What is Tor Browser?
Tor Browser is a web browser meticulously crafted to ensure users’ privacy and anonymity while navigating the internet. It operates on the principles of the Tor network, commonly known as “The Onion Router.” The US Navy developed this Onion-routing mechanism to protect secret US government communications. This network directs internet traffic through various relays, encrypting it at each stage to obscure the user’s location and online activities from any potential network monitors.
Tor Browser is built upon the Firefox web browser and includes several privacy-enhancing features by default. It integrates seamlessly with the Tor network, providing users a simple way to access the internet anonymously. Tor Browser safeguards your online privacy and anonymity. It leverages the foundations of Mozilla Firefox while configuring your web traffic to traverse through the Tor network, which comprises volunteer-operated servers, effectively anonymizing your online endeavors.
Understanding Tor Browser
Tor Browser emerges as a potent tool for anonymous internet browsing. It obscures users’ IP addresses, encrypts their data, and directs internet connections through a sequence of randomly chosen Tor relays, rendering it exceedingly challenging for entities like internet service providers, government agencies, or malicious actors to monitor users’ online activities.
Moreover, Tor Browser comes equipped with a range of built-in privacy features. These include blocking third-party trackers, restricting websites from accessing your location, and deactivating browser plugins that might compromise your anonymity.
Table of Contents
Key takeaways
- Onion routing shields internet traffic through a series of relays over the network.
- Masking IP addresses safeguards online activity from attackers.
- Encryption protects sensitive information from interception.
- Shield the user’s actual location and online identity.
- Circumvent censorship in a restricted environment and access blocked content.
How does the Tor browser work in Kali Linux?
Tor Browser in Kali Linux: Tor browser in Kali Linux enhances privacy and security by masking the user’s identity for conducting cyber security investigations or sensitive online activities.
- Onion Routing:
When a user requests a website or any resource through a Tor browser, the request is encrypted and routed through a series of intermediary servers called Tor relays or nodes. Relays in a network form a chain or sequence, with each relay knowing only the IP address of the one before and after it. It ensures that no relay knows the traffic’s origin and destination. This multi-layer routing process represents layers of the onion by masking the data packets’ source and destination.
- Entry, Middle, and Exit nodes:
When a user browses a website or resource in the Tor network, the internet traffic is encrypted and sent through three layers of nodes to reach its destinations as follows:
- Entry Nodes: The encrypted data packets are sent to an entry node. The entry node peels off the first layer of encryption and passes the data packets to random middle nodes.
- Middle Nodes: The data packets are passed through several middle nodes, each peeling off another layer of encryption. The middle nodes must know these data packets’ source and destination.
- Exit Nodes: Finally, the data packets reach the exit node, decrypt the last layer of this encryption, and send the user request to the destination websites or resources. These websites are unaware of your IP address. They only see the exit node IP address.
- Encryption:
The Tor browser employs end-to-end encryption to protect user communication and provide confidentiality. The data is encrypted using multiple layers of encryption, creating a tunnel through a Tor network. Further, the Tor browser uses HTTPs everywhere, enhancing security and privacy.
- Tor browser bundle:
The Tor browser comes bundled with everything containing a modified version of Firefox for additional security and privacy, Tor clients for managing network connections, and pre-configured settings to ensure that traffic is routed through the Tor network.
- Launching Tor browser on Kali Linux:
When a user launches the Tor Browser on Kali Linux, it provides a user-friendly interface, allowing users to access the internet anonymously with minimal configuration. It launches through the following steps:
- Connect to Tor network: The launcher selects the entry, relay, and exit nodes for passing traffic and maintaining anonymity.
- Circuit establishment: The Tor browser establishes a circuit through the Tor network. It consists of relays to pass internet traffic from origin to destination.
- Routes traffic: The internet traffic is routed through this circuit securely, ensuring the user’s browsing activity and identity anonymity.
What are the reasons to use tor and who uses it?
