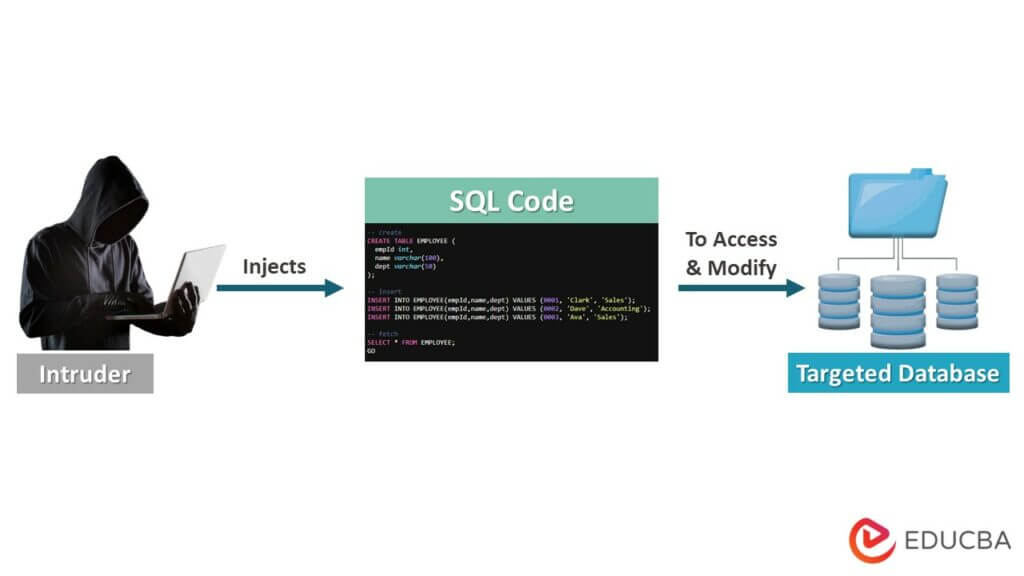
What is SQL Injection?
SQL injection is a security flaw that grants an intruder access to add, delete, or modify the application’s database and queries.
For instance, in November, a SQL injection was found in the Zendesk CRM by a few Varonis Threat Labs researchers. Due to the vulnerability, the intruder would have had access to over 100,000 customer data. The issue was, however, resolved within a week with the help of those researchers.
SQL Injection is a dangerous programming model that, if injected into your database code, can destroy the database. The hacker can also cause a database D-O-S (Denial of Service) attack. The intruder can alter any information that the application has access to or the data of other users. In most cases, it enables an intruder to access a database they would not typically be able to access.
Key Highlights
- SQL injection or SQLi is a popular attack method that uses malicious SQL code to manipulate backend databases and access secure data.
- There are three types of SQLi options: in-band, inferential, and out-of-band.
- Intruders use SQL queries and commands like data retrieval, update, removal, and modification to carry out these attacks.
- The SELECT statement is the most popular and common option to detect vulnerabilities.
How to Create an SQL Statement?
A structured query is used to accomplish an SQL statement by triggering the desired answer. The attacker needs the response to comprehend the database design and gain access to the application’s safeguarded data. SQL injection can be carried out by an attacker using the following techniques:
1: A Constant True SQL Statement
- A hacker uses a SQL statement that is perpetually true to carry out a SQL injection.
- As an illustration, the hacker chooses 1=1 rather than just inputting the “false” data because it is a statement that is always true.
2: Batched SQL Injection
- A group of SQL statements are combined into a batch SQL injection and are separated by semicolons.
- However, it must be kept in mind that if the SQL commands (the statement that appears after the semicolon) are legitimate, this strategy can function properly.
Real-Life Examples
Example #1: GhostShell Attack
The most renowned cyber attack by the Ghost gang was taken over, where they claimed to leak around million user accounts from 100 websites worldwide. Their main targets were government agencies, banks, manufacturing companies, and banks. The attackers employed the famous SQLmap tool for this attack and hacked databases that included around 30,000 records.
Example #2: 7-Eleven Breach
On August 8, 2022, a group of hackers attacked the retail chain of 7-Eleven, where they stole 130 million credit card numbers. It was confirmed that each customer loses around $600 million and the hackers did this via the newly launched payment app of the store, i.e., 7pay. After this incident, the store was closed for a long time, and people were instructed to block their cards.
Example #3: HBGary Breach
The US Security firm HBGary was attacked by the Anonymous Team, which breached HBGary’s networks and posted executive email archives on file-sharing networks. Additionally, the group hacked the company’s website and replaced it with a message claiming that it was disclosing Barr’s (Aaron Barr, the CEO) findings independently because it was certain that Barr’s findings were incorrect.
More Examples
Example #1
Say you have entered “100 OR 1=1” when submitting the query. The response that it will return will be in the table details.
“OR” “=”
You certainly notice a similarity with the above SQL injection method. An attacker will insert “OR” “=” in the query box. It is a malicious code and will dig deeper into the application.
Example #2
A hacker wants to retrieve a user’s login ID and password from the SQL database. The hacker will type “OR=” in the user ID and password section. Since this is a valid SQL statement, the hacker will have access to the user ID and password without any trouble.
Example #3
If someone is trying to delete a table named SUPPLIER from the database, S/he has to enter the command “105; DROP TABLE SUPPLIER,” and the statement that follows the semicolon will be dropped (or deleted) from the database.
How to Detect Vulnerabilities?
There are three types of queries available to detect SQL Injection.
#1 SELECT statement
- The Select Query statement fetches specific information or data from the database.
- If you want to retrieve data from the SQL database, you must use the SELECT statement.
