Introduction to VPN Tunneling
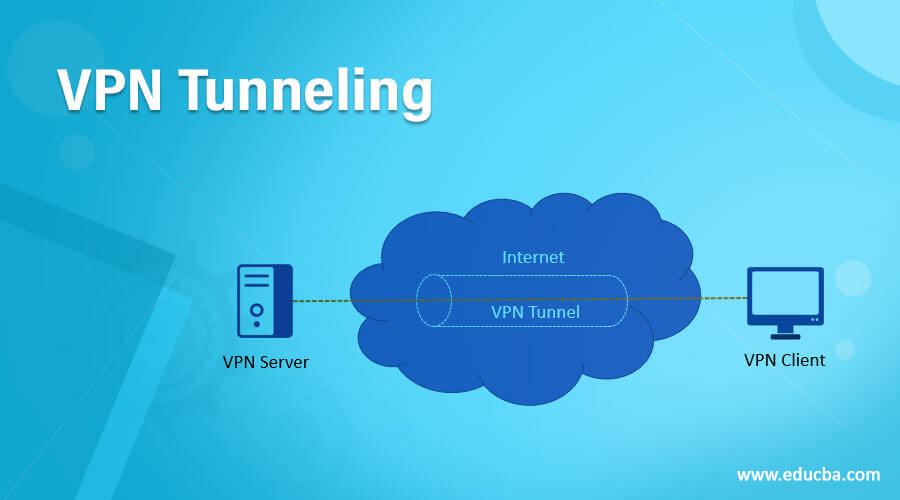
You might have heard that a mechanism called” tunneling “is used by Virtual Private Networks (VPNs) to spread a private network into a public network (the Internet). Tunneling is the method of encrypting information and keeping it isolated from other internet traffic. It allows the transparency (data remains unaltered) and anonymity (data remains secret) of messages to be covered by a VPN as they pass across the public network. For instance, never sending it across the public network will be the safest way to secure the data in the first place, but you know that’s almost unlikely. That is why we depend on a VPN when we indulge in online activities to protect our privacy.
What Is VPN Tunneling?
The term VPN tunneling defines a mechanism through which data is safely transferred via a non-secure environment without violating privacy from one computer or network to another. By repackaging it into a new shape, tunneling requires shielding information. In practice, there is, of course, no actual tunnel; the data must flow through the same wires as all other data that travels through the public network. Encapsulation isolates the data packet from all data passing across the same network. At the same time, encryption also renders the data ‘invisible’ (unreadable) to intelligence officers and offenders who identify it as encrypted data. So it’s like the data passes into a tube inside. Using an armored transport van along public roads, you might think of VPN tunneling as close to the practice of transferring actual money from one bank location to another. In this instance, the cash is your data, the non-secure public network is the public highway, and the armored van is similar to a VPN tunnel.
Many VPN providers offer users the option of multiple tunneling protocols to select from. The VPN tunneling protocol you want to use has important consequences for your tunnel’s consistency and efficiency. Until picking a tunneling protocol, some key questions to consider include:
- How quickly does it obstruct apps from transverse (get past)?
- How easily can I use and access it
Different Types of VPN Tunneling Protocols
A VPN tunneling protocol is an agreed-upon series of data transfer and encryption laws. The Layer Two Tunneling Protocol (L2TP), Point-to-Point Tunneling Protocol (PPTP), Internet Protocol Security (IPSec), Open VPN (SSL / TLS), and Secure Socket Tunneling Protocol (SSTP) are some of the most common protocols used.
1. PPTP
Site-to-site and remote VPN connectivity is provided via PPTP over the internet. It is easy to use and configure because setting up a tunnel to the remote server requires only a password, username, and server address. Because of its low encryption standard, it’s one of the fastest protocols. For that purpose, for applications where speed is more critical than full protection, PPTP is useful.
2. L2TP
Instead of having data security independently, the L2TP tunneling protocol depends on another protocol to wrap the data again, establishing two security layers to secure data passing through the tunnel. The double encapsulation process, however, makes L2TP / IPsec a little slower than Point-to-Point Tunneling Protocol.
To help protect your online activities, Microsoft has created the Secure Socket Tunneling Protocol (SSTP). It is supported on Windows 7, Windows 8, and Windows 10 systems by default, making it simple to set up for Windows users. The SSL, the same protocol used to operate secure network links (HTTPS), transports internet data.
Best VPN Tunneling Tools
Lets us discuss the VPN Tunneling Tools in detail.
1. NordVPN
Viewed by analysts and customers alike as one of the best all-around VPNs available today. It offers impressive performance and reliability, along with a proven ability to get past demanding geoblocks and firewalls. Its security safeguards include a circuit breaker and a strict no-logs policy, and its customer service agents are knowledgeable and easy to reach via 24x7x365 live chat.
2. PrivateVPN
By offering excellent network speed and stability along with some interesting features, including a Team Viewer option that helps you to interact directly through configuration with the provider’s tech team, PrivateVPN has climbed up the VPN ranks. PrivateVPN also remains a clear favorite among consumers.
3. ExpressVPN
We spent hours checking the declaration of this VPN to be the fastest premium VPN in life, and it never let us down. Features such as military-grade encryption and an automated kill switch show that this VPN did not attain its pace by compromising privacy security.
4. TuxlerVPN
Similar to ExpressVPN, Tuxler VPN is a great solution if you want to protect your online activities from potential threats. This is possible because it uses military-grade encryption protocols. This means that TuxlerVPN ensures optimal confidentiality and protection of your sensitive information. With Tuxler VPN, you can browse the web anonymously. Additionally, Tuxler VPN offers a user-friendly interface that is extremely fast, making it a preferable option for seamless browsing.
5. CyberGhost
CyberGhost is best known for its simple, easy-to-use GUI experience and enjoyment by all levels of users. Via a comprehensive global server network, it also provides fast, secure connections. Just two of the many aspects that CyberGhost protects consumer privacy are a checked no-log policy and an opportunity to buy a subscription anonymously through digital currency.
Conclusion
In this article, we have seen VPN tunneling, along with various protocols and software. I hope you will find this article helpful.
Recommended Articles
This is a guide to VPN Tunneling. Here we discuss the introduction and Different Types and tools of the VPN Tunneling Protocol. You may also have a look at the following articles to learn more –


