Updated August 5, 2023
Introduction to Kerberos
The following article provides an outline for Kerberos. Kerberos is a computer network authentication protocol. MIT designed it to allow network resources securely.
How does Kerberos Work?
Kerberos works in three steps.
Step 1: Log in
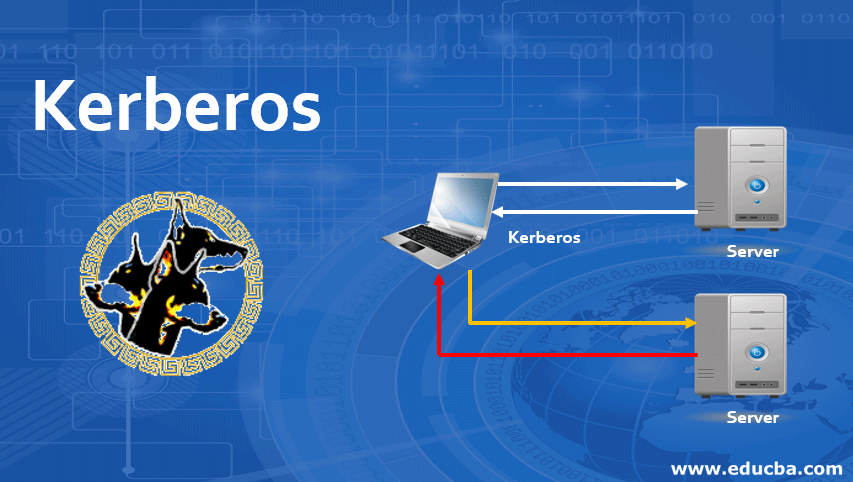
The client enters his name at an arbitrary workstation. Then workstation sends the name to the authentication server in plain text format.
In response, the Authentication server performs some action. First, it creates the package of user name, i.e. client, and generates the session key. It encrypts this package with a symmetric key that the authentication server shares with Ticket Granting Server(TGS). The output of this process is called a Ticket Granting Ticket (TGT). The authentication server then combines TGT and session keys and encrypts them together using the symmetric key derived from the client’s password.
After receiving this message, the user’s workstation asks for the password. When a user or client enters his password, the workstation generates the symmetric key derived from an authentication server’s password. This key is used to extract the session key and TGT. After that, the workstation destroys the client’s password from its memory to prevent the attack.
Step 2: Obtaining a Service Granting Ticket
After the successful login, let’s assume that the user wants to communicate with other users through the mail server.
For that client to inform his workstation that he wants to contact another user X., the client needs a ticket to communicate with X. At this point, the client workstation creates a message intended for a ticket-granting server, which contains the below-mentioned items:
- Ticket granting ticket.
- The id of the X whose services clients are interested in.
- The current timestamp should be encrypted with the same session key.
Ticket granting, the ticket is encrypted only with the secret key of the ticket-granting server; hence only the ticket-granting server can open a ticket-granting ticket because the ticket-granting server believes the message comes from the indeed client. The session authentication server encrypted the ticket-granting ticket and session key.
An authentication server encrypts it using the secret key derived from the client’s password. Hence only the client can open the package and retrieve the Granting ticket.
Once the ticket-granting server is satisfied with the details entered by the client, the ticket-granting ticket creates a session key KAB for the client to perform the secure communication with X. Ticket Granting Server sends it twice to the client – the first time it sends when combined with X’s id and encrypted with the session key, the second time it sends when combined with client id’s and encrypted with X’s secret key KB.
In this case, the attacker can try to obtain the client’s first message and attempt a reply attack. However, this would fail as the client message contains an encrypted timestamp, and the attacker cannot replace the time stamp as he does not have the session key.
Step 3: User Contacts X for Accessing the Server
A client sends KAB to X to create a session with X. For secure communication, the client forward KAB encrypted with X’s secret key to X. X can access KAB. To protect from a reply attack, the client sends a timestamp to X, encrypted with KAB. X uses his secret key to obtain the information; he uses KAB to decrypt the stamp value from this information. Then X adds 1 to the timestamp value, encrypts it using KAB, and sends it to the client. The client then opens the packet and verifies the stamp incremented by X. From this process; the client ensures that X received the same KAB the client sends.
Now client and X can communicate with each other securely. Both use a shared secret key KAB to encrypt the data when sending and decrypt the message using the same key. Suppose that the client may want to communicate with another server Y; in that case, the client n3d to obtain another secret key from the Ticket Granting Server. After receiving the secret key, he can communicate with Y similarly, as we have discussed in the case of X. If the client may communicate again with X, he can use the same previous key; there is no need to generate a ticket every time, only for the first time he needs to obtain the ticket.
Advantages and Disadvantages of Kerberos
Given below are the advantages and disadvantages:
Advantages:
- Clients and services mutually authenticate in Kerberos.
- Various operating systems support it.
- Tickets in Kerberos have a limited period. If the ticket gets stolen, it is hard to reuse it because of strong authentication needs.
- Passwords are never sent over the network unencrypted.
- In Kerberos, secret keys are shared, which is more efficient than sharing public keys.
Disadvantages:
- It is vulnerable to weak or repeated passwords.
- It only provides authentication for services and clients.
Conclusion
In this article, we have seen what Kerberos is, how it works, and its advantages and disadvantages.
Recommended Articles
This is a guide to Kerberos. Here we discuss the introduction, how does kerberos works, advantages & disadvantages respectively. You can also go through our other suggested articles to learn more –