Introduction to Proxy Servers
Proxy Servers are referred to those servers that act as an intermediary to the request made by clients to a particular server for some services or request for some resources. Several types of proxy servers are available whose use will depend on the purpose of a request made by the clients to the servers. The purpose of Proxy servers is to Protects the direct connect of Internet clients and internet and internet resources: Proxy server prevents the identification of the client’s IP address while any request is made to any other servers.
- Internet clients and internal resources: Proxy servers also act as a shield for an internal network against the request coming from a client to access the data on that server. The original IP address of the node remains hidden while accessing data from that server.
- Protects true host identity: Outgoing traffic appears to come from the proxy server. It must be configured to the specific application, e.g. HTTPS or FTP.
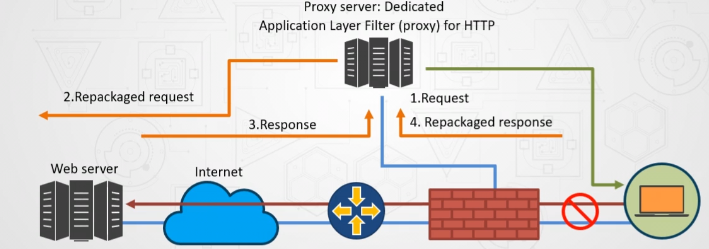
For example, as a client to MNC, a client can use a proxy service to observe its contract employees’ traffic to get the work efficiently done. It can also be used to keep a check on any leakage of internal highly confidential data. Some can also use it to increase their websites rank and get the traffic diverted anonymously.
The need for Private Proxy
Some of the need for a private proxy is mentioned below:
Defeat Hackers
Every organization has its own personal data that needs to be protected from malicious use. Thus, passwords are used, and different architectures are set up, but there is still a possibility that this information can be hacked if the IP address is accessible easily. Proxy servers are set up to prevent tracking of the original IP address; instead, data is shown to come from a different IP address. Tools like Multilogin’s anti-detect browser further enhance online security by enabling businesses to manage multiple virtual identities and mask their digital footprint effectively, adding an additional layer of protection.
Filtering of the Content
Proxy servers also help filter out the content that doesn’t follow the web application’s policies or server required. It provides a facility to authenticate the user and provides the logs of URL of users requests made through that proxies.
Content can be Cached.
The proxy also helps in caching the content of the websites. This helps in fast access to the data that has been accessed oftenly.
Examine Packet Headers and Payloads
We can also examine the payloads and packet headers of the nodes in the internal server’s requests so that any access to social websites can be easily tracked and restricted.
Types of Proxy Servers
Below are the different types of proxy servers:
1. Reverse Proxy
This represents the server. In case there are multiple websites on different servers, then it is the job of a reverse proxy server to listen to the client’s request and redirect to the particular web server.
Example – Listen for TCP port 80 website connections. These are normally placed in a DMZ zone for publicly accessible services and protect the host’s true identity. It is transparent to the external users as external users will not be able to identify the actual number of internal servers. It is the duty of reverse proxy to redirect the flow depending on the configurations of internal servers. The request made to pass through the private network protected by firewalls needs a proxy server that does not abide by any local policies. This type of request from the clients are completed using reverse proxy servers. This is also used to restrict the client’s access to the sensitive data residing on the particular servers.

2. Web Proxy Server
This type of proxies forward the HTTP requests. This request is the same as HTTP requests; only URL is passed instead of a path. A request is sent to which the proxy server responds. Examples of such proxies are Apache, HAPProxy. Web proxy servers are also used by businesses for several purposes, like keeping track of competitors, scraping data and building AI Solutions.
The client-server Proxy auto-config protocol solves the solution to the problems of multiple proxy servers.
3. Anonymous Proxy
This is the type of proxy server that does not makes an original IP address. Although these servers are detectable still provides rational anonymity to the client device.
Similar to anonymous proxies, mobile proxies also offer a degree of anonymity by masking the user’s real IP address with an IP address provided by a mobile carrier. For a deeper understanding of how mobile proxies work and their benefits, you can refer to this comprehensive guide on some of the best mobile proxies available. For those looking to compare and purchase reliable proxies, ProxyCoupons offers a selection of deals on high-quality proxy services to suit different needs.
4. High Anonymity Proxy
This proxy server does not allow the original IP address to be detected, and no one can detect it as a proxy server.
