Updated March 16, 2023

Introduction to Cyber Security Challenges
Cyber Security Challenges have been the national security in today’s world, organizations ranging from small to large enterprises, government and private universities, hospitals, all prone to cyber-attacks from across the globe. In addition, in our quest to deal with newly emerging threats, we often face challenges that one must deal with to secure their territory.
You might have recently heard that Wikipedia was taken offline (Sep 9, 2019) in regions of Middle East countries because it was attacked with a massive and broad distributed denial of service attack. So if the bad guys don’t spare a free education, what less can we expect from them?
A crisp which details out that why Cyber Security Challenges should be the top priority of top organizations is pointed below.
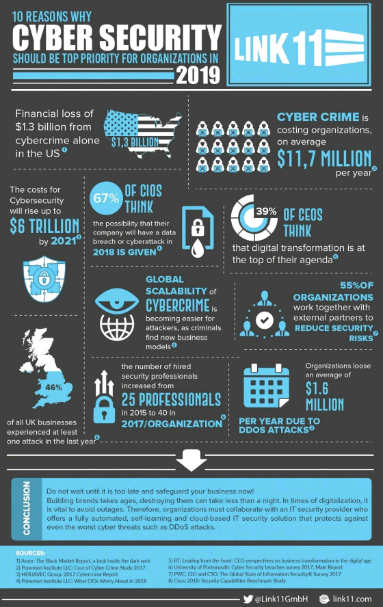
Main Cyber Security Challenges
Following are main cybersecurity challenges in detail:
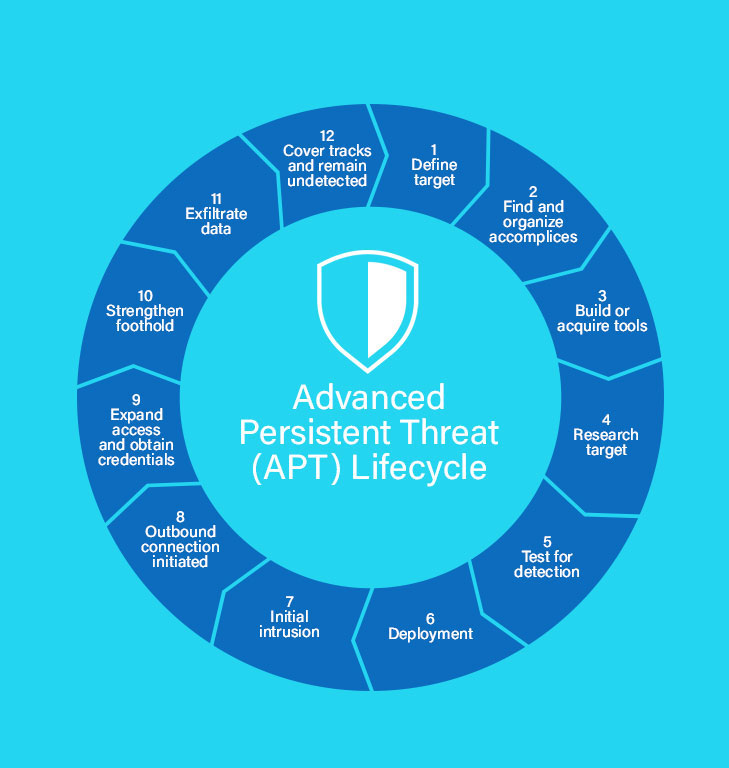
1. Advanced Persistent Threats
- Advanced persistent threats go the stealthy way around to penetrate systems and servers and stay there for a longer time without getting noticed/detected by anybody.
- They are designed specially to mine highly sensitive information, and these days, many organizations fail to protect themselves from advanced persistent threat attacks.
- The APTs are not like typical malware, they are designed specially to serve a purpose, and in other words, they are being made for targeted attacks. For example, below is one depicted lifecycle of advanced persistent threat.
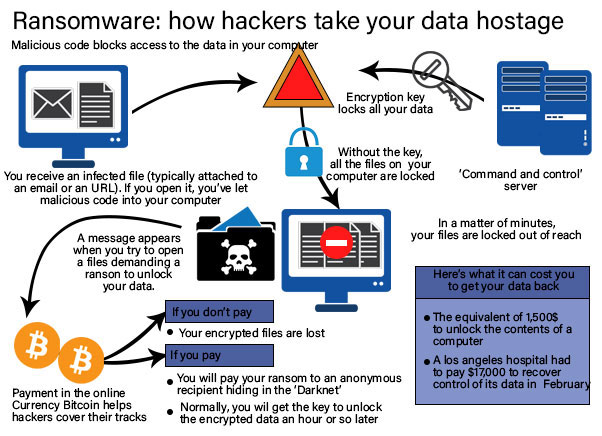
2. Evolution of Ransomware
- The last few years have seen a widespread rise in Ransomware attacks. Ransomware can also be classified as one type of APT attack where malware penetrates inside your system, and as the days pass, it starts to encrypt all of your files slowly.
- Finally, all the files on one’s system get locked, and a ransom is being demanded, usually in the form of bitcoin (Because it is hard to track it down).
- Once the payment is made, a decryption key is being provided by hackers, using which all the data can be decrypted back, and the access is returned.
