Difference between Cryptography and Encryption
Secure communication can be provided using techniques, in the presence of malicious third-party content called adversaries. These techniques can be referred to as Cryptography. Any private messages can be hidden from the public or any third parties using a set of protocols. These protocols need to be analyzed and constructed in an efficient manner in order to maintain the secrecy of message being sent. Modern Cryptography has a certain aspect that is central to it, like data integrity, authentication, confidentiality etc. In the modern world, Cryptography heavily relies upon subjects like mathematics and computer science. Algorithms for Cryptography are designed in such a way that they are hard to crack in practice by any malicious third party, also known as adversaries. A practical approach toward cracking such an algorithm would fail; however, the theoretical approach may possibly crack such a system. Thus, any algorithm can be cited as secure if its key properties cannot be deduced with a given ciphertext. Cryptography can be categorized into two branches: Symmetric and Asymmetric. With the symmetric approach, a single key is utilized for the encryption and decryption process, i.e. sender and receiver should have a shared key. However, with this approach, the distribution of key was a weak link, which gives rise to adopt a novel approach. In an asymmetric version of cryptography, sender and receiver have two keys, public and private. A private key is kept as a secret, whereas the public key is exposed to the outer world. Any set of data, which is encrypted with a public key, can only be decrypted using a corresponding private key. When it comes to comparison, the symmetric approach is faster than the asymmetric one: for example – a digital signature utilized asymmetric cryptography to encrypt messages in hashes instead of a complete message.
Encryption is one of the component of Cryptography, which is the most effective and popular data security technique. The encryption process involves transforming the data into another form, known as ciphertext, whereas the original data to be encrypted is known as plaintext. The plaintext is supplied to an algorithm and an encryption key, which create a ciphertext. This ciphertext can be decrypted with a valid key. Data which is stored on the computer need to transferred using internet or computer network. While sending the data across a network, the integrity or security of digital data needs to be maintained; encryption plays a key role in providing data integrity. There are some core securities features that need to be maintained: data integrity, authentication, and non-repudiation. Authentication means the data’s origin needs to be verified. Data integrity would ensure that content is not altered since it was being sent. And, non-repudiation would ensure the sender cannot refuse about sending the message. An encryption process is serving these primary security aspects. Like Cryptography, Encryption has two modes: symmetric and asymmetric. The same secret key is shared between the sender and receiver while performing encryption and decryption. The asymmetric approach, on the other hand, uses two different keys, public and private. Encryption technique is common among the usage of protecting information with civilian system, by governments and military. Customer’s personal and banking related data is highly prone to theft; encrypting such files is always a boon in case of the security system fails to protect the confidential data. Encryption at first may seem like a complicated approach, but various data loss prevention software handles it efficiently.
Head To Head Comparison Between Cryptography and Encryption (Infographics)
Below is the top 6 difference between Cryptography and Encryption
key Differences Between Cryptography and Encryption
Both are popular choices in the market; let us discuss some of the major difference:
- Cryptography is the study of concepts like Encryption, decryption, used to provide secure communication, whereas encryption is the process of encoding a message with an algorithm.
- Cryptography can be considered a field of study, which encompasses many techniques and technologies, whereas Encryption is more of mathematical and algorithmic in nature.
- Cryptography, being a field of study, has broader categories and ranges; encryption is one such technique. Encryption is one of the aspects of Cryptography that can efficiently encode the communication process.
- Cryptography is more generic in nature uses digital signature and another mode of techniques to provide security for digital data, whereas Encryption is being utilized with a set of algorithms widely known as a cipher to encrypt the digital data.
- Cryptography has a symmetric and asymmetric version, with a concept of a shared and non-shared key, whereas Encryption follows the same approach with some specific terms like ciphertext, plaintext, and cipher.
- Cryptography involves working with algorithms with basic cryptographic properties, whereas Encryption is one of the subsets of Cryptography that uses mathematical algorithms called cipher.
- Cryptography has its application which is wide and ranging from digital data to classical cryptography, whereas Encryption is utilized to encode the data in transit over a computer network.
- Cryptography’s fields include computer programming, algorithm, mathematics, information theory, transmission technology, whereas Encryption is more of digitalized in nature since the modern era.
- Cryptography involves two major components called Encryption and Decryption, whereas Encryption is a process of safeguarding information to prevent unauthorized and illegal usage.
