Introduction
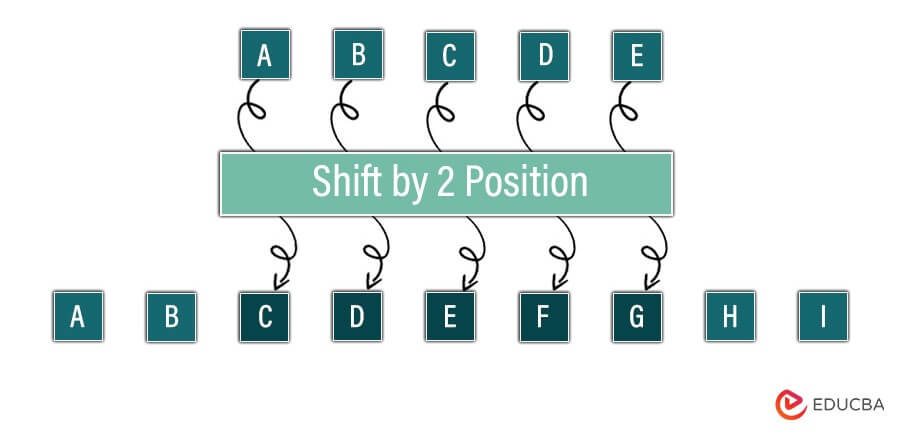
The Caesar Cipher Program in Java is a cryptographic tool that encodes and decodes messages using a simple substitution method. It shifts each letter in the message by a fixed number of positions down or up the alphabet. This program accepts user input for the message and the shift value. Through Java’s string manipulation capabilities, it efficiently processes the text, ensuring secrecy and confidentiality in communication. With its intuitive interface and reliable encryption method, the Caesar Cipher Program is a fundamental tool for understanding and implementing basic encryption techniques in Java applications, making it a valuable resource for learners and professionals alike.
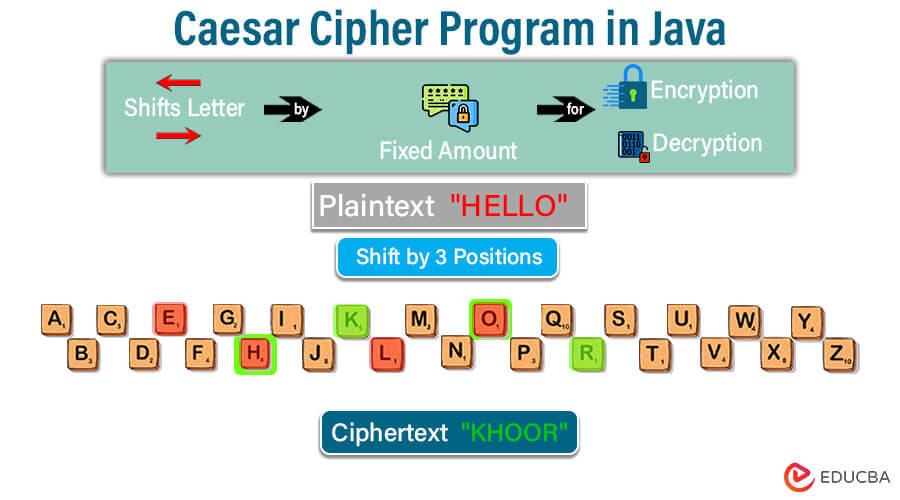
Table of Contents
Key takeaways
- The Caesar Cipher Program in Java facilitates basic encryption via letter substitution.
- It encrypts and decrypts messages by shifting letters by a predefined number of positions.
- User input dictates both the message and the shift value for encryption.
- Leveraging Java’s string manipulation capabilities ensures effective message processing.
- It is a valuable educational tool for grasping encryption fundamentals and Java application development.
- Offers practical insights into encryption principles and their real-world applications for data protection.
Setting Up the Java Development Environment
- Installing the Java Development Kit (JDK):
- Go to the Oracle JDK download page or the AdoptOpenJDK website.
- Download the appropriate JDK installer for your operating system.
- Observe the installation guidelines that the installer has supplied.
- After installation, set the JAVA_HOME environment variable to the JDK installation directory.
- Selecting an Integrated Development Environment (IDE):
- Download and install an IDE such as Eclipse, IntelliJ IDEA, or NetBeans from their respective official websites.
- Launch the IDE after installation.
- Configure any initial settings or preferences as needed.
