Updated June 5, 2023
Introduction to Routing Protocols
Routing protocol defines how routers coordinate with each other and distribute information that allows them to choose routes between any two nodes on a computer network. In the basics of networking, a routing protocol is a key factor in today’s world of communication. The protocol is a set of rules for communication and routing is the process of choosing a path for that communication. Thus, Routing Protocol refers to the set of rules used for choosing paths for data transmission in a network.
These rules, i.e. routing protocols are followed by devices such as routers to communicate with each other and transfer incoming or outgoing data from or to devices. Every router has a pre-information of networks that are attached to it which is then shared by the routing protocol with all the devices on the network which makes the information of the whole topology of the network available to the routing protocol. This operation procedure is a factor used to categorize routing protocols further.
Types of Routing Protocols
Routing protocols are categorized into different groups as per their uses and other qualities such as:
- Purpose
- Operation (types of the path chosen, no. of routers falling in between the communication, etc.)
- Behavior
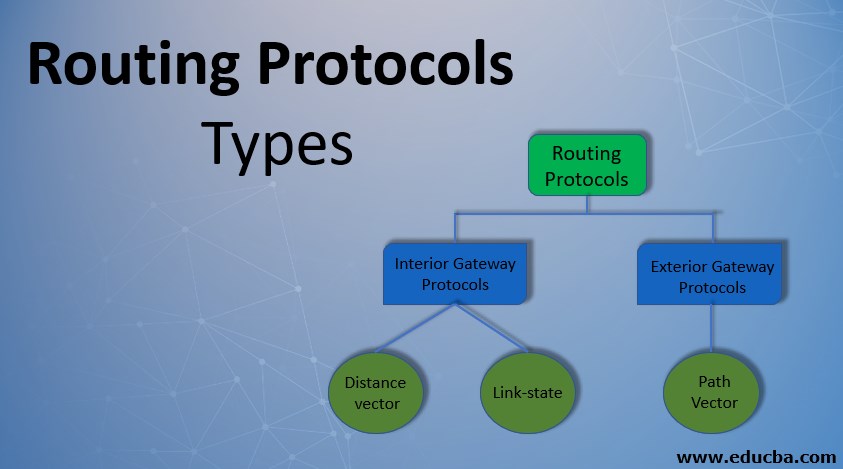
The major classes of routing protocols which are further categorized into sub-categories:
- Interior Gateway Protocols (Type 1 & Type 2)
- Exterior Gateway Protocols
1. Interior Gateway Protocols
Interior Gateway Protocols share routing information within a network controlled by a single administration. Types:
- Distance vector routing protocols
- Link-state routing protocols
Distance Vector Protocols
- This is categorized under the class “Interior Gateway Protocol Type 1”.
- It is a simple routing protocol as compared to other routing protocols
- These protocols determine routers based on distances. The best route for data is chosen based on distances.
- The distance is measured by the no. of routers a data packet has to go to one by one. One router is counted as one hop.
- This protocol mandates that a router should inform all its neighboring routes regularly about the network topology or arrangement.
- Complete routing tables are shared. duplicate copies of routing tables are shared with the neighboring routers to keep the neighboring routers update with the latest information and changes.
- The original algorithm of ARPANET was a distance-vector algorithm
- The version 1 of RIP (Routing Information Protocol) i.e. RIPv1 is the oldest distance-vector protocol and came into existence in 1988
- RIP can be used in local area networks (LANs) as it is an interior gateway protocol.
- For wide-area networks
- Examples of Distance vector protocols are Routing Information Protocol (RIP), Interior Gateway Routing Protocol (IGRP), EIGRP (Enhanced Interior Gateway Routing Protocol)
Problem:
- Each router has to propagate that new information to its neighboring routers, which takes a long time for all routers to have a current accurate view of the network.
- Frequently the information of network updates is exchanged which is a problem as it creates huge network traffic thus consuming large network bandwidths.
- These protocols use fixed-length subnet masks that are not scalable.
Link State Protocols
- This is a complex routing protocol in which every router shares information with other routers about the connection of other networks and the measurements used to reach the other networks in order to determine the best path.
- These are categorized under the class “Interior Gateway Protocol Type 2”.
- Each router in the network performs the link-state protocol
- Each router creates a graph (map of the network connectivity) which shows which router is connected to which router and device.
- Each router or node individually and independently calculates the next best logical path from itself for data transmission to every possible destination. This collection of best paths then forms the routing table of each node.
- Unlike Distance vector protocols, in link-state protocols, only the connectivity-related information is shared between routers and not the whole routing table
- No continuous broadcasting of routing tables is done
- Only when a change is detected in the network then only the link-state protocol router informs its neighboring routers.
- Examples of Link state protocols are Open Shortest Path First (OSPF), IS-IS (Intermediate System to Intermediate System)
2. Exterior Gateway Protocols
These are routing protocols used on the Internet for exchanging routing information between autonomous systems like Path Vector Routing Protocol. Big MNCs use EGPs to connect with each other. As far as now only Border Gateway Protocol has been considered as a useful and possible Exterior Gateway Protocol and “Internet” uses BGP as its routing protocol. The exterior routers and border routers on the “Internet” use BGP. These protocols use many factors to determine the shortest path but not the hops i.e. no. of routers.
- BGP is used in wide area networks (WANs).
- BGP uses TCP (Transmission Control Protocol) to share information between routers.
- BGP is used by telecommunication companies and internet service providers (ISPs).
Conclusion
We can conclude that routing protocol is a term that cannot be ignored or avoided as without it the communication of devices or data transfer is impossible. Routing protocol has been found after much research and studies which has proved as a great help in networking and communication. There are many further studies that test the types of protocols and yield that which type of protocol is best like some say EGP is best etc.
Recommended Articles
This is a guide to Routing Protocols Types. Here we discuss the Introduction and Types of Routing Protocols which include, Interior Gateway Protocols, Exterior Gateway Protocols. You may also look at the following articles to learn more –


