Introduction to Phishing and Pharming
The method of social engineering where hackers send emails and messages to people in the form of emails from reputed companies to make them believe and share personal information is called Phishing. This also makes the hacker deploy harmful malware or viruses into the system, which makes the victim’s system useless. The practice of making internet users redirect to another website that looks like a valid website and makes the users share sensitive information is called Pharming. This can be done by changing the host’s file or by checking the weakness of the DNS system of the host system.
Table of Contents
What is Phishing?
Phishing is one of the methodologies adopted to achieve unlawful acts. It is an illegal procedure through which a hacker or any person secretly acquires information about confidential/sensitive subjects. It may be a username, password, credit/ debit card details, etc. Phishing is a part of cybercrime, and the intention of acquiring sensitive information is malignant.
The aim of committing such a crime is to victimize consumers by sending fraudulent emails containing the virus. As such, the phisher sends bulk emails that may seem authentic in the first instance. For example, people may get emails about a lottery prize from a bank or other renowned company. The sender usually asks for personal information such as name, address, phone number, email, and, most importantly, bank details. Of late, phishing has become quite common, victimizing several people in the process.
However, various measures have been undertaken to curb this cyber threat, such as making people aware and cautious of such fraud emails and not trusting them blindly, offering to train users to tackle such incidents, improving the websites’ security level legislation, and much more. Phishing comes within the social engineering category; it has also targeted social media websites like Facebook, YouTube, and Twitter to swindle users.
Advent of Phishing
The first primary target of the phishers was American Online Accounts (AOL). They wanted to get information on the accounts secretly. They introduced themselves as AOL employees to their target victims and sent messages requesting the latter to submit their login and password with that intent in mind. Once the user fell into their trap, it became easy to fulfill their evil intention. They got engaged in several cyber-related crimes, such as sending bulk spam emails, software containing malware, etc.
Taking a step further in this process, they resorted to illegal activities like encouraging internet users to browse fake websites whose URL was not legitimate. They also took undue advantage of the grammatical and spelling mistakes. With time, the phishing business became technologically advanced, making it challenging for the authorities to detect errors. But it is a matter of grave concern that several governmental and military websites are targeted through phishing to steal confidential information.
Unfortunately, many financial institutions such as banks, renowned and trusted companies, and even governments incur huge yearly losses due to illicit phishing activity. The loss is estimated to be in the billions.
Categorization of Phishing Techniques
Some of the essential types of phishing techniques include-
1. Whaling
This activity is whaling when the phishers or hackers aim to target the senior executives and other high-ranked officials of a well-reputed company, such as the Chairman, CEO, or CFO. A simple example can explain it. It is usually written to the higher authorities with a false claim regarding the company’s concern. The content of the email is typically some customer complaint. The hackers can send a URL and request the authority to download and install the software so that they can view the subpoena. Therefore, the company management needs to be very careful about such emails to not get into a trap in the net. This can lead to financial loss for the company.
2. Filter Evasion
Filter Evasion is a new method developed by Phishers to perpetuate their unlawful activity. In this procedure, they use pictures or photos rather than text. This technique is a challenge to the anti-phishing authorities who identify fraudulent emails or spam. However, advanced technology has introduced medicines to combat such diseases. It has launched a more modernized version of anti-phishing filters to detect such images using Optical Character Recognition (OCR). On the other hand, these authorities also use Intelligent Word Recognition (IWR) to identify cursive and various handwriting styles. However, this technique will not substitute OCR.
3. Spear Phishing
These types of phishing techniques intend to attack individual users or even a company. It has been one of the most common phishing processes in recent times. Hackers aim to gather the personal information of persons through fake emails. However, beware of any such email from an unknown person.
4. Link Manipulation
This is a technical scam wherein a fraud email will ask to click on a link to a spoofed website of any bogus company. However, after opening the URL, there is no doubt that it is a phishing website. Hackers conduct this illegal act by using wrong spellings on the link or using a false sub-domain to trap their prey. When viewing a particular page on a site, it seems like viewing the specific page, but the truth is that it links with some other website. In addition, emails that show where the link will take you further. The phishers also take advantage of some international domain names, which take time to identify.