- Configuring the IDE:
- Ensure that the IDE recognizes the installed JDK. You may need to specify the JDK location in the IDE’s settings.
- Set up any additional plugins or extensions required for Java development, such as Maven or Gradle support.
- For your Caesar Cipher Program, open the IDE and create a new Java project.
- Adding Libraries and Dependencies:
- If your program requires external libraries, download the necessary JAR files from their official sources.
- Add these JAR files to your project’s IDE build path or dependencies settings.
- Setting up Version Control (Optional):
- Install Git on your system if you haven’t already.
- Make sure your project has a new Git repository created.
- Initialize version control in your project directory.
- Add and commit your project files to the repository.
Encryption And Decryption:
EquationImplementing the Caesar Cipher in Java
Encryption Process:
- Input Message: Receive the message to be encrypted as input.
- Select Shift Value: Choose a fixed shift value, denoted by ‘k,’ which determines the time each letter in the message will be shifted in the alphabet. This value can be any integer between 1 and 25.
- Iterate Through Message: Iterate through each character in the message.
- Shift Characters: For each character, shift its ‘k’ positions to the right in the alphabet. Ensure that the shift wraps around the alphabet if it exceeds ‘z’ (or ‘Z’ for uppercase letters).
- Handle Non-Alphabetic Characters: Leave it unchanged if the character is not alphabetic.
- Output Encrypted Message: Output the modified message, which is now encrypted using the Caesar Cipher.
Example:
import java.util.Scanner;
public class CaesarCipher {
public static void main(String[] args) {
Scanner scanner = new Scanner(System.in);
// Step 1: Receive the message to be encrypted as input
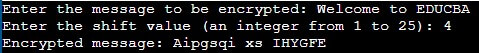
System.out.print("Enter the message to be encrypted: ");
String message = scanner.nextLine();
// Step 2: Select Shift Value
System.out.print("Enter the shift value (an integer from 1 to 25): ");
int shiftValue = scanner.nextInt();
scanner.nextLine(); // Consume newline character
// Step 3: Iterate Through Message, Step 4: Shift Characters
String encryptedMessage = encryptMessage(message, shiftValue);
// Step 5: Output Encrypted Message
System.out.println("Encrypted message: " + encryptedMessage);
scanner.close();
}
public static String encryptMessage(String message, int shiftValue) {
StringBuilder encryptedMessage = new StringBuilder();
for (int i = 0; i < message.length(); i++) {
char originalChar = message.charAt(i);
char encryptedChar;
if (Character.isLetter(originalChar)) {
char base = Character.isUpperCase(originalChar) ? 'A' : 'a';
encryptedChar = (char) (((originalChar - base + shiftValue) % 26) + base);
} else {
// Step 4: Handle Non-Alphabetic Characters
encryptedChar = originalChar;
}
encryptedMessage.append(encryptedChar);
}
return encryptedMessage.toString();
}
}Output:
Decryption Process:
- Input Encrypted Message: Receive the encrypted message as input.
- Select-Shift Value: Use the same shift value ‘k’ used for encryption. It ensures proper decryption.
- Iterate Through Encrypted Message: Iterate through each character in the encrypted message.
- Reverse Shift Characters: For each character, shift its ‘k’ positions to the left in the alphabet. For characters beyond ‘a’ (or ‘A’ for uppercase letters), handle wrapping around the alphabet like encryption.
- Handle Non-Alphabetic Characters: Non-alphabetic characters remain unchanged.
- Output Decrypted Message: Output the modified message, which is now decrypted back to its original form using the Caesar Cipher.