- Cryptography act as a superset of Encryption, i.e. every process and terms used for Encryption can be said to be a part of Cryptography, whereas Encryption being a subset, has its own specific terms and processes.
Cryptography vs Encryption Comparison Table
Let us discuss the comparison between Cryptography vs Encryption are as follows:
| The basis of comparison |
Cryptography |
Encryption |
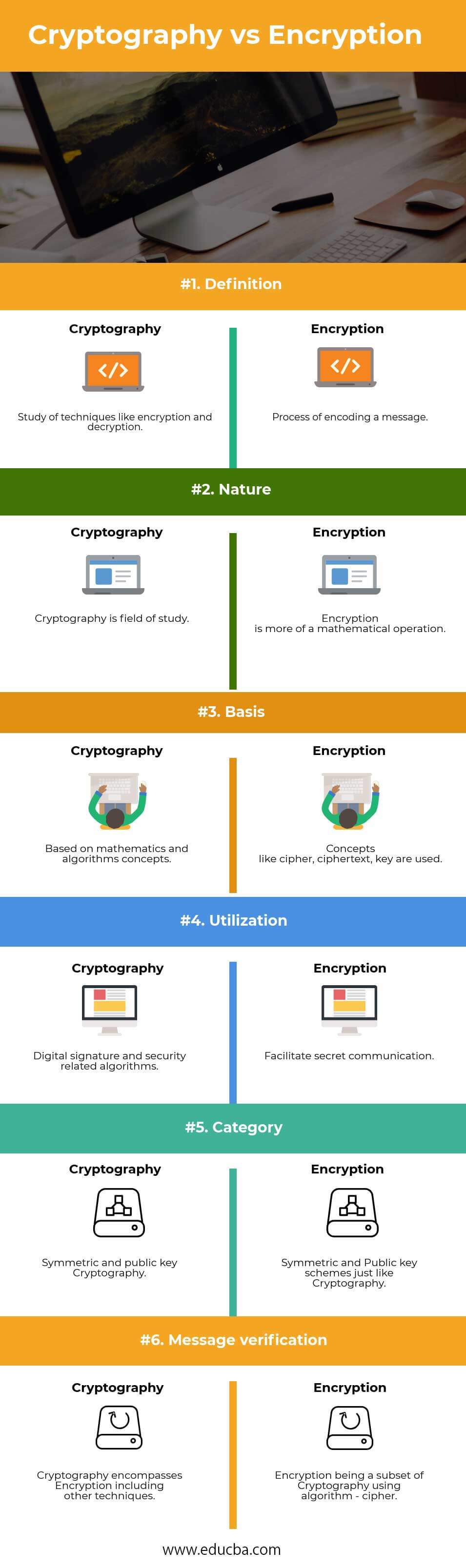
| Definition | Study of techniques like encryption and decryption. | A process of encoding a message. |
| Nature | Cryptography is a field of study. | Encryption is more of a mathematical operation. |
| Basis | Based on mathematics and algorithms concepts. | Concepts like a cipher, ciphertext, key are used |
| Utilization | Digital signature and security-related algorithms. | Facilitate secret communication. |
| Category | Symmetric and public key Cryptography. | Symmetric and Public key schemes, just like Cryptography. |
| Message verification | Cryptography encompasses Encryption, including other techniques. | Encryption being a subset of Cryptography using an algorithm – cipher. |
Conclusion
Cryptography involves various techniques and technologies, including algorithms, mathematics, information theories, transmission, encryption etc. Encryption is one such technique of Cryptography. A standalone, Encryption process can confidentially provide the message, but at the same time, other techniques and strategies are required to provide the integrity and authenticity of a message. So, in a nutshell, a successful scheme should provide data integrity, authentication, and non-repudiation, which is what Cryptography provides.
Encryption is provided in two forms, symmetric and asymmetric. Symmetric involves a single shared key among sender and receiver. Asymmetric, on the other hand, involves two public and private keys, one for a sender and the other for a receiver. Thus, a user can choose among any two forms. Public key cryptography is used to implement a lot of schemes like a digital signature. Various software is based on public-key algorithms, which are crucial in today’s world to provide digital data safe and reliable. One can say, cryptography vs encryption like techniques are the basis of a secure and reliable digital data mechanism. Internet & the digital world won’t survive without these two pillars of safety.
Recommended Article
This has been a guide to the top difference between Cryptography vs Encryption. Here we also discuss the key differences with infographics and comparison table. You may also have a look at the following articles to learn more –

