Virtual Private Network (VPN) Meaning
A VPN or Virtual Private Network is a service that helps you to create a secure and encrypted connection over the internet. It enables users to access a private network, such as their work network or the internet while ensuring their data remains private and protected from unauthorized access or surveillance.
To understand what VPN means, let’s take an example:
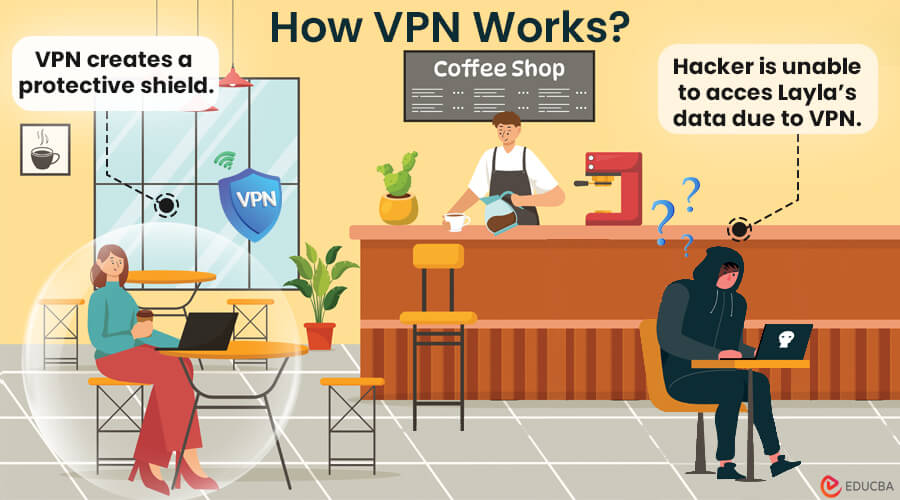
Imagine Layla, an enthusiastic online shopper, realizing that her private information could be at risk from cybercriminals. Seeking a robust solution, she invests in a VPN. Now, picture Layla in a café, using their Wi-Fi to buy something online. Little does she know, a sneaky hacker is nearby trying to grab her information. But the VPN notices and stops the hacker from getting in. Layla’s data stays safe, and she finishes buying without any trouble. The VPN turns out to be her digital protector, ensuring her data is safe online, especially with all the tricky cyber crimes happening.
In this article, we will discuss everything about VPNs and additional security measures to ensure your online security is top-notch.
Table of Contents (TOC)
How Does a Virtual Private Network Work?
A VPN builds a safe and coded path between your device and its server. Here’s how a VPN works:
Step 1: Encrypting Your Data
When you use a VPN, your device secures all the information you send and receive by turning it into a secret code. This code, or encryption, makes it tough for anyone to understand your data without the right key.
Step 2: Sending Data Safely
The encrypted data travels through a safe passage, like a secret tunnel, to the VPN server. This tunnel shields your information from anyone trying to mess with it.
Step 3: Decoding at the VPN Server
After the VPN server receives the data, it decodes it. This server then sends your information out onto the internet in its regular form.
Step 4: Privacy Protection
VPN keeps your online actions private by hiding your IP address. This way, others can’t easily trace what you are doing.
Step 5: Accessing Restricted Content
VPN lets you get around restrictions on certain websites or content based on your location. Pretending to be in a different place enables you to access content blocked in your location. For example, using a VPN Russia allows you to bypass local internet censorship and access websites that are restricted within Russia.
Benefits of Using a Virtual Private Network
There are various benefits for users of using a VPN, as follows:
1) Privacy and Security
Using a VPN has a big advantage because it makes your online activities more private and secure. When you use a VPN, it scrambles your internet data, making it unreadable to your internet service provider (ISP), government, advertisers, cybercriminals, and others. It means they can’t spy on or grab your sensitive information. It also stops them from following your online behavior and gathering your data.
2) Security On Public Wi-Fi
Using public networks puts your online accounts and financial transactions at risk of cyberattacks and interception. Be careful when using public Wi-Fi, as it is easy for people with bad intentions to get hold of your sensitive information. Consider using a VPN when connected to public networks to enhance your online security.
3) Bypassing Geolocation Restrictions
A VPN helps you access content and streaming services that might be restricted in your location due to authority blocks. It lets you connect to servers in different locations, tricking websites into thinking you are in a different place. It lets you avoid restrictions and access content limited to specific regions, such as certain shows on streaming or social media platforms.