import java.util.Scanner;
public class CaesarCipher {
public static void main(String[] args) {
Scanner scanner = new Scanner(System.in);
// Step 1: Receive the encrypted message as input
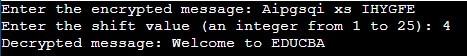
System.out.print("Enter the encrypted message: ");
String encryptedMessage = scanner.nextLine();
// Step 2: Use the same shift value used for encryption
System.out.print("Enter the shift value (an integer from 1 to 25): ");
int shiftValue = scanner.nextInt();
scanner.nextLine(); // Consume newline character
// Step 3: Iterate Through Encrypted Message
// Step 4: Reverse Shift Characters
String decryptedMessage = decryptMessage(encryptedMessage, shiftValue);
// Step 5: Output Decrypted Message
System.out.println("Decrypted message: " + decryptedMessage);
scanner.close();
}
public static String decryptMessage(String encryptedMessage, int shiftValue) {
StringBuilder decryptedMessage = new StringBuilder();
for (int i = 0; i < encryptedMessage.length(); i++) {
char encryptedChar = encryptedMessage.charAt(i);
char decryptedChar;
if (Character.isLetter(encryptedChar)) {
char base = Character.isUpperCase(encryptedChar) ? 'A' : 'a';
// Reverse shift operation
decryptedChar = (char) (((encryptedChar - base - shiftValue + 26) % 26) + base);
} else {
// Step 4: Handle Non-Alphabetic Characters
decryptedChar = encryptedChar;
}
decryptedMessage.append(decryptedChar);
}
return decryptedMessage.toString();
}
}Output:
Code Structure:
The structure and functionality of a simple Caesar cipher implementation are as Follows
- Main Method:
- It takes input messages and shifts values for the user.
- Calls the encrypt method to encrypt the message.
- Calls the decrypt method to decrypt the encrypted message.
- Prints both the encrypted and decrypted messages.
- Encrypt Method:
- Accepts the message and shift value as parameters.
- Iterates through each character in the message.
- Shifts alphabetic characters by the specified shift value.
- Handles non-alphabetic characters without modification.
- Returns the encrypted message.
- Decrypt Method:
- It accepts the encrypted message and shifts the value as a parameter.
- Iterates through each character in the encrypted message.
- Reverses the shift operation to decrypt the message.
- Handles non-alphabetic characters without modification.
- Returns the decrypted message.
Let us take an Example to understand Implenting better using Java programming language.
Code:
import java.util.Scanner;
public class CaesarCipher {
public static void main(String[] args) {
Scanner scanner = new Scanner(System.in);
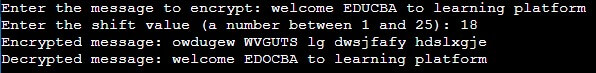
System.out.print("Enter the message to encrypt: ");
String message = scanner.nextLine();
System.out.print("Enter the shift value (a number between 1 and 25): ");
int shift = scanner.nextInt();
scanner.nextLine(); // Consume newline
String encryptedMessage = encrypt(message, shift);
System.out.println("Encrypted message: " + encryptedMessage);
String decryptedMessage = decrypt(encryptedMessage, shift);
System.out.println("Decrypted message: " + decryptedMessage);
scanner.close();
}
public static String encrypt(String message, int shift) {
StringBuilder encrypted = new StringBuilder();
for (char c : message.toCharArray()) {
if (Character.isLetter(c)) {
char base = Character.isLowerCase(c) ? 'a' : 'A';
char shiftedChar = (char) (((c - base + shift) % 26) + base);
encrypted.append(shiftedChar);
} else {
encrypted.append(c);
}
}
return encrypted.toString();
}
public static String decrypt(String encryptedMessage, int shift) {
StringBuilder decrypted = new StringBuilder();
for (char c : encryptedMessage.toCharArray()) {
if (Character.isLetter(c)) {
char base = Character.isLowerCase(c) ? 'a' : 'A'; // Determine base character
char shiftedChar = (char) (((c - base - shift + 26) % 26) + base); // Reverse the shift
decrypted.append(shiftedChar);
} else {
decrypted.append(c);
}
}
return decrypted.toString();
}
}Output:
Explanation:
In this implementation, the program takes a message and a shift value as input from the user, encrypts the message using the Caesar Cipher technique, and then decrypts it back to the original message. Finally, it prints both the encrypted and decrypted messages.
Testing and Using the Program
Testing the Caesar Cipher Program involves providing various inputs and verifying the corresponding outputs to ensure the correctness and effectiveness of the encryption and decryption processes. Here are some sample inputs along with their expected outputs:
Sample Inputs and Outputs:
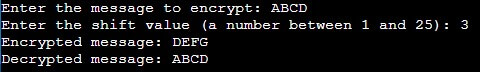
Test Case 1
Input
Message: “ABCD”
Shift Value: 3
Output:
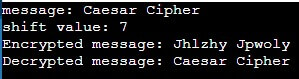
Test Case 2
Input
Message: “Caesar Cipher”
Shift Value: 7
Output:
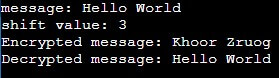
Test Case 3
Input:
Message: “Hello World”
Shift Value: 3
Output:
By testing with diverse inputs, including different messages and shift values, the program’s functionality and robustness can be thoroughly evaluated.