Reasons to use Tor:
- Enhanced Cybersecurity and Privacy:
The Tor browser safeguards privacy by ensuring an extra privacy layer for users concerned about invasive tracking, online surveillance, or identity theft. The Tor service encrypts and routes internet traffic through relays that safeguard online activities from the third eye.
- Circumventing Censorship and Accessing Restricted Content:
Tor facilitates users to bypass censorship enforced by governments in their region. It enables individuals to access online services or websites that may be restricted or blocked by a strict government censorship regime.
- Protection from Surveillance and Tracking:
Tor shields user’s activity from monitoring and interception by ISPs, advertisers, threat actors, or government agencies. It anonymizes the user’s online activity and identity and alleviates the danger of online tracking, data breaches, and targeted advertising.
- Secure communication:
Tor ensures a safe platform for sharing sensitive information and communicating without compromising the user’s safety. It protects the identity of an individual, activist, and journalist, ensuring secure communication and freedom of expression in restricted or threatened regions.
Who uses Tor?
Government Agencies:
Government agencies benefit from Tor browsers for protecting shared communication and sensitive information from surveillance. Government officials ensure integrity and confidentiality during online interactions.
Illicit Organization:
Illegal organizations use Tor browsers to mask their online identity and activity from law enforcement agencies. Tor shields and encrypts the illicit acidity for cyber criminals who conduct extortion, money laundering, and other illegal activities.
Privacy Seeker:
Many individuals concerned about personal information use Tor to shield their online identity and activity. Privacy seekers may include journalists or activists who want to enhance online privacy, communicate securely, and protect their digital rights.
For-profit Enterprises:
For-profit enterprises use the Tor browser for extra data privacy and security. Tor platform safeguards businesses’ sensitive corporate information, online transactions, and customer privacy.
Prerequisite
There are a few prerequisites required before installing the Tor browser on the Kali Linux environment:
1) Internet Connection:
Installing the Tor browser requires downloading specific files and browser packages, and this process requires robust internet access for quick execution.
2) Sudo access:
The Kali Linux system should have sudo access because most of the installation commands use sudo to execute the command.
3) System update:
Before installing, updating the system using the “sudo apt update” command is preferable.
4) Memory:
The Tor browser requires a certain amount of memory on the disk. So, before starting the installation process, free up disk space for downloads.
Installation of Tor Browser on Kali Linux
1. By using Terminal
Let us dive into the step-by-step process of installing and launching the Tor browser in Kali Linux.
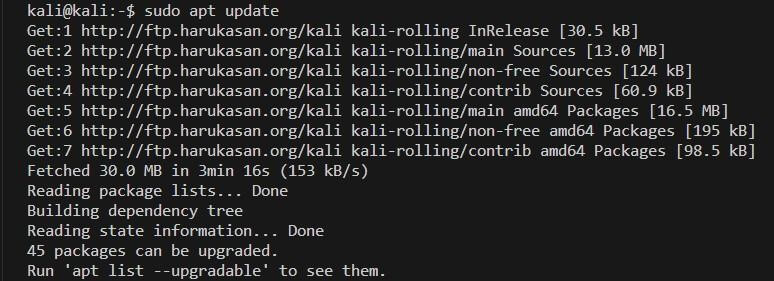
Step 1: In any Linux environment, the first step is to update the system with a simple universal command.