- There can be cases where a hacker with a very bad mindset may take all the demanded money but still don’t give the decryption key.
- Ransomware is the bane of cybersecurity, data professionals, IT, and executives. Below is an anatomy of a Ransomware attack.
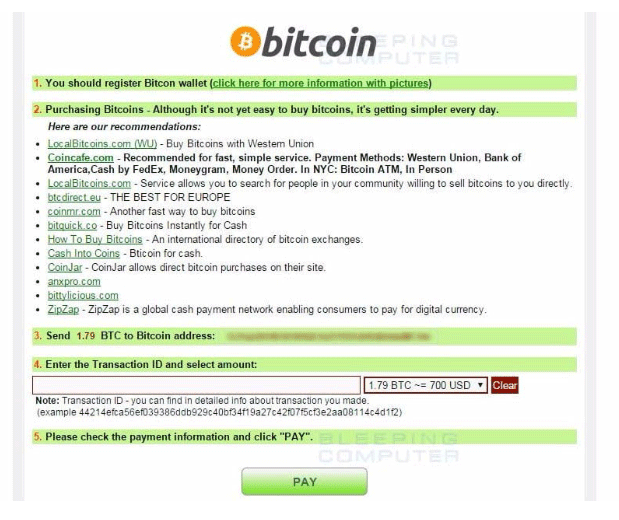
Some of the examples of Ransomware are Cryptolocker, Bad Rabbit, Wanna cry, Goldeneye, Zcrypter, Jigsaw, Petya, etc.
3. IoT Threats (Attacks through compromised IOT devices)
- IoT stands for the internet of things. The IoT is a system of interrelated computing, digital, mechanical devices that can transmit data over a network without the need of any human to human and human to computer intervention.
- All of these IoT devices have a unique identifier that identifies the device through a unique code. In today’s world, every digital device that we use can be connected with a network, and yes, it is happening in almost all the parts of the globe.
- By doing this, we have control over the majority of appliances and devices from a single point of operation- let’s say your cell phone. In today’s world, you can use your cell phone to turn off the lights, operate Alexa, operate refrigerator and washing machines, etc. So, many consumer devices are now interconnected.
- In other words, if you access one device, you’ve accessed them all, and this leads to an increased risk of attacks and gaps in securities.
- There could be many reasons for these gaps, such as insecure web interfaces and data transfers, lack of knowledge about security, insufficient authentication methods, insecure wifi, etc. Below is a map that shows threats related to the Internet of things.
4. Cloud Security
- There is fear, and many organizations are unwilling to put their data on the cloud, and they want to be reserved for a time unless it is ensured that the cloud is a highly secure place and matches with on-premise security standards.
- The main reason is, big organizations have their own Data centers. They have full control over it; the data is located at their sites and their network(i.e. the internal network). In contrast, in the case of the cloud, the data no longer stands at the company’s own Data centers, and also, the network becomes external, which poses a risk.
- Few issues lead to cloud attacks, few of them are – Cloud misconfigurations, Insecure APIs, Meltdown and Specter vulnerabilities, Data loss due to natural disasters, or human error.
5. Attacks on Cryptocurrencies and Blockchain Adopted Technologies
- It’s not so long that technologies like cryptocurrencies and blockchains have started to being implemented.
- As these technologies just have crossed their infancy level and there lies a great path for their evolution, so adopting these technologies by companies but not implementing the appropriate security controls is a big threat; in the first place, they might not be aware of the gap itself.
- So it is being advised to understand the security controls before implementing these technologies. Some of the attacks made are the Eclipse attack, Sybil attack, and DDOS attack.
6. Attacks Designed with the help of AI and Machine Learning
No doubt the big data from all over the world is being fed to AI systems for various purposes, and it helps us to make our decisions. While this is a good side of it, there can be a bad side as well. Hackers can also use AI and Machine Learning to design innovative solutions for performing out more sophisticated attacks.
This was all about the challenges to cybersecurity, and we have talked about major challenges, but we might also be interested in knowing information on steps to cybersecurity.
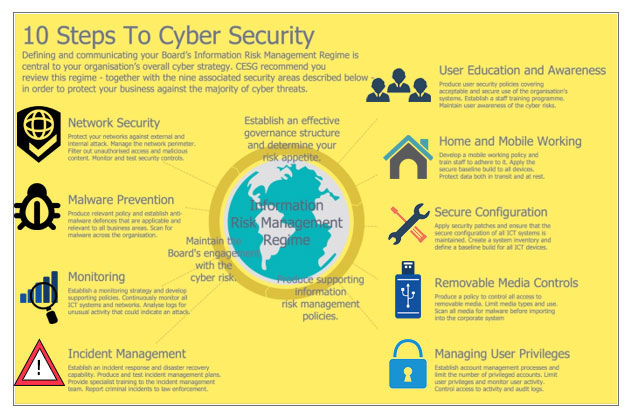
Recommended Articles
This is a guide to Cyber Security Challenges. Here we discuss the introduction and main cybersecurity challenges, including advanced persistent threats, evolution of ransomware, IoT threats, cloud security, attacks on cryptocurrencies, and blockchain adopted technologies. You may also look at the following articles to learn more –


