Updated March 18, 2023
Introduction to Types of NAT
The story behind the existence of NAT is that using IPV4, i.e. 32 bit, which will give around 4.2 billion unique IP’s, In which it is impossible to accommodate 7 billion* No of devices used by an individual in the world, Solution to keep using IPV4 yet, get more devices on the internet is NAT. NAT processes in which one or more Local IP address is translated into one or Global IP addresses and vice versa in order to provide internet access to the local hosts. Generally, a border router or firewall will be configured for NAT. In this article, we will learn about the different types of NAT in detail.
NAT Terminologies
Before jumping into how NAT works and Types of NAT, let us understand a few terminologies to avoid confusion.
- Inside local address: Private IP address, assigned to a host on the inside (local) network, it is inside host as seen from the inside network. This IP address is assigned by the router connected to a group of devices; it is not accessible from the internet. All addresses starting from 192.168.x.x and 10.x.x.x are reserved for private IP addresses. We can use any IP within range without being worried about it; some other device is using the same.
- Inside global address: It is one or more IP addresses, which represents the local network, seen as inside host from outside network. When we register with ISP, we get an IP, which accessible throughout the internet. It is assigned to the router connected to a group of devices. Ex:12.13.14.15
- Outside local address: Actual IP of the remote host, after NAT translation.
- Outside Global address: It is the IP address of the remote host before
usually, local IP addresses are referred to as ‘private IP’ and Global as ‘public or registered IP’.
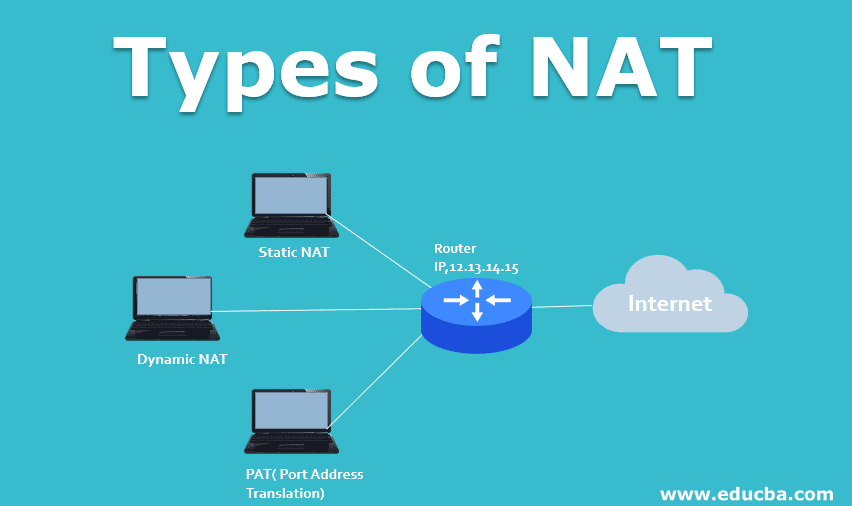
Types of NAT
Based on how the IP addresses’ mapping is done from local IP to Global IP, there are 3 types of NAT.
1. Static NAT
In this case, there will be one to one mapping between private IP and Public IP. i.e. a private IP 192.162.19.2 is permanently mapped to a global IP 13.14.56.07; it is commonly used for web hosting.
2. Dynamic NAT
In this case, the router is provided with a set of public IP addresses, any device that wants to connect to the internet will be provided with immediately available public IP at the router end; there will be one to one mapping based on a first-come, first-served technique but not permanent, the public IP address used by the private IP can change over time.
3. PAT( Port Address Translation)
In this case, many private IP addresses are mapped to a single public IP; port numbers of devices distinguish traffic, i.e. which packets belong to which private This is cost-effective; many users can connect to the Internet using single public IP at a time. It is also known as NAT overloading.
How Does NAT Work?
To understand how NAT works in a real scenario, Let’s consider a small topology; it has 3 devices connected to a router, let devices be a laptop, a mac, and a smartphone, they are all connected to a router, the router in its turn is connected to the internet, public IP assigned to the router is 12.13.14.15, the router has assigned 10.11.12.01 to a laptop, 10.11.12.01 to MAC and 10.11.12.03 to a smartphone.
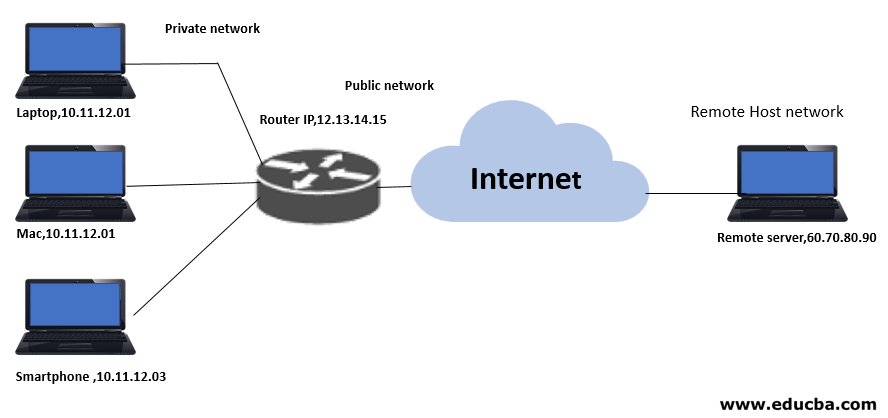
Assume that laptop wants to connect to a remote server which hosts ‘weather forecasting website’ with global IP 60.70.80.90 and smartphone wants to access Facebook hosted at global IP 60.70.80.80 when both requests arrive at the router, router maps the IP and entry in NAT table as shown below:
| Device | Private IP(Source IP: Port) | Public IP(Public IP: Port) |
| Label | 10.11.12.01 : 42301 | 12.13.14.15:6666 |
| Smartphone | 10.11.12.03 : 42302 | 12.13.14.15:5555 |
The request with Public IP and Host IP with a message is sent to respective host servers via internet, on port 80 commonly used for HTTP requests, remoter servers respond to Public IP with added message, at router interface, router refers NAT table and sends back the response message to respective private IP and to their respective ports. To the laptop or smartphone, it appears the response has been sent directly to them by remote hosts.
Advantages of Using NAT
- It prevents the depletion of ipv4 addresses, i.e. more devices can connect to the internet using ipv4.
- It provides an additional layer of security by making the original and destination addresses hidden from each other.
- NAT provides increased flexibility while connecting to the Internet.
- If we are changing the device IPs used for a service accessed over the internet, it will not affect the NAT system’s service IP.
Conclusion
IPV4 is an age-old idea that is implemented after the 1970s to overcome the drawback of its NAT was introduced. It has a few disadvantages like it is time and resource consuming, it loses the traceability between source and destination and delays communication.
A slow migration is happening between IPV4 to IPV6, which will give 32 followed by 37 zeroes unique IP addresses, yet delayed because many devices that are already on the Internet support only IPV4, and it takes time to break and build the new IPV6 supporting architecture.
Recommended Articles
This is a guide to Types of NAT. Here we discuss the introduction, working, terminologies, and top 3 types of NAT and its advantages. You may also look at the following articles to learn more-