4) Secures Remote Access
Since the COVID-19 pandemic, working from home has become common. This shift raised security worries for companies as employees needed to access company networks remotely. VPNs help by providing a secure way for remote workers to connect to the company’s network, especially when accessing sensitive information while traveling or working from home.
5) Cost-Effective Measures
Using a VPN saves your money by tricking websites into thinking you are in a different location. Some places offer lower prices for the same things, so you can connect to a server in a cheaper location and take advantage of the cost savings. Additionally, a free VPN can provide these benefits without any cost, making it an even more attractive option for budget-conscious users.
Factors to Consider when Choosing a VPN
When choosing a VPN, look for online security with the fastest VPN that suits your requirements and keeps your online activities secure. Here are the most critical factors and features that a VPN must have:
1) No-Logs Policy
A good VPN should have a strong No-Logs Policy, meaning it doesn’t record what you do online or the websites you visit while using the VPN. It should delete any recorded data as soon as you disconnect from the VPN. Additionally, considering the location of the VPN provider is crucial because different places have different laws about how long they can retain data.
2) Security Features
Ensure your VPN service has strong encryption (like AES-256) and secure tunneling protocols (such as OpenVPN or IKEv2). Look for additional safety features like a Kill Switch, which stops your internet connection if the VPN disconnects suddenly, keeping your data secure and avoiding leaks.
3) Extensive Server Network
Choose a VPN with many servers because having more allows you to get around location restrictions easily and can improve performance by preventing congestion. Ensure the VPN provider has servers in places that can help you access content blocked in certain regions.
4) Device Compatibility
The VPN service should work on various devices like iOS, Android, macOS, Windows, and Linux. Some VPN providers offer apps for all devices, while others provide step-by-step guides for manual setup on compatible devices.
5) Customer Support
The VPN service should have a reliable customer support team that can quickly help with any technical questions. They should be available through phone, email, and live chat channels. Additionally, the VPN provider should offer user-friendly guides and tutorials to assist customers in using the VPN app and understanding its features.
6) Connection Speed & Performance
Check the speed and performance the VPN service provider offers to ensure it suits your requirements. It is crucial for streaming HD videos, playing online games, or downloading large files. Choose a VPN with fast servers and low latency to ensure a smooth, uninterrupted gaming and streaming experience.
Protocols of VPN
1. PPTP (Point-to-Point Tunneling Protocol)
PPTP, or Point-to-Point Tunneling Protocol, is utilized on Windows NT systems. It facilitates a virtual private network connection between a single user and a local area network (LAN). However, it doesn’t support LAN-to-LAN connections.
2. L2TP (Layer 2 Tunneling Protocol)
L2TP, or Layer 2 Tunneling Protocol, is an enhanced version of PPTP developed by IETF. It is known as a safe and widely accepted standard for creating virtual private network connections. L2TP supports connections between a single user and a LAN and LAN-to-LAN connections.
3. IPSec (Internet Protocol Security)
IPSec provides authentication and confidentiality services, ensuring secure communication. It is commonly used in isolation to enhance the security of data transmissions.
Is A VPN The Most Secure Method?
While VPNs help boost privacy and security by hiding IP addresses and encrypting internet traffic, but they also have limitations. VPNs alone cannot safeguard against various online threats like viruses, malware, trojans, ransomware, and adware. It is important to use VPNs with reliable antivirus software to achieve comprehensive protection. Antivirus software actively scans for online threats, detects them in real time, and removes them from your device. Whether connected to a VPN or not, these threats can still harm your device and compromise sensitive data. Therefore, for a well-rounded defense, it is essential to combine VPNs for privacy with antivirus software for protection against malicious software and phishing sites.
Final Thoughts
A Virtual Private Network offers a secure and encrypted online experience, protecting users like Layla from cyber threats. Its benefits include privacy, security on public Wi-Fi, ignoring location restrictions, secure remote access, and potential cost savings. So, whether you are shopping, working remotely, or accessing restricted content, a VPN adds an extra layer of security in this increasingly digital world.
Recommended Articles
We hope this article on “Virtual Private Network” was helpful to you. You can also refer to the articles below to learn more.