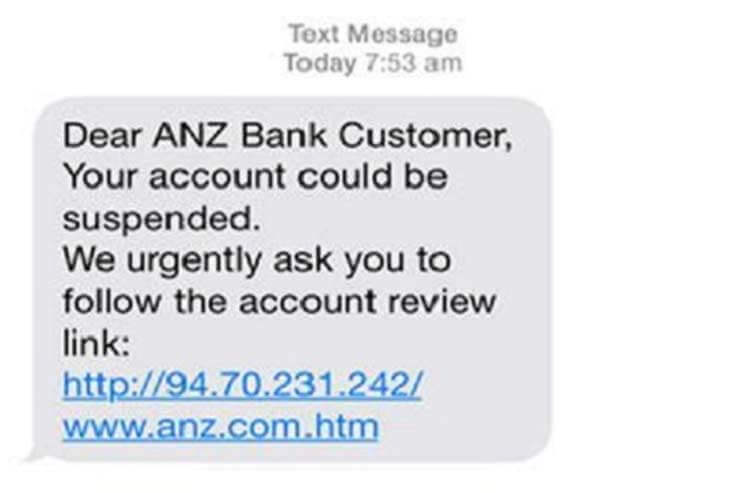
5. Phone Phishing
Phone phishing techniques are another standard methodology that does not require any internet connection to commit a crime. The phishers identify their victims and then make fake phone calls, especially posing as bank managers or staff. They usually fool people by saying that their bank account has developed a problem, and they ask for complete banking info, including the credit or debit card details and PIN. They get an IP during the conversation and then take out all money from the person’s account, leaving him bankrupt. Therefore, never share your banking details with an unknown person over the phone.
6. Clone Phishing
As the name suggests, it is a cyberattack on the website conducted with the help of an email or any link. The phishers often target a genuine email that was previously active. They develop an identical clone of that mail or link and replace it with the pirated version containing malware. Now, they will send an email to their target from the forged ID, and the user presumes it is an original email. The hackers usually use a computer or laptop infected with the virus to complete their malicious intentions.
7. Website Forgery
The phishers use high technology, such as JavaScript, to achieve their motive. This helps them to change the address bar. It also allows them to substitute pictures from the authentic website as well. They can close the genuine site and develop their site using the same valid URL. With technology becoming more advanced, they have adopted newer methods such as Cross Script Scripting, which directly attacks the original website. This poses significant difficulties for the anti-phishers to control such illegal activities. The concern is even more critical because users must sign in to their bank or service’s page. PayPal has faced a lot of problems with web forgery in the past.
8. Covert Redirect
Covert Redirect is one of the phishing techniques through which these shrewd hackers get personal information from the victims when they later visit their fake websites. However, this can only happen if the user authorizes the site app. When you do so, the phishers get a token from the accessibility to confidential information becomes very easy.
Aside from these phishing techniques, the phishers can adopt some other methods too. These include Evil Twins, Tab nabbing, and getting bank details information.
What is Pharming?
In simple terms, it is a type of cybercrime in which the web traffic of a simple site transports to another malicious website. This kind of cyber attack is more associated with technical aspects. In this case, the alteration of the host’s file happens on the victim’s computer. The attackers can also take advantage of the drawbacks of DNS server software. Pharming becomes easier if the attackers access a computer system that is not secure. Therefore, computers installed at home can be easily targeted compared to corporate systems with a protected server.
Phishing is derived from the word ‘fishing’; pharming is derived from farming. According to the latest reports, phishing and pharming have become significant threats to the internet and cyber world. Pharming victimizes online businesses such as E-Commerce websites and transactions via the Internet. However, initiation of a few steps happened to curtail this malignant act by introducing antivirus software or spyware removal, but, unfortunately, nothing proved to be effective.
Home-Based Servers are Easy Targets
Home-based servers and personal computers are vulnerable and unprotected; thus, they quickly come on the radar of the pharmers. Several techniques are used, which the hackers can pharm, but the most common is using the DNS cache poisoning method. The website’s name converts into digits that are decoded with the machine’s help. For instance, www.product.com becomes a series of numerical like 180.172. 1.1. This can pose more significant threats. One primary reason that makes desktops easily vulnerable is their poor administration.
