Updated August 19, 2023

Introduction to Simple Mail Transfer Protocol (SMTP)
The SMTP protocol is a Simple Mail Transfer Protocol that defines both MTA (Mail Transfer Agent) client to send mail and MTA (Mail Transfer Agent) server to receive the mail. SMTP simply defines how data or commands transfer from client to server or server to client, used two times between the sender and sender’s mail server and between two mail servers. To transfer mails, SMTP uses three phases, i.e. connection establishment, mail transfer and connection termination and commands, which are used to send data from client to server and responses, which is used to send data from server to client.
It can also perform the following tasks:
- It can transmit a message to more than one recipient.
- It can attach text, video voice or graphics in the message.
- It can transmit messages on networks external to the internet, as well.
Understanding of SMTP Protocol
- The main idea behind the SMTP Protocol is to set up communication guidelines among servers. The servers identify themselves and announce the kind of communication being done. Servers also handle errors like incorrect email addresses. For instance, if the recipient address is incorrect, then the recipient server responds with an error message.
Components
Normally, SMTP is integrated into an email application and consists of four main components:
- Mail user agent (MUA)
- Mail submission agent (MSA)
- Mail transfer agent (MTA)
- Mail delivery agent (MDA)
SMTP begins a session between the MUA, the user, and the MSA, the server. MTA and MDA are used for searching the domain for addresses and for local delivery services.
Commands Of SMPT
Let us look at a few SMPT Commands:
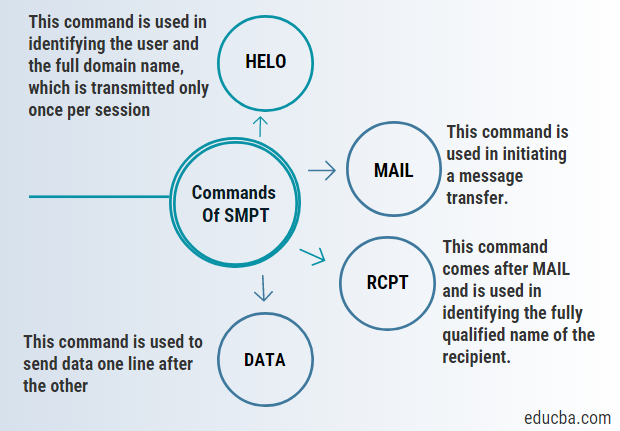
- HELO – This command is used in identifying the user and the full domain name, which is transmitted only once per session.
- MAIL – This command is used in initiating a message transfer.
- RCPT – This command comes after MAIL and is used to identify the recipient’s fully qualified name. For multiple recipients, we use one RCPT for each of the recipients.
- DATA – This command is used to send data one line after the other.
Types of SMTP Protocol
The SMTP model can be of the following two types:
- End-to-end model
- Store-and-forward model
The end-to-end design communicates between different organizations while communicating within the organization is the warehouse and forward model. To submit an email, the customer contacts the destination”s SMTP immediately. The SMTP server keeps the email until the receiver’s SMTP effectively receives it. Then, the SMTP customer initiates the meeting, and the SMTP receiver reacts to the petition for the meeting.
How does SMTP Protocol Work?
Let us look at the working of SMTP to get a better understanding.
1. Composition of Mail
Initially, the sender composes an e-mail message with the help of a Mail User Agent (MUA) and then transmits the e-mail. MUA helps in sending and receiving mail. The email message consists of two parts, namely the body and the header. The body comprises the main portion of the message, while the header comprises the subject, which is a one-line description of what the body holds and the sender and recipient address information.
2. Submission of Mail
After the document’s structure is complete, the customer utilizes the Simple Mail Transfer Protocol and sends the completed document to the server on TCP channel 25.
3. Delivery of Mail
E-mail addresses contain the recipient’s username and the domain name. For example, in [email protected], “abc” is the username of the receiver and “gmail.com” is the domain name. If the recipient”s domain name is different from the sender’s domain name, then MSA will send the letter to Mail Transfer Agent (MTA). To transmit the email, the MTA searches for the target domain. It looks in the Domain Name System (DNS) to find the target domain. Once the record is found, MTA connects to the server to transmit the message.
4. Receipt and Processing of Mail
After the server receives the message, it sends it to the Mail Delivery Agent (MDA), which keeps the e-mail until the user retrieves it.
5. Access and Retrieval of Mail
The email stored in the MDA is retrieved by logging into the MUA with the help of a username and password of the MUA.

Advantages
Below are some of the advantages of the SMTP Protocol.
- SMTP delivers the easiest form of communication by emails among several computers in a specific network.
- SMTP is made from a simple platform, making it easy and quick to send emails.
- SMTP presents reliability for outgoing email messages so that if a message is not sent successfully, then the SMTP server tries to re-send the same message up until the message is sent successfully.
- SMTP helps to have a committed server to manage outgoing email messages in organizations.
- It is easy and simple to connect to SMTP. Moreover, it offers an easy installation.
- SMTP connection has no limitations and can be used to connect to any system. All we have to do is incorporate the SMTP information.
- It doesn’t include any development from our end.
Conclusion
SMTP provides the easiest solution to send emails and messages to people all over the world. Bulk emailing is possible only via SMTP servers, and it is one of the most money-friendly means of sending out emails to a vast number of people at a time.
Recommended Articles
This has been a guide to the SMTP Protocol. Here we discussed the working, command, types, and advantages of SMTP with a detailed explanation. You can also go through our other suggested articles to learn more –


