Updated November 2, 2023
Introduction to SQLMap in Kali Linux
SQLMap is an open-source penetration testing tool that is specifically designed for detecting and exploiting SQL injection vulnerabilities in web applications. SQL injection occurs when attackers manipulate an application’s SQL query with malicious SQL code.
SQLMap helps security professionals, ethical hackers, and penetration testers identify and exploit such vulnerabilities in web applications.
It’s essential to note that SQLMap should only be used for ethical and legal purposes, such as penetration testing, security assessments, and ensuring the security of your web applications.
Unauthorized or malicious use of SQLMap on systems you do not own or have explicit permission to test is illegal and unethical. Ensure you have the proper authorization before using security testing tools like SQLMap.
Table of Contents
- Introduction
- Prerequisites
- SQLMap Package Description
- Key Features
- Tools Included in the SQLMap Package
- SQLMap Usage Example
- Advanced Techniques
Prerequisites
Before using SQLMap for penetration testing or security assessments, there are several prerequisites you should consider to ensure responsible and legal use of the tool.
Let’s see some of them:
Ensure Kali Linux is installed and up to date.
First of all, Verify that Kali Linux is installed on your computer. Kali Linux is a Debian-based Linux distribution specifically designed for penetration testing and security assessments.
You can download and install Kali Linux from the official Kali Linux website.
System Update (Recommended): Ensure your Kali Linux system is up to date by running the following commands:
sudo apt updatesudo apt upgradeBefore using Kali Linux for security testing, make sure it’s up to date. You can update Kali Linux using the above commands.
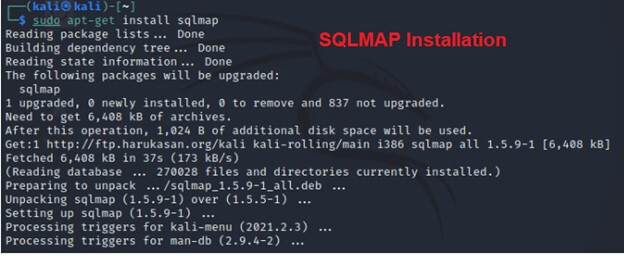
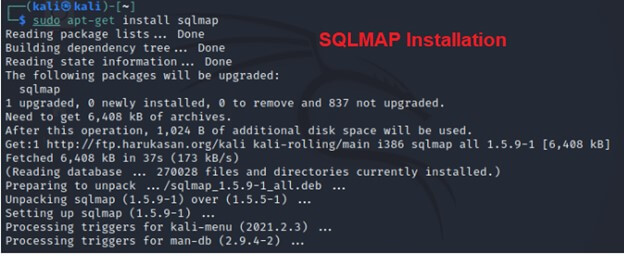
Install SQLMap if not already installed.
Install SQLMap if it’s not already installed. You can install SQLMap using the package manager (apt) or download it from the official GitHub repository.
Command
sudo apt install SQLMapSQLMap Package Description
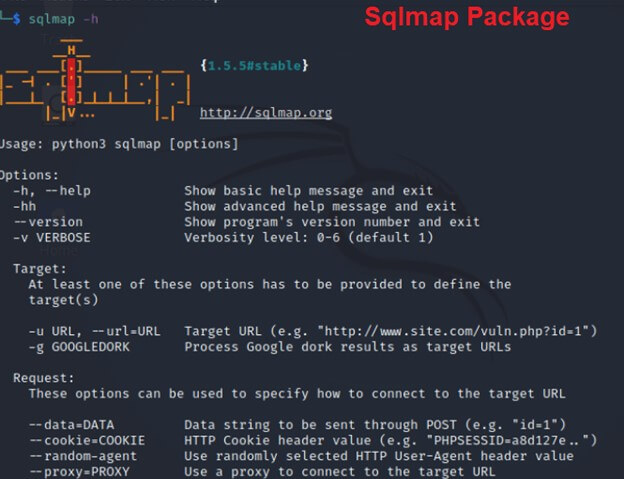
The “SQLmap” package is a popular and widely used tool in cybersecurity and penetration testing. Here’s a description of the “SQLmap” package:
Package Name: SQLMap
The package name for SQLMap is indeed “SQLmap.” You can use this package name to install SQLMap on your system using package managers like apt or yum if available in your system’s repository.
