Updated March 14, 2023
Introduction to Symmetric Key Encryption
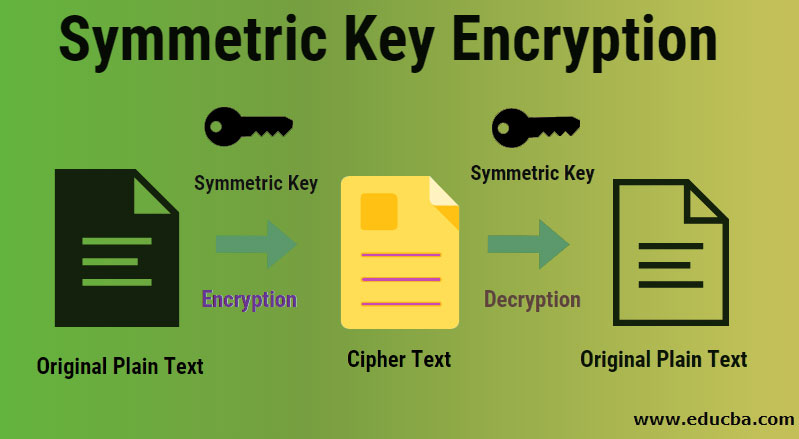
A symmetrical key is used for encrypting and decrypting electronic information in cryptography. It means you must have the same key used to encrypt information to decrypt and decrypt the information to encrypt. This is because data are translated to a type using symmetric encryption algorithms, which can not be understood by anyone who has no secret key to decrypt it. Thus, the symmetrical algorithm provides a high level of security.
Understanding
- As we have already mentioned in the symmetric key encryption technique, only a single key, also known as the secret key, is used to encrypt and decrypt electronic information. Therefore both the entities which are participating in the process of symmetric key encryption must make sure that a single key is shared among both the groups of parties. This one is a less reliable method than asymmetric key encryption as this technique uses both the public and the private keys for decryption and encryption purposes.
- In the case of symmetric key encryption, the secret key that both the parties possess can be anything such as a passcode or a password. It can also be the random string of letters or numbers generated by a secure random number generator (RNG). This RNG is used for critical applications such as banking based encryption, where the symmetric keys must be developed by making use of RNG, which is also an industry-wide standard such as FIPS 140-2.
How does Symmetric Key Encryption make Working so Easy
The symmetric key encryption does not have to rely on separate private and public keys, as is the case with asymmetric encryption technology. Instead, it makes use of a simple shared key that can be used for the transfer of the data and information by making use of encryption and decryption algorithms. Therefore there is comparatively a lesser complexity involved with the decryption of a single key than to decrypt two keys, and therefore it is an easier approach to work with.
What can you do with Symmetric Key Encryption?
This can be used in the case of RC6, DES, RC5, AES, RC4, Blowfish, Twofish, CAST5, Serpent, 3DES, Skipjack, IDEA, Safer++, etc. This is generally used to achieve more cryptographic primitives than normal or basic encryption techniques. When you encrypt a message, you cannot guarantee that the message content will not be changed when encrypted. Therefore, a message authentication code is added along with the ciphertext to ensure that the changes made to the ciphertext will be well efficiently noted by the receiver side.
Advantages
Given below are the advantages mentioned:
- Extremely secure: This algorithm is extremely secure as only one key is being put to use for all kinds of transactions.
- Relatively fast: This is a faster algorithm as not much complex structure is involved with these algorithms.
- Easier and a lesser complex structure: This algorithm is more efficient and relatively has a lesser complex structure.
Why Should we use Symmetric Key Encryption?
We should be using this encryption to ensure that the security is not compromised, which is a key standard and specifically for all banking-based applications and other critical data-intensive firms. We should also use this algorithm due to its comparatively faster pace compared to other algorithms of the same league.
Future Scope
The scope of these keys is that they are generated, which are used with multiple given suits of algorithms, specifically called the cryptosystems, to lie till the fact these algorithms are being used for doing one transaction or for sending and receiving one or the other form of a message packet. As soon as the data is delivered to the intended recipient, the symmetric key encryption scope disappears as the key is then destroyed, and a fresh key is created for a different set of data.
Why do we Need it?
Data is critical, and securing data is one of the major challenges that big enterprises and banks struggle with today. The plain text form of data can easily be tampered with and played around by an attacker or a hacker. Therefore securing these critical pieces of information becomes mandatory and then algorithms and techniques such as symmetric key encryption come into play.
How is Symmetric Key Encryption Technology going to help you in Career Growth?
Securing data is one of the primary challenges which many businesses have been facing today. Therefore, if you learn symmetric or asymmetric key encryption techniques, you can see your way going through in cyber forensics, crypt- departments, ethical hacking, and other DoD-based research institutes.
Recommended Articles
This has been a guide to Symmetric Key Encryption. Here we discuss the working, uses, need, future scope, advantages, and how this technology will help you in career growth. You can also go through our other suggested articles to learn more –


