Updated July 12, 2023
Difference Between Encryption and Decryption
Encryption is the process of converting plain text into cipher text, i.e. converting the text from readable format to nonreadable format to secure the conversation between two parties or from an unauthorized person; on the other hand, Decryption is the process of converting ciphertext into plain text, i.e. converting the non-readable text into readable text which anyone can understand. Both methods use secret keys to perform desired operations.
Reasons why Encryption vs Decryption Should be Used
- They also give the confidentiality of our private information.
- They also help in ensuring that the documents haven’t been changed.
- Encryption prevents plagiarism and also protects IP.
- They are quite helpful for using network communication, such as the internet, and wherever hackers can access unencrypted data very easily.
- They are important methods since they help us in securely protect our data that we don’t wish anyone else to get access to.
- These processes help in the protection of our confidential data, like passwords.
Head-to-Head Comparison between Encryption and Decryption (Infographics)
Below are the top 6 differences between Encryption vs Decryption
Key Differences Between Encryption and Decryption
Below are the lists of points that describe the key differences between Encryption vs Decryption:
- The encryption algorithm uses the message, which is plaintext and key, during the encryption process. Whereas during the decryption process, the decryption algorithm transforms the encrypted form of the message, that is, the ciphertext using the secret key.
- Encryption occurs at the end of the sender, and decryption occurs at the end of the receiver.
- The main functionality of encryption is the conversion of plaintext into ciphertext, whereas decryption main functionality is the conversion of the ciphertext into plaintext.
- Encryption occurs automatically when data is being sent by a machine, referred to as the source. Programs that are pre-installed transform the information into the secret code prior to sending.
- Decryption takes place at the machine of the destination. The machine would receive and transform the encrypted form of the data into the original form.
- Encryption and decryption are both interrelated to each other since they are considered the utmost preference for the data’s privacy.
Key Types of Encryption vs Decryption
- Symmetric Key – It refers to those algorithms that use the same secret keys for the purpose of both the encryption of plain text and the decryption of the ciphertext.
- Asymmetric Key – It refers to those algorithms that make use of 2 pairs of keys for the purpose of encryption. The public key is made available to any random person, whereas the secret key is made available only to the message’s receiver.
- Public Key – It is an asymmetric encryption system that uses two pairs of keys. The public keys are used to encrypt the data or message that is sent to a receiver.
- Private Key – It is part of the public and private asymmetric pair of keys. This key is used in asymmetric encryption since we use the same key to encrypt and decrypt data.
- Pre-Shared Key – It is referred to as a secret that is shared, which earlier was shared between two of the parties with the help of a secure channel before we can use it.
Encryption vs Decryption Comparison Table
Below is the topmost comparison between Encryption vs Decryption
| Aspect | Encryption | Decryption |
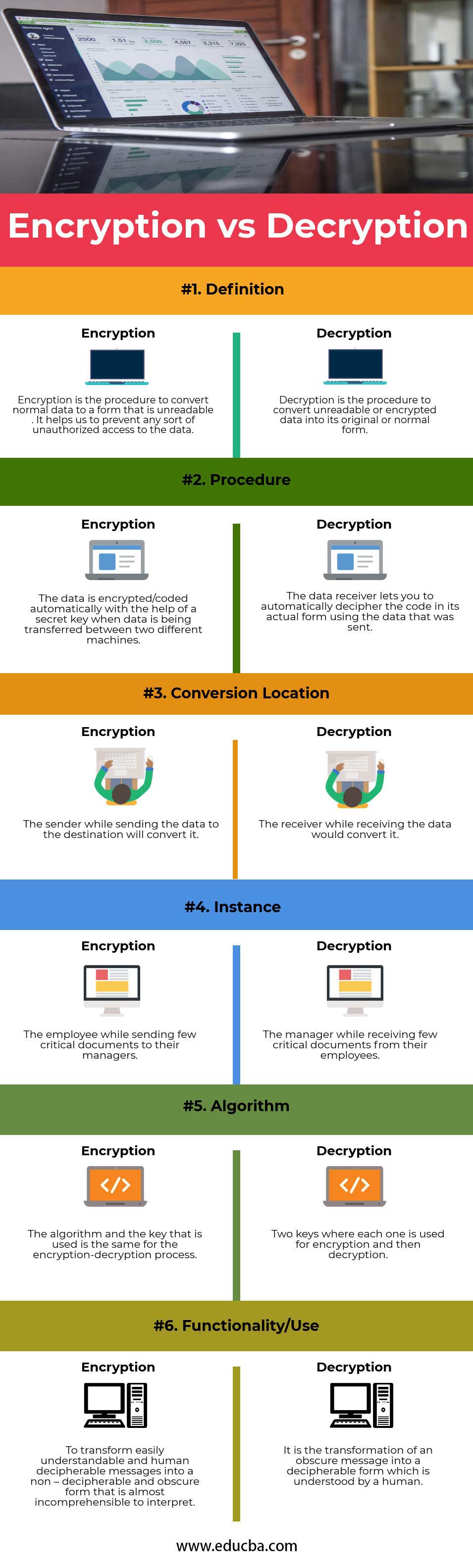
| Definition | Encryption is the procedure to convert normal data into a form that is unreadable. It helps us to prevent any sort of unauthorized access to the data. | Decryption is the procedure to convert unreadable or encrypted data into its original or normal form. |
| Procedure | The data is encrypted/coded automatically with the help of a secret key when data is being transferred between two different machines. | The data receiver lets you automatically decipher the code in its actual form using the data that was sent. |
| Conversion Location | The sender, while sending the data to the destination, will convert it. | The receiver, while receiving the data, would convert it. |
| Instance | The employee, while sending a few critical documents to their managers. | The manager, while receiving a few critical documents from their employees. |
| Algorithm | The algorithm and the key that is used are the same for the encryption-decryption process. | Two keys where each one is used for encryption and then decryption. |
| Functionality/Use | To transform easily understandable and human-decipherable messages into a non – decipherable and obscure form that is almost incomprehensible to interpret. | It is the transformation of an obscure message into a decipherable form that a human understands. |
Conclusion
Thus, both encryption vs decryption processes come under cryptology, that is referred to as a mixture of cryptography and cryptanalysis. Cryptography consists of techniques for ensuring security with the help of encoding messages to make them unreadable, whereas Cryptanalysis refers to the decoding of the messages where the unreadable form is transformed back to its normal form.
Encryption is invested for encrypting the information at the end of the sender end before transferring it across the network. However, decryption is invested in decrypting the coded content at the end of the receiver.
Recommended Articles
This has been a guide to the top difference between Encryption vs Decryption. Here we also discuss the key differences between infographics and comparison tables. You may also have a look at the following articles to learn more-