Description:
- “SQLMap” automates the detection and exploitation of SQL injection vulnerabilities.
- It assists security professionals and ethical hackers in assessing the security of web applications by probing for potential weaknesses that could lead to unauthorized access or data leakage.
- With its comprehensive feature set, SQLmap simplifies the identification and resolution of SQL injection issues, enhancing the security posture of web applications and underlying databases.
- This tool is a critical asset in security testing and vulnerability assessment for ethical and responsible hacking practices.
Please note that package availability may vary depending on your Linux distribution, so you might need to adjust the package management commands accordingly if you’re using a different distribution.
sudo apt-get install sqlmapKey Features
SQLMap automates the detection and exploitation of SQL injection vulnerabilities in web apps and databases with its powerful features. Some of its key features include:
- Automatic Detection: SQLMap automatically identifies SQL injection vulnerabilities in web applications, saving time and effort in the testing process.
- Database Support: It supports various database management systems, including MySQL, PostgreSQL, Oracle, Microsoft SQL Server, and more.
- Interactive Mode: SQLMap offers an interactive command-line interface for more fine-tuned control over the testing process.
- Enumeration and Dumping: It can perform reconnaissance by enumerating databases, tables, and columns and extracting data from them.
- Fingerprinting: SQLMap can determine the type and version of the database management system, which aids in crafting effective attacks.
- Batch Mode: Allows for automated scanning of multiple targets by specifying a list of URLs or targets.
- Tamper Script Support: SQLMap supports tamper scripts, which can be used to evade web application security mechanisms and WAFs.
- Data Exfiltration: It can retrieve, modify, or delete data in a database, depending on user permissions, for effective testing.
- Post-Exploitation: SQLMap can be used for post-exploitation activities, such as command execution on the target system.
- Blind SQL Injection: Supports both time-based and boolean-based blind SQL injection attacks.
- Custom Headers and Cookies: You can specify custom HTTP headers and cookies for testing, making it more versatile.
- Session Management: SQLMap can maintain session cookies for authenticated testing.
- Proxy Support: It can be configured to route traffic through a proxy for anonymity or to bypass security controls.
- Reporting: Generates detailed and customizable reports about the vulnerabilities it discovers.
- Database Management: SQLMap includes basic functionalities like creating, deleting, and listing databases.
- Integration: Other tools and scripts can integrate with it for a more complete testing workflow.
- WAF Detection: SQLMap can identify the presence of Web Application Firewalls (WAFs) and suggest potential bypass techniques.
- RegEx-Based Testing: Allows for customized regular expressions for better testing precision.
These features make SQLMap a versatile and essential tool for security professionals and ethical hackers in identifying and mitigating SQL injection vulnerabilities and enhancing the security of web applications and databases.
Tools Included in the SQLMap Package
The “SQLMap” package primarily focuses on the SQL injection testing and exploitation tool. However, it may include auxiliary and support tools to enhance its functionality. The main SQL injection testing and exploitation tool.
- SQLmapapi: A RESTful API server for SQLMap, which allows you to interact with SQLMap programmatically.
- conf: The configuration file for SQLMap where various settings can be defined.
The package contents might change, and additional scripts or tools may be included or removed in newer versions. To get the most up-to-date information about the tools included in the SQLMap package, you can check the package documentation or the official SQLMap website or repository.
Example of SQLmap in Kali Linux
In this example, we’ll assume that you have already installed SQLMap on your Kali Linux system and are conducting this test against a target website for which you have explicit permission to test.
