Updated August 19, 2023
Introduction to DDoS Attack
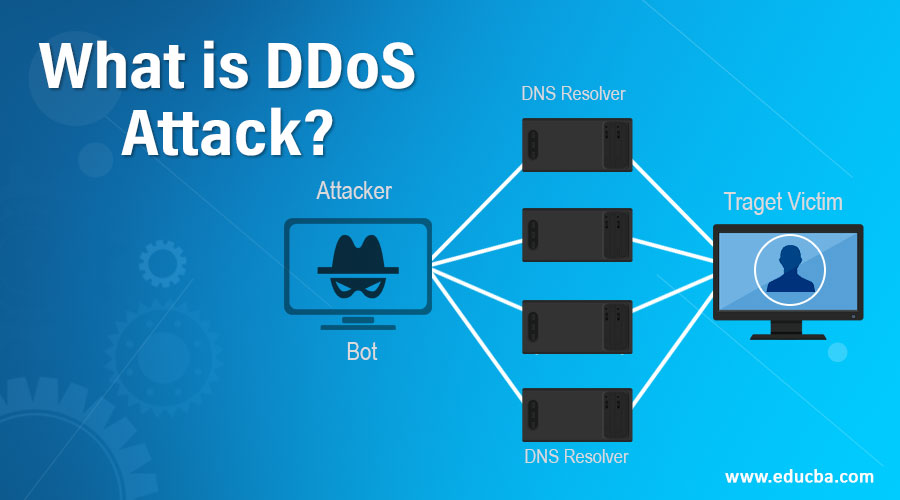
DDos, commonly abbreviated as Distributed Denial of Service, is used to wash out the network resources. The end-user cannot get access to the essential information and also makes the application’s performance very slow. DDos attempts to make a web application or online service busy by congestion with massive floods of traffic produced from several multiple resources. It is hard to locate where the attack comes from or the origin of the attack because it arrives from various sources, usually uses Trojon to infect a system. In this article, we will discuss What is DDoS Attack?
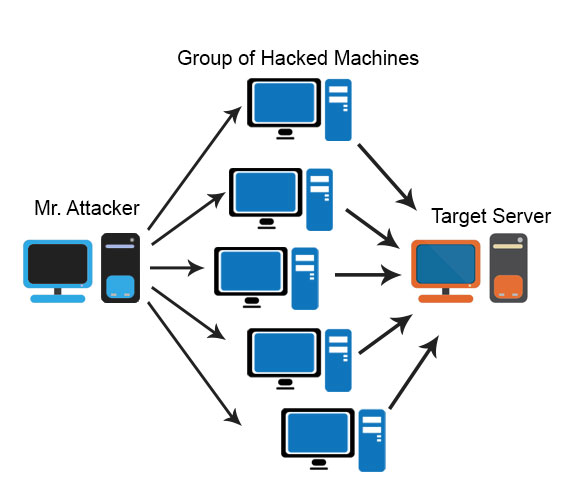
DoS (Denial of Service) attack is different from DDoS attacks because DoS is used to target a single network connection and a single computer, whereas the DDoS attack is used to damage multiple systems and several network connections simultaneously time which is referred to as Botnet.
What are Botnets?
Botnets are defined as the attackers construct a hacked technology network; they spread by a piece of code through social media, websites, and emails. Attackers can control the system remotely, without the end users knowledge; once these systems get infected and frequently, they used to commence an attack on the infected computers against any intention.
There are few symptoms to track whether your computer is get infected by DDos,
- Constantly loss of internet connection.
- A website that was available before unexpectedly becomes unavailable.
- Incapable of right to use any website.
- Corrupted network performance.
- Unable to use internet services for a lengthy time period.
Purpose of a DDoS Attack
The purpose of the DDoS attack primarily includes politics, competitions, revenge, war, and criminal activities.
How does it work?
- The DDoS attack has in need of an attacker to get the power of a network of online systems in a process to carry out an attack. Once the systems or other machines get infected with malware, each one reflects into a bot; then, the attacker can easily access the computers through remote controls.
