Updated February 14, 2023
Introduction to XPath Injection
XPath injection attack will occur on a website when a user uses the user-supplied information; the information is nothing but the xml data XPath query. While sending the information that was malformed into the website, the attacker finds out how our xml data will access and structured data to which they usually have access.
What is XPath Injection?
As we know that the querying of xml is done with the XPath. The simple distractive statement allows the xml queries to locate the information. We can specify a particular attribute like SQL for finding the matched pattern. When using xml for a website, it is widespread to accept some form of input onto the query string to specify the content for displaying the web page. The input of the query is sanitized to verify that it will not mess up with the query of XPath, which returns the wrong result.
XPath is the standard language, the syntax of XPath is always implementation-independent, and we can say that the attack will be automated. There is nothing another dialect that takes place in a database of SQL. In XPath, there is not any level of access control possible to get an entire document. Therefore, we are not encountering any limitations we will know from the SQL injection attack. Attacks will arise when the user’s data is incorporated into the queries of XPath, which is unsafe. The attacker will supply the input crafted to break out the context of data appearing as input and the interface for the surrounding query structure.
As per the purpose of the vulnerable query, we use an attacker to exploit an injection XPath flaw for reading an application’s sensitive information and logic of the application. It is the technique to exploit the applications that construct the queries from the user-supplied input. It is used directly by query of application as a document of xml as a more significant operation part; we can say that applying the transformation of xslt for an XML document.
XPath Injection Technique
The XPath injection issues will occur while storing data using xml; it is similar to SQL. It is an attack type, which we have defined in the injection technique and how it will occur in the XPath query. It is the type of attack where malicious input will lead to being unauthorized for sensitive information such as xml documents and structures. Its attack will occur when the user’s input is used in a query string construction. Although many techniques are used in XPath injection attacks, it will depend on the SQL dialect characteristics used by the target database, where the attack of SQL injection is more ubiquitous and adaptable.
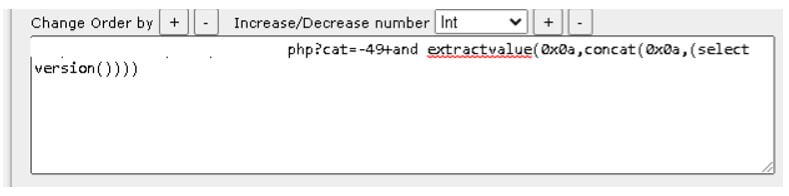
For the XPath injection technique, we can consider the following scenario. The website uses XML for storing the information and credentials. The xml documents are as follows.
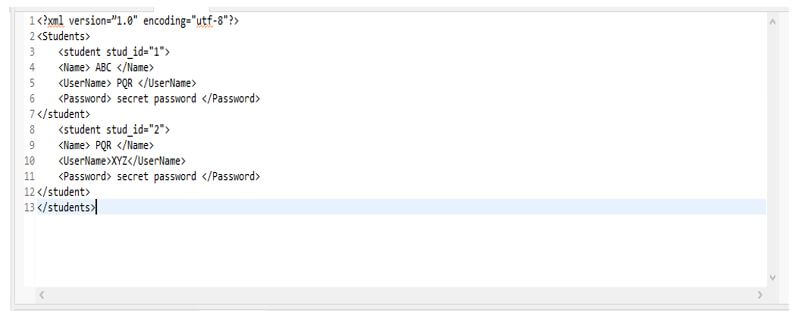
In the below xml document, we have defined the student username and password to define the technique of XPath injection.
Code:
<?xml version = ”1.0" encoding = "utf-8"?>
<Students>
<student stud_id="1">
<Name> ABC </Name>
<UserName> PQR </UserName>
<Password> secret password </Password>
</student>
<student stud_id="2">
<Name> PQR </Name>
<UserName>XYZ</UserName>
<Password> secret password </Password>
</student>
</students>Output:
Usage XPath Injection
XPath is the language used to address the parts of xml documents. The XPath language is designed for the xpointer. In many cases, the XPath expression will represent the sequence of the steps required to navigate one node document to another.