“sudo apt update”
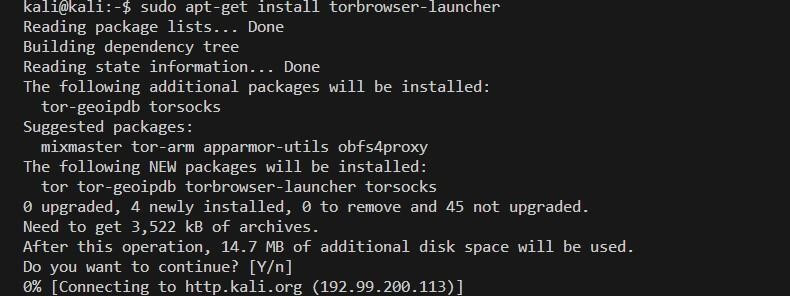
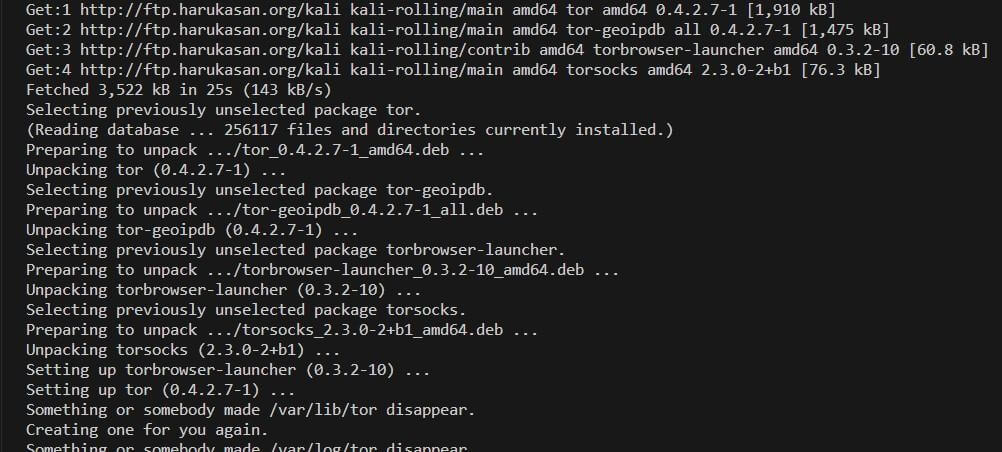
Step 2: Once the system is updated, install the tor browser launcher by executing the following command:
“sudo apt –get install tor torbrowser-launcher”
Step 3: Launch the Tor browser in Kali Linux by executing the following command
“sudo torbrowser-launcher”
Or simply by searching for it
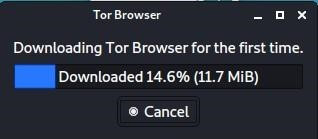
Step 4: This will start the process of launching the browser. If you are doing this for the first, the following dialog box will pop up.
This might take a while if the internet connection is low.
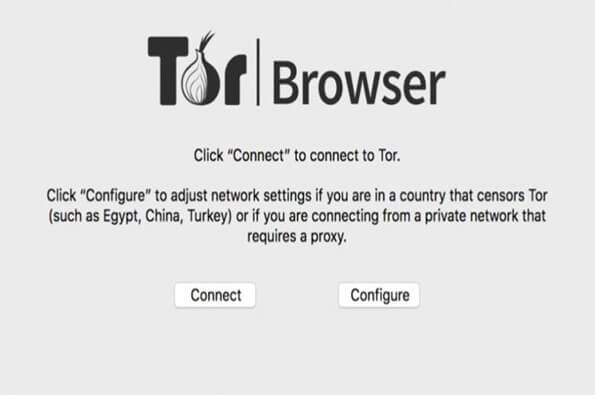
Step 5: After the initial launch, we need to connect it to the Tor Browser by clicking connect.
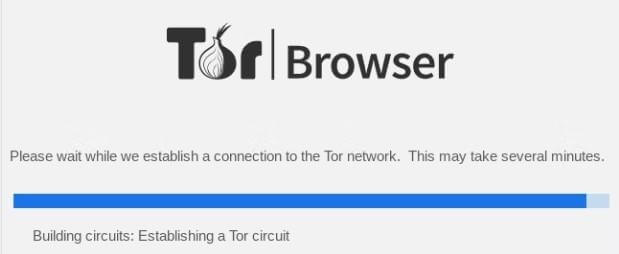
Step 6: Once you click on connect and apply the necessary settings, It will establish the connection to the Tor network.