- One uses the SELECT statement commonly for information search purposes or to view a specific profile in a table.
- In some scenarios, one uses the SELECT statement for login purposes.
#2 INSERT statement
- The Insert Query statement is used to insert data or info into the database.
- If you want to include a new row in the database table, you need to use the INSERT command. They are frequently used whenever a program makes a new order, includes new data in the audit log, or creates a new account for the user.
- If you are creating a new user account, you need to use the INSERT statement to submit the data into the database.
The syntax:
- INSERT INTO accounts (user_name, password, signature) VALUES (‘xxx,’ ‘yyy,’ ‘zzz’);
- Mention the account’s name in the “accounts” section and observe the “(user_name, password, signature)” section of the syntax.
- These are the names of the columns featured in the database. If the database does not feature the columns’ names, you need to add them.
- Move to the section that precedes VALUES, “(‘xxx,’ ‘yyy,’ ‘zzz’)” and insert the username for ‘xxx,’ password for ‘yyy,’ and a signature for ‘zzz.’
- Due to the high risk, keeping the application secured is important. It can be hacked by specially designed input and injecting random values in the database.
- Use the user_name parameter: (‘name,” pass,” sign’)- to examine the vulnerability of the data.
- After finding the location of the injected data in the database, it becomes easy to modify the data or even extract it by altering the input.
#3 UPDATE statement
- The Update Query statement is used to alter or modify the content of the database.
- One uses the UPDATE statement to manage the proceedings if one wants to alter the existing rows in a database table.
- One uses the UPDATE statement commonly to modify passwords, change the value quality on a line, or even update contact details.
- The UPDATE statement is very similar to that of the INSERT statement but with a slight difference, the use of the WHERE clause that indicates the rows in the table to be updated.
- For example, UPDATE Contacts SET Phone Number=”569853264″ WHERE Name = ‘Sandy’
Types of SQL Injections
#1 In-band SQLi
The attack and the resulting gathering are made using the same communication channel for the attacker. One of the most prevalent kinds of SQLi attacks is the in-band SQLi due to its simplicity and effectiveness.
Error-Based Injection
- In this type of injection, the hacker will try to insert a spam query into the table’s fields, and the output will display an error, indicating a problem in the database or SQL syntax.
- This technique is considered the simplest and easiest of the two to detect the location of the SQL injection.
Union Based Injection
- This method uses the SQL operator UNION, which combines many select statements produced by the database into one HTTP response.
- The information in this response might be useful to the attacker.
#2 Inferential SQLi
Also known as Blind Based Injection, the hacker injects the malicious syntax or query into the SQL database table. Here, the output message will only indicate that the syntax is incorrect. Through this approach, the hacker will try to retrieve some information by verifying true or false statements when querying.
Boolean
- The attacker issues a query to the SQL database to force the application to deliver a result. Based on the pattern of the inquiry (true or false), the outcome will change.
- Depending on the outcome, the data in the response server will change or remain the same. After then, the attacker can determine whether the output is true or false.
Time-based
- The database must wait (for a time in seconds) before responding to the attacker’s SQL query, which is sent to the database. Depending on how long it takes the database to answer, an attacker can determine the validity of the query.
- Depending on the outcome, an HTTP reply will either be generated immediately or after a short delay. Thus, the attacker does not need to rely on information from the database to determine whether the message returned true or false.
#3 Out-of-band SQLi
Out-of-band SQLi is carried out when a hacker cannot utilize the same channel to retrieve information or attack the server.
- One can also use it with slow and unstable servers.
- These strategies rely on the server’s ability to send HTTP and DNS requests to send data to an intruder.
How to Prevent SQL Injection?
- The user/developer needs to filter every input from the program, including single quotes (likely to hold malicious elements), as well as login forms and other web input forms.
- Next, turning off the database error visibility on the site is a better idea to prevent further damage.
- Remember, database errors can prove harmful in giving away information regarding the database.
- One uses WAF, or Web Application Firewall, to eradicate online threats and filter out SQL injection attacks. It first detects a suspicious input. Then it cross-verifies the same with the concerned IP data before deciding whether it’s malicious, and then the IP can only block the input if it has a bad user interface.
Final Thoughts
Although SQL injection is primarily recognized as a website attack vector, it may be used to target any kind of SQL database. When it comes to vulnerabilities in SQL databases, detecting them is of real importance. Without detecting the vulnerabilities in the database, it will become impossible to move on with the identification process.
Frequently Asked Questions (FAQs)
Q1. What is an injection in SQL?
Answer: SQL injection is known as a code injection technique that might corrupt or destroy any database. It is one of the most commonly used web hacking techniques used by hackers. In this entire process, the hacker places malicious code in the SQL statements through web page input.
Q2. What are the three types of SQL injection?
Answer: Typically, SQL injection is divided into three categories: In-band SQLi (Classic), Inferential SQLi (Blind), and Out-of-band SQLi. One can classify the types of SQL injections on the basis of methods used to gain access to backend data and the potential damage.
Q3. What can a hacker do with the SQL injection process?
Answer: The potential outcomes if the application has a SQL injection vulnerability include Possible authentication bypass, the confidentiality of the data could be compromised, and an attacker can modify and delete database data and remove entries.
Q4. Which tool is best for SQL injection?
Answer: SQLMAP is an open-source SQL injection tool and is popularly used SQL injection amongst folks. This tool helps to make it very easy to exploit the SQL injection vulnerabilities of any web application and gain access to the database server.
Recommended Articles
This article is a guide to SQL Injections. We discuss its definition, examples, queries, and more. Read the following articles to learn more,