When storing web application data into the xml documents, we may use XPath to access the data in response to the user-supplied input. Suppose this input inserts into the XPath query without sanitization or filtration. In that case, the attacker will manipulate the interface of the query by using application logic to retrieve the data which was not authorized.
It is the technique to exploit the websites used to construct the XPath queries from the user-supplied input. Its attack occurs when the website uses user-supplied input for constructing the website query. By sending the malformed information to the website, the attacker will find how the xml data will be structured.
Examples of XPath Injection
Different examples are mentioned below:
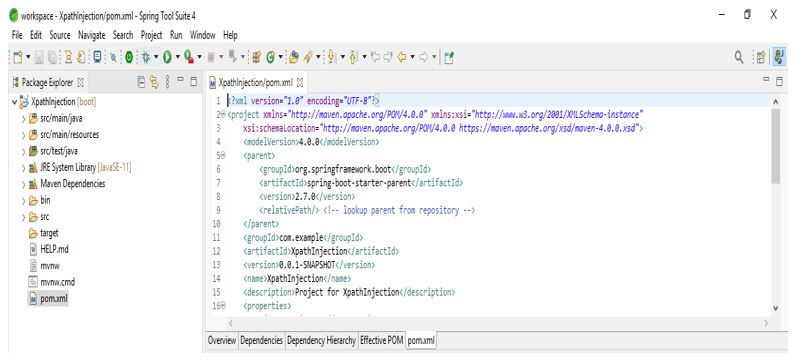
In the below example, we are creating the project of XPathInjection. In the below example, we are making the template of the project name as XPath injection into the spring boot.
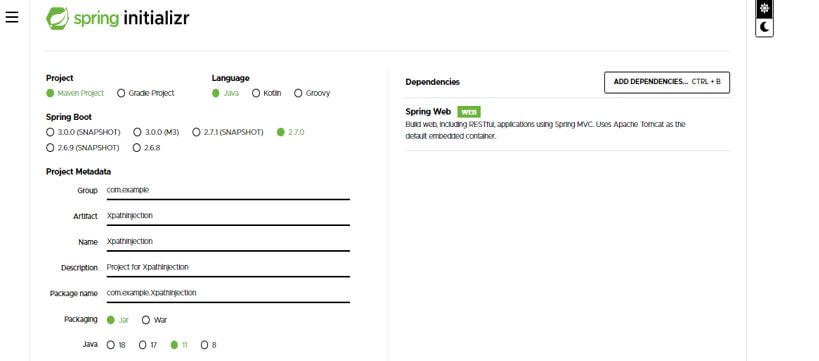
1. While creating the project into the XPath injection using spring boot, we are providing the group’s name as com.example, artifact name as XPathInjection, project name as XPathInjection, and selected java version as 11.
Group – com.example
Artifact name – XPathInjection
Name – XPathInjection
Spring boot – 2.6.7
Project – Maven
Java – 11
Package name – com.example. XPathInjection
Project Description – Project for XPathInjection
Dependencies – Spring web
Packaging – Jar
2. In the figure below, we can extract the project name as XPathInjection and open this project using the spring tool suite.