Limitations of the Caesar Cipher:
- Vulnerable to brute force attacks: With only 25 possible keys (assuming the English alphabet), the Caesar Cipher can be easily cracked by trying all possible combinations.
- Lack of robustness: Due to its simple nature of shifting letters, the Caesar Cipher cannot handle complex encryption requirements and fails to provide strong security against modern cryptographic attacks.
- Limited key space: The small key space makes it susceptible to frequency analysis, where the frequency of letters in the ciphertext can be used to deduce the shift value and decrypt the message.
- Inability to encrypt numbers and special characters: The Caesar Cipher works only on alphabetic characters, leaving numbers, symbols, and special characters unaffected. This limits its applicability to encrypting diverse data types.
- Known plaintext vulnerability: If attackers can access the plaintext and corresponding ciphertext, they can easily derive the key used in the encryption process, compromising the cipher’s security.
- Not suitable for sensitive data: Given its inherent vulnerabilities and susceptibility to attacks, the Caesar Cipher is not recommended for encrypting sensitive information or communication requiring high confidentiality and security levels.
Extensions and Variations
- Handling Uppercase Letters: Extend the Caesar Cipher program to handle uppercase letters by incorporating a condition to differentiate between lowercase and uppercase characters during encryption and decryption. It ensures versatility in encrypting messages containing both uppercase and lowercase letters, enhancing the applicability of the cipher.
- Adjustable Character Sets: Modify the Caesar Cipher implementation to accommodate adjustable character sets beyond the standard English alphabet. This extension enables the encryption of messages containing non-alphabetic characters, numbers, and special symbols. The cipher’s versatility and usefulness are significantly enhanced by allowing users to specify the character set or automatically detect and encrypt a broader range of characters.
- Polyalphabetic Substitution: Implement a polyalphabetic substitution cipher, such as the Autokey Cipher or the Beaufort Cipher, which uses multiple cipher alphabets instead of a single fixed shift value. This approach increases the encryption process’s complexity and strengthens the cipher’s security against attacks like frequency analysis. Incorporating polyalphabetic techniques makes the cipher more resilient and adaptable to modern cryptographic challenges.
- Customizable Shift Values: Extend the Caesar Cipher program to support customizable shift values for each character in the message. This feature allows users to define unique shift values based on specific encryption requirements or preferences, offering greater flexibility and control over the encryption process. By enabling customizable shift values, the cipher becomes more versatile and capable of effectively addressing a wider range of encryption scenarios.
Conclusion
The Caesar Cipher Program in Java offers a foundational understanding of encryption techniques. While simple, its implementation provides insight into cryptographic principles. However, its susceptibility to brute force attacks and limited security features underscores the need for more robust encryption. Nonetheless, the program is an educational tool for beginners and a starting point for exploring advanced encryption algorithms. With further enhancements and understanding, it lays the groundwork for more secure communication systems in the digital age.
Frequently Asked Questions (FAQs)
Q1: How does the Caesar Cipher program handle non-alphabetic characters in the input message?
Answer: The Caesar Cipher program in Java preserves non-alphabetic characters that are unchanged during encryption and decryption. It identifies non-alphabetic characters in the input message and leaves them unmodified in the output, ensuring that punctuation, numbers, and special symbols remain unaffected by the encryption process.
Q2: Can the Caesar Cipher program in Java handle messages with varying shift values for different characters?
Answer: No, the Caesar Cipher program in Java applies a uniform shift value to all characters in the input message. It encrypts and decrypts the entire message using the same shift value specified by the user. While this simplicity ensures ease of implementation, it limits the program’s ability to handle complex encryption scenarios requiring different shift values for distinct characters.
Q3: Is it feasible to enhance the security of the Caesar Cipher program by integrating additional cryptographic techniques?
Answer: Yes, although the Caesar Cipher is relatively simple, it can be augmented with supplementary security measures. For instance, implementing a key generation mechanism to generate shift values dynamically or combining the Caesar Cipher with other encryption algorithms, such as the Vigenère Cipher or modern symmetric-key ciphers, can bolster its resistance against cryptographic attacks and enhance overall security.
Recommended Article
We hope that this EDUCBA information on “Caesar Cipher Program in Java” was beneficial to you. You can view EDUCBA’s recommended articles for more information,