Please ensure you have the necessary authorization and follow ethical guidelines when performing security assessments.
sqlmap -u "http://target-website.com/page.php?id=1" --dbsIn this command:
- sqlmap: Launches the SQLMap tool.
- -u “http://target-website.com/page.php?id=1”: Specifies the target URL with a parameter that may be vulnerable to SQL injection. It would be best if you replaced this with the actual URL you want to test.
- –dbs: This option instructs SQLMap to enumerate the available databases on the target server.
Running this command initiates the SQL injection test. SQLMap will send various payloads to the specified URL parameter to detect any potential SQL injection vulnerabilities. If a vulnerability is found, SQLMap will enumerate the available databases on the server.
Here’s a breakdown of the steps you can expect to see as SQLMap runs:
- SQLMap will automatically analyze the target URL for possible SQL injection vulnerabilities.
- It will attempt different SQL injection techniques to identify any potential vulnerabilities.
- If a vulnerability is detected, SQLMap will proceed to enumerate the databases on the server.
- SQLMap will provide a list of the available databases, and you can then explore them further.
Remember that SQLMap is a powerful tool, and using it without proper authorization can be illegal and unethical. Always ensure you have explicit permission to test the target and adhere to ethical hacking practices. Additionally, SQLMap provides many more options and capabilities for fine-tuning your tests, which you can explore in its documentation and help menu.
Advanced Techniques Used in SQLmap Kali Linux
SQLMap offers advanced techniques for evading security mechanisms like Web Application Firewalls (WAFs) using tamper scripts. These scripts modify the SQL injection payloads sent to the target in a way that may bypass security filters. Here’s how to use tamper scripts and evade WAF protections with SQLMap:
1. Tamper Scripts
Tamper scripts are essential for modifying SQL injection payloads in a way that can bypass security filters and evade detection. SQLMap has several built-in tamper scripts, and you can create custom scripts to suit your needs. To use tamper scripts, follow these steps:
Specify the tamper script(s) using the –tamper option. You can use multiple tamper scripts separated by commas.
sqlmap -u "http://target-website.com/page.php?id=1" --tamper=space2comment,randomcaseSQLMap will apply the selected tamper script(s) to the payloads it sends to the target, potentially evading security filters.
Experiment with different tamper scripts to determine which ones are effective for a particular target.
2. Evading WAF Protections
WAFs are designed to block SQL injection and other malicious traffic. SQLMap can help evade WAF protections by using tamper scripts and other techniques. Here are some strategies:
Use Effective Tamper Scripts: Certain tamper scripts, like space2plus or randomcase, can be more successful in bypassing WAFs.
sqlmap -u "http://target-website.com/page.php?id=1" --tamper=space2plusMultiple Tamper Scripts: Combining multiple tamper scripts can increase the chances of evading the WAF.
sqlmap -u "http://target-website.com/page.php?id=1" --tamper=space2plus,randomcase- Custom Tamper Scripts: If built-in tamper scripts are ineffective, you can create custom tamper scripts tailored to the specific WAF’s filters.
- Remember to conduct security assessments responsibly and with proper authorization. Unauthorized testing can lead to legal consequences and ethical concerns. Adhering to ethical hacking guidelines and respecting the terms of service and laws is crucial.
Using these advanced techniques, you can enhance the effectiveness of SQLMap in identifying and mitigating SQL injection vulnerabilities while working within ethical and legal boundaries.
Conclusion
SQLmap is a valuable tool in cybersecurity and penetration testing, particularly for identifying and mitigating SQL injection vulnerabilities in web applications and databases. Its automation capabilities, a wide range of features, and advanced techniques, such as tamper scripts for evasion, make it a powerful asset for security professionals, ethical hackers, and penetration testers.
Recommended Articles
We hope that this EDUCBA information on “SQLMap in Kali Linux” was beneficial to you. You can view EDUCBA’s recommended articles for more information.