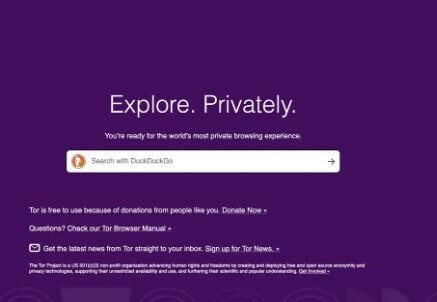
Step 8: Once the connection is established, we are ready to use the Tor browser.
2. By manually
Step 1: One can also download the Tor browser from its official website. Click on the “Download for Linux” button.
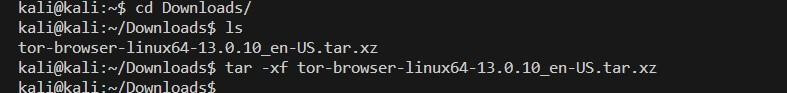
Step 2: Check for the file in the respective folder after the download is complete, and unzip the folder. This can also be done by executing the following command
kali@kali:~$ cd Downloads/
kali@kali:~/Downloads$ ls
tor-browser-linux64-13.0.10_en-US.tar.xz
kali@kali:~/Downloads$ tar -xf tor-browser-linux64-13.0.10_en-US.tar.xz
kali@kali:~/Downloads$
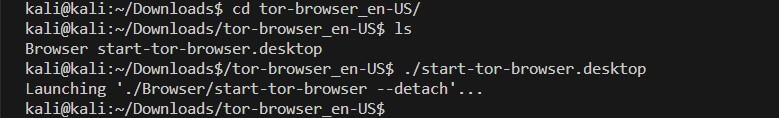
Step 3: Launch the Tor browser by using the following command
kali@kali:~/Downloads$ cd tor-browser_en-US/
kali@kali:~/Downloads/tor-browser_en-US$ ./start-tor-browser.desktop
Launching ‘./Browser/start-tor-browser –detach’…
kali@kali:~/Downloads/tor-browser_en-US$
Now, you are ready to use your Tor browser in Kali Linux.
Uninstalling the Tor browser from Kali Linux
There are two ways through which the uninstallation process can be carried
1) By using Command
“sudo apt remove torbrowser-launcher”
2) By manual Deletion
Go to the Directory of Tor browser and right-click and “delete”. This will uninstall and delete the Tor Browser from the system.
Configuring Tor Browser on Kali Linux
After launching the Tor browser on Kali Linux, there are some settings that users might configure according to their preference to prioritize security and privacy:
Language and appearance:
After launching the Tor browser, users can choose the language according to their preference and customize the appearance by setting themes, fonts, and toolbar visibility.
Connection to the Tor network:
After launching, the Tor browser automatically connects to the Tor network. It is, by default, configured to use the Tor network and select the required relays to anonymize the browser. To confirm the connection to the Tor network, the user can visit the check.torproject.org website; this website displays messages for successful connection, ensuring user traffic anonymization.
Security level:
The Tor browser provides three different security levels to protect user’s privacy, and users can configure security levels according to their requirements from security level settings from the Tor browser shield icon.
- Standard: The standard security level comes within the default setting. It provides a user-friendly interface with most website functionalities and features.
- Safer: This is the second security level with more security. Disable some website features, such as automatic media playback and JavaScript on non-HTTPS
- Safest: This is the highest security level with more security; it disables most website features and only allows basic functionalities for static websites.
Privacy:
The Tor browser also provides various privacy settings to configure, such as preventing websites from accessing a user’s location, blocking third-party cookies, and disabling features that might reveal a user’s online identity.
Troubleshooting
A few issues might emerge while downloading and installing the Tor browser on Kali Linux. Let us discuss the possible problems and their optimal solutions.