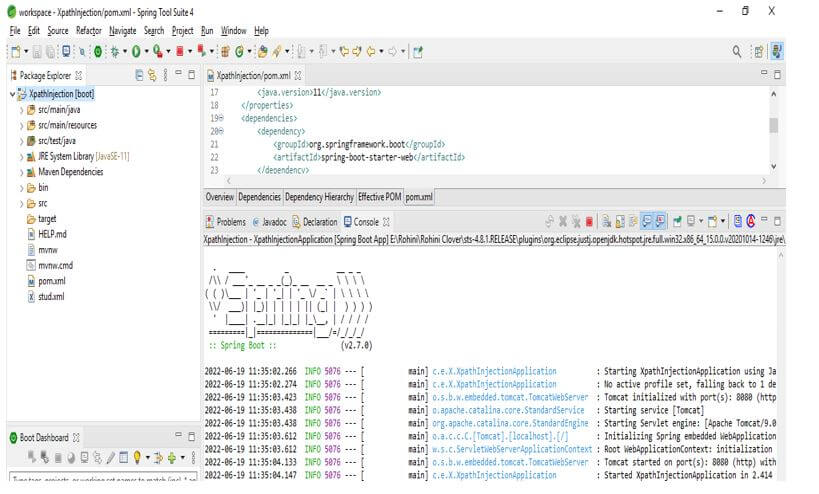
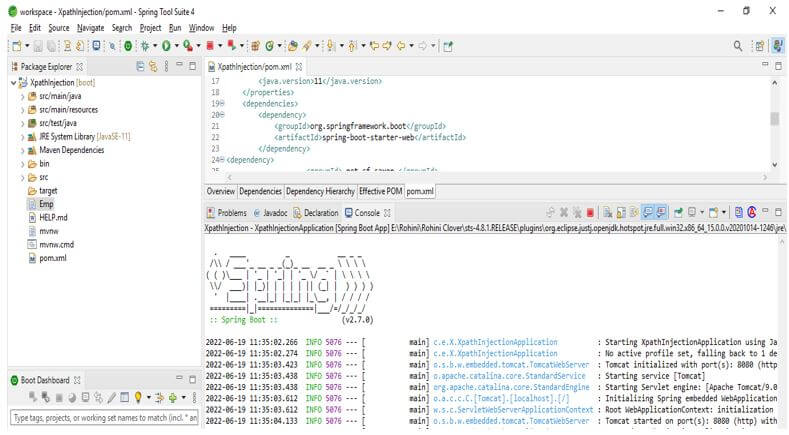
3. In the below step, we are checking the structure of the XPath injection project. Also, we are seeing the project dependency, which was added to the pom.xml file. Also, we are checking all the structures of the XPath injection example project.
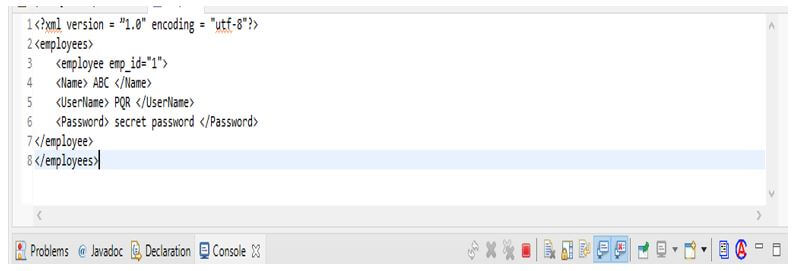
4. Now, we are creating the xml file for an example of XPath injection.
Code:
<?xml version = ”1.0" encoding = "utf-8"?>
<employees>
<employee emp_id="1">
<Name> ABC </Name>
<UserName> PQR </UserName>
<Password> secret password </Password>
</employee>
</employees>Output:
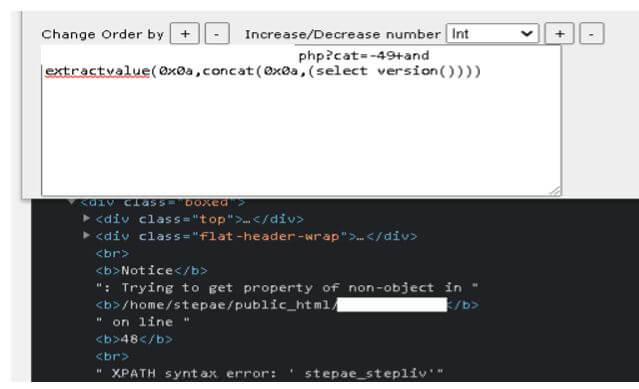
5. In the below example, we are detecting the vulnerability in our application as follows.
6. Now, we are defining the database name for the XPath injection as follows.
Conclusion
XPath is a standard language, the syntax of XPath is always implementation-independent, and we can say that attack will be automated. The attack will occur on a website when the user uses the user-supplied information; the information is nothing but xml data XPath query.
Recommended Articles
This is a guide to XPath Injection. Here we discuss the introduction, XPath injection technique, usage, and examples. You may also have a look at the following articles to learn more –