However, the concern does not end here; some other vital drawbacks must be highlighted. Often people compromise on the local network router. Routers have a significant role to play by considering cybersecurity. But if it is not a genuine router, it can spoil the DNS information. In such a circumstance, the pharmer will take control of the DNS server, and all data will be passed on to this illegal or bad server.
Another problem that may prop up is the change of firmware by the routers. In that scenario, the authorities will find difficulty in tracing the attacker. This is because the replaced firmware resembles the same, including the administration page, settings, etc.
A Few Incidents of Pharming
A few significant pharming instances of attacks reported came into the limelight. One such incident was hacking a New York ISP’s domain name linked to a website in Australia. However, reporting of no such financial loss happened. It occurred in January 2005. In yet another incident, the lodging of a complaint against a bank in Mexico that indulged in pharming activity. The complainant was Symantec, and it took place in January 2008. According to the report, DNS settings were altered from a customer’s computer at home after getting an email from Spain.
Difference Between Phishing and Pharming
Below are the differences between phishing and pharming:
| Aspect | Phishing | Pharming |
| Definition | A cyber attack where attackers impersonate legitimate entities to trick victims into revealing sensitive information, such as passwords or credit card numbers. | A cyber attack involves redirecting or tampering with the Domain Name System (DNS) to send victims to fraudulent websites, often without their knowledge. |
| Attack Vector | Typically conducted through fraudulent emails, websites, or messages that mimic trusted organizations or individuals. | Manipulates DNS servers or uses malware to redirect users to malicious websites even when they enter the correct website URL. |
| Targeted Data | Attackers aim to steal personal or financial information, such as login credentials, credit card numbers, or Social Security numbers. | Primarily used to compromise website traffic and steal sensitive data entered by users on spoofed websites. |
| User Awareness | Often relies on social engineering to trick users, so user awareness and vigilance play a significant role in defense. | Users may not be aware of the attack, as they are directed to fraudulent websites without any indication. |
| Mitigation | Users can protect themselves by verifying email senders, avoiding suspicious links, and being cautious about sharing sensitive information. | Requires DNSSEC (Domain Name System Security Extensions) to prevent DNS tampering and strong network security measures. |
| Examples | Phishing emails that ask users to click on fake login links or enter sensitive information on fraudulent websites. | DNS cache poisoning attacks or malicious DNS server redirection that leads users to fake websites. |
| Common Countermeasures | Email filters, anti-phishing software, two-factor authentication, user education, and awareness programs. | DNSSEC implementation, network monitoring, regular DNS server audits, and using secure DNS resolvers. |
Conclusion – Phishing and Pharming
Phishing and pharming pose serious threats to cybersecurity, and combating these crimes requires the development of new software and techniques. However, it’s crucial for people to remain alert, aware, and cautious when using the internet, as protecting one’s information and preventing financial loss is of utmost importance. To stay safe, users should verify any emails they receive and ensure that the URL addresses begin with HTTPS. Users can also utilize anti-phishing and fraud monitoring tools to stay protected against online attacks.
Frequently Asked Questions(FAQs)
Q1. How do I recognize a phishing email?
Answer: Look for suspicious email addresses, misspelled URLs, generic greetings, urgent personal information or money requests, and poor grammar or spelling. Be cautious of unexpected emails from unfamiliar senders, and always verify the sender’s identity before clicking on any links or downloading attachments.
Q2 How can I protect myself from pharming attacks?
Answer: Ensure that your computer’s antivirus and anti-malware software is up to date. Regularly check your DNS settings to ensure they haven’t been tampered with. Use a trusted DNS service or DNSSEC (DNS Security Extensions) to enhance DNS security.
Q3 Can firewalls protect your system from pharming?
Answer: Antivirus software or firewalls can help detect malicious code in the system. It also warns the user before visiting insecure websites.
Recommended Articles
We hope that this EDUCBA information on “Phishing and Pharming” was beneficial to you. You can view EDUCBA’s recommended articles for more information.