1) Low Internet connection and incomplete downloads:
Due to a low Internet connection, packages may not download with all their properties, and this causes flaws in the functioning of the Tor browser. Always have a strong internet connection to download all the packages correctly.
2) Outdated system:
When installing, if the system is outdated, it causes package conflicts and issues with missing dependencies. To solve this issue before installing, update the system using “sudo apt update’.
3) Sudo access:
The superuser does, or sudo, is a must for installing new software in a Linux environment. So always have sudo access; if one doesn’t have one, use the command “apt install sudo” to get the sudo access in your Linux environment.
4) Inefficient space:
Due to inefficient space, the installation will start but will discontinue in between due to low memory space on the disk. Check your memory space on disk by using the command “free –h”. This will display the total available and used memory in megabytes (MB) and gigabytes (GB).
Advanced Usage and Tips
-Utilizing Tor bridges
- In some regions where Tor is actively blocked or monitored, users use Tor bridges to evade the restrictions. The Tor network can be accessed in a restricted environment with bridges where relays are not listed publicly, making detecting and blocking Tor usage challenging.
- For using Tor bridges, there is an option in the Tor Browser’s network setting where users can select and enter bridge addresses from trusted sources.
-Managing Tor circuits
- Tor circuits depict the paths for user traffic throughout the Tor network. Users can manage and manually control the Tor circuit to optimize performance and anonymity. Controlling how the Tor circuit works will prioritize speed or configure for specific nodes or countries for routing.
- The Tor circuit display feature, accessible through the browser toolbar, allows users to view and manage the Tor circuit to ensure efficient traffic distribution and monitor routing paths.
-Using Tor over VPN for added security
- Integrating Tor with VPN adds extra security and an encryption layer for enhancing privacy and anonymity.
- The system configuration for traffic is routed through a VPN connection, this effectively obscures the origin of internet traffic by twice encryption, mitigating the risk and masking Tor usage from ISPs
- Users should be knowledgeable about compatibility issues, as using Tor over VPN may impact connection speed and lead to complexity in network configuration.
-Clearing cookies and browsing history:
Users should frequently clear their browsing history, cookies, and cache to maintain privacy while browsing through Tor. The attacks may use the browsing data to track the user’s activity and identity.
The Tor browser has a built-in feature for clearing browsing data, which is available in the browser’s privacy settings. It allows users to use browser settings to automatically delete cookies and browser history while exiting the browser to minimize tracking.
Conclusion
The Tor browser on Kali Linux provides online Freedom and safeguards sensitive information.
The users can access restricted content and bypass the internet censorship imposed by a strict government censorship regime. Anonymous browsing allows users to explore the web without boundaries and ensure online activity and identity security.
Frequently Asked Questions (FAQs)
1) Can the Tor browser be configured to use a specific exit node?
Answer: Configuring specific exit nodes in the Tor browser is highly discouraged. Tor architecture relies on randomly selecting middle and exit nodes, maintaining anonymity and security. Controlling and monitoring specific exit nodes compromise the security provided by the Tor network and increases the risk of exposing nodes and identifying the traffic pattern. Tor default path selection offers the best protection and anonymity.
2) What is ISP, and how does TOR protect itself from ISP?
Answer: ISP stands for Internet service provider, and these service providers can monitor user activities. But in the case of the Tor browser, the ISP cannot track our activities because internet traffic is routed through a series of volunteered-operated servers. However, if the user logs into the account using identifications, security vulnerabilities are possible.
3) Which countries have banned the use of the Tor browser?
Answer: Some countries have banned the use of the Tor browser for different reasons.
- China has banned the Tor browser because it wants access to its citizens’ online activities.
- Iran has curbed access to Tor and similar tools because it needs to track its citizen’s online activities.
- Other countries like Russia, Belarus, and Turkmenistan have curbed access to the Tor browser.
Recommended Articles
We hope that this EDUCBA information on “Tor Browser Kali Linux” was beneficial to you. You can view EDUCBA’s recommended articles for more information.