- If the botnet has been established, the attacker can have complete access to the computers by transferring well-run instructions to each bot through the remote controls. Once the IP address of the end-user is tracked or targeted by the botnet, each and every bot will start to work on it to respond by transferring request to the targeted machines, and probably origin the server or network resultant in a DoS to normal traffic, and to make overflow capacity.
How can DDoS Attack Happen?
- DDos is a form of a cyberattack with intense critical systems to interrupt network connectivity or service so that it creates a denial of service for users of the specified resource.
- DDoS attacks make use of the power of numerous malware-affected systems to achieve a single system.
The Motive Behind DDoS Attack
- The DDoS attack is used to flood out the network resources so that the end-user cannot get access to the necessary information, and also makes the performance of the application very slow.
- The DDoS attacks can control or take down the website of all sizes commencing from large enterprises to small units for more susceptible sites.
- The progress for the attacks differs from pure financial gain to politics.
- The motive behind the DDoS attacks is that they can be sold out, so the consumer may ask for an assured website to be taken offline and make payment for its execution. In this case, revenge is often a motive.
- On the other hand, if the attackers require money, they might also want to blackmail a website for their required money and also keep their website slow down or suddenly becomes unavailable for a long period till their required payment.
- In conclusion, a trendy approach used to control political events and obstruct others a political memo is to thrash and take down websites with unusual views. An activity like this is becoming a progressively more smart way of using DDoS attacks to deal with the media.
What to do after DDos Attack?
After the DDoS attack process, we can find out our system behaviours like slow responses; there will be no website access and loss of internet access; likewise, we will face such cases. If we are facing such issues to follow few things,
- To make a call to ISP (Internet Service Provider) and let them know that you have attacked by DDoS.
- If you can control your website, keep it in safeguarding mode to avoid any loss of data and report to the management team about the concern.
- Call the third party to inform them that you are under attack, which may depend on security management or service delivery.
- To get as much as information achievable.
- To get track of server logs with the time of events.
- To monitor all the system’s occurrence and be attentive that any changes might happen on your system during or after the DDoS attack.
- To showcase the traffic throughputs, traffic statistics.
- To check back-end databases and all critical systems and note any changes that might occur on the system.
- To look out for the issues that take place in temporary sites.
To employ professional guidance to help ease the issues and execute a flexible solution that will help to reduce any DDoS occurrences. To retain a risk register and renew any tragedy improvement plan to comprise a DDoS endurance plan. To avoid DDoS attacks, have in contact with DDoS prevention experts.
How to prevent it?
The DDoS prevention are followed,
- Attack Prevention and Preemption (before the attack)
- Attack Detection and Filtering (during the attack)
- Traceback and Identification (during and after the attack)
1. In Attack Prevention and Preemption (before the attack), we have to protect the host from agent implants and master by using scanning measures and signatures to identify them. To monitor the network traffic for recognized attack information’s sent between masters and attackers.
2. In Attack Source Trackback and Identification(during and after the attack) to locate the precise source of a packet without relying on source point. The noticed information can be recorded by the routers, and also routers can send the message about the seen packets to their target place.
3. In Attack Detection and Filtering (during the attack) in Attack Detection, we can identify the attacked DDoS packets and packet Attack Filtering to categorize those packets and reduce them.
Conclusion
A DDoS (Distributed Denial of Service) attack uses network vulnerability, which makes a loss of network connection persistently, slows down the system performances, and creates more traffic on the internet, resulting in the inability to use internet service for a long period of time. This practice is favourable for the trespasser who wishes for the valid user to cooperate with the safety measures of his essential and sensitive information. Once the system gets attacked by DDoS, it might not be found easily, and its prevention is also not the easiest one. The only way to get relieved from this is to determine whether any injuries caused by it and to take action to recover them.
Recommended Articles
This has been a guide to What is DDoS Attack. Here we discussed the Introduction, how it works, its Purpose, and the Motive of DDoS. You can also go through our other suggested articles to learn more –