5. Transparent Proxy
This type of proxy server never provides any anonymity to the client; instead, an original IP address can be easily detected using this proxy. Still, it is being used to act as a cache for the websites.
A transparent proxy combined with gateway results in a proxy server where the client IP’s connection requests are redirected. This redirection occurs without the client IP address configuration. This redirection can be easily detected by the HTTP headers present on the server-side.
These are also known as intercepting proxies, inline proxy, and forged proxy.
Working: It intercepts the communication at the network level without the need for any configuration. It also works as a gateway or router that authenticates the communication without making any changes to the requests or responses passing through the server.
Uses: These types of proxies are most commonly used at the business level to enforce the policy over communication. It also tries to prevent any attack on TCP servers example – denial-of-service attack.
6. CGI Proxy
This type of proxies was developed to make the websites more accessible.
Working: It accepts the requests to target URLs using a web form, processes it and returns the result to the web browser. It is less popular due to VPNs and other privacy policies, but it still receives many requests these days. Its usage reduces because of excessive traffic that can be caused to the website after passing the local filtration, leading to collateral damage to the organization.
7. Suffix Proxy
This type of proxy server appends the proxy’s name to the URL to the content that has been requested to the proxy. This type of proxy doesn’t preserve a higher level of anonymity.
Uses: It is used for bypassing the web filters. This proxy is easy to use and can be easily implemented but is used less due to more or more web filters.
8. Distorting Proxy
Proxy servers can generate an incorrect original IP address of clients once being detected as a proxy server. It uses HTTP headers to maintain the confidentiality of the Client IP address.
9. Residential Proxy
Residential proxies use IP addresses that Internet Service Providers provide to individuals at home. They mimic real user actions, making them useful for activities like web scraping.
Residential proxies use IP addresses from ISPs, making them highly effective for web scraping and ensuring secure data transmission. Opting for reliable residential proxies can help avoid IP bans and bolster anonymity while accessing target websites. They also mimic real user actions, contributing to their effectiveness in evading detection.
10. TOR Onion Proxy
It is software that aims at online anonymity to the user’s personal information.
Working: It routes the traffic through various networks present worldwide to make it difficult to track the users’ address and prevent the attack of any anonymous activities. It makes it difficult for any person who is performing traffic analysis to track the original address. For this, it uses ONION ROUTING.
In this type of routing, the information is encrypted in a multi-folds layer by layer to prevent it. At the destination, each layer is decrypted to prevent the information from scrambling or getting distorted.
This software is open source as well as free of cost to use.
11. I2P Anonymous Proxy
It is an anonymous network enhanced version of the Tor onion proxy, which uses encryption to hide all the communications at various levels. This encrypted data is then relayed through various network routers present in different locations. Thus I2P is a fully distributed proxy that aims at online anonymity. It also implements garlic routing. (enhanced version of Tor’s pnion routing. It provides a proxy to all protocols. This type of proxies can be run on the node.
I2P router finds other peers to build an anonymous identity to protect the user’s personal information.
This software and network are free of cost and open source to use; It also resists censorship.
12. DNS Proxy
Unlike other proxies, this type of proxy takes requests in the form of DNS queries and forward them to the Domain server, where they can also be cached, and the flow of requests can also be redirected.
Types of Proxy Servers (Protocols)
Below are the different types of proxy servers protocols:
- Socks Proxy Server: This type of proxy server provides a connection to a particular server. Depending on Socks protocols, this type of server allows the multilayering of various data types such as TCS or UDP.
- FTP Proxy Server: This type of proxy server caches FTP requests’ traffic and uses the concept of relaying.
- HTTP Proxy Server: This proxy was developed to process a one-way request to the web pages using HTTP protocols.
- SSL Proxy Server: This type of server was developed using the concept of TCP relaying being used in the SOCKS proxy protocol to allow Web Pages’ requests.
Conclusion
Proxy servers help in various anonymity types required at different levels, either as a client or as a service provider. It helps to resist the security of information of various users as well as the internal network. Different types of proxies are available, which follow various routing protocols and serve different uses at different anonymity levels.
Proxifiers are the client programs that allow the adaptation of any type of software used for networking using various types of proxy servers.
Recommended Articles
This is a guide to Types of Proxy Servers. Here we discuss the basic concept, need, types and various protocols of Proxy Servers in detail. You can also go through our other suggested articles to learn more –


