Updated March 17, 2023
Difference Between SSH and SSL
As there are many doors and windows open, hackers and eavesdroppers may secretly collect your personal data and access your own sensitive applications and files. So now people are asking for site security. SSH and SSL are joined. For the safe transmission of critical information such as credit cards and banking, SSL is mainly used. In comparison, SSH can execute commands securely throughout the Internet. In order to establish a secure connection, SSH uses the username/password authentication system, although SSL does not bode.
Head to Head Comparison Between SSH and SSL (Infographics)
Below are the top 8 differences between SSH vs SSL
Key Differences Between SSH and SSL
Both SSH and SSL are public-key cryptography protocols that create a secure, confidential exchange of data and connection across the Internet. Let’s discuss some of the major key differences:
- Usually, SSH uses Port 22, whereas SSL uses Port 443.
- SSH uses a username/password authentication process to establish a secure connection, whereas SSL does not consider it.
- SSH is based on network tunnelling, whereas SSL is based on certificates.
- SSL is used for securely transmitting critical information like credit cards and banking. Whereas SSH is used for securely executing commands across the Internet.
- SSL is used for encrypting communication between browser and server. On the other hand, SSH is used for encrypting communication between two computers over the Internet.
- In SSL, the communication is authenticated via the private-key/public-key pair. Whereas in SSH, the communication is authenticated via private-key/public-key pair or username/password pair.
- Technically, SSH is for securing computer networks, whereas SSL is for securing online data transfers.
- SSL generally (except exceptions) uses X.509 digital certificates for server and client authentication processes, whereas SSH does not.
- Another major difference is that SSH has more built-in functionality than SSL. It helps in enabling users to log in to a server and execute commands remotely, whereas SSL does not have this functionality. To achieve this functionality, you need to pair it with another protocol like HTTP, FTP.
Comparison Table of SSH vs SSL
Let’s discuss the top 8 difference between SSH vs SSL.
| Key factor | SSH | SSL |
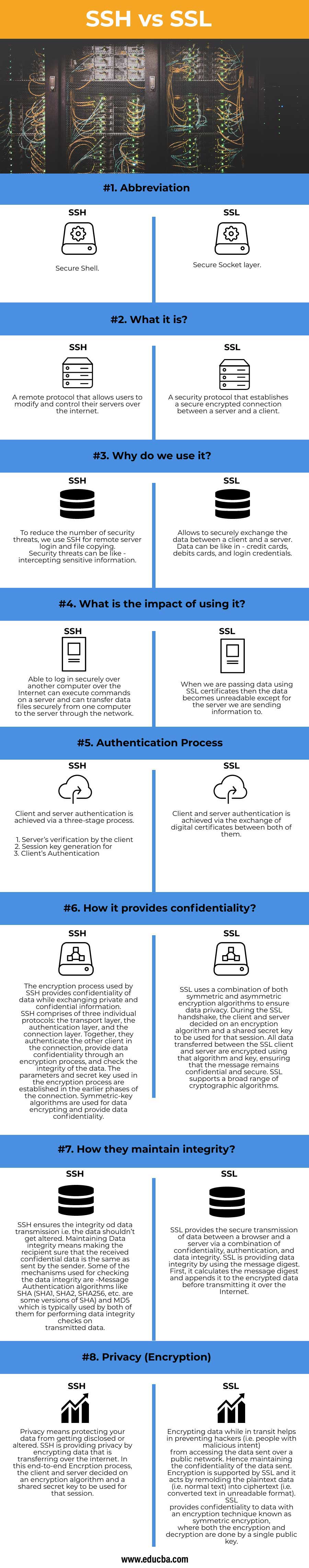
| Abbreviation | Secure Shell | Secure Socket layer |
| What is it? | A remote protocol that allows users to modify and control their servers over the internet. | A security protocol that establishes a secure encrypted connection between a server and a client. |
| Why do we use it? |
|
|
| What is the impact of using it? | Able to log in securely over another computer over the Internet, can execute commands on a server and can transfer data files securely from one computer to the server through the network. | When we are passing data using SSL certificates, then the data becomes unreadable except for the server we are sending information to. |
| Authentication process |
Client and server authentication is achieved via a three-stage process.
|
Client and server authentication is achieved via the exchange of digital certificates between both of them. |
| How it provides confidentiality? | The encryption process used by SSH provides confidentiality of data while exchanging private and confidential information. SSH comprises of three individual protocols: the transport layer, the authentication layer, and the connection layer. Together, they authenticate the other client in the connection, provide data confidentiality through an encryption process, and check the integrity of the data. The parameters and secret keys used in the encryption process are established in the earlier phases of the connection. Symmetric-key algorithms are used for data encrypting and provide data confidentiality. |
SSL uses a combination of both symmetric and asymmetric encryption algorithms to ensure data privacy. During the SSL handshake, the client and server decided on an encryption algorithm and a shared secret key to be used for that session. All data transferred between the SSL client and server are encrypted using that algorithm and key, ensuring that the message remains confidential and secure. SSL supports a broad range of cryptographic algorithms. |
| How they maintain integrity? | SSH ensures the integrity od data transmission, i.e. the data shouldn’t get altered. Maintaining Data integrity means making the recipient sure that the received confidential data is the same as sent by the sender. Some of the mechanisms used for checking the data integrity are -Message Authentication algorithms like SHA (SHA1, SHA2, SHA256, etc. are some versions of SHA) and MD5, which is typically used by both of them for performing data integrity checks on transmitted data. | SSL provides the secure transmission of data between a browser and a server via a combination of confidentiality, authentication, and data integrity. SSL is providing data integrity by using the message digest. First, it calculates the message digest and appends it to the encrypted data before transmitting it over the Internet. |
| Privacy (Encryption) | Privacy means protecting your data from getting disclosed or altered. SSH is providing privacy by encrypting data that is transferring over the internet. In this end-to-end Encrption process, the client and server decided on an encryption algorithm and a shared secret key to be used for that session. | Encrypting data while in transit helps in preventing hackers (i.e. people with malicious intent) from accessing the data sent over a public network. Hence maintaining the confidentiality of the data sent. Encryption is supported by SSL, and it acts by remoulding the plaintext data (i.e. normal text) into ciphertext (i.e. converted text in unreadable format). SSL provides confidentiality to data with an encryption technique known as symmetric encryption, where both the encryption and decryption are done by a single public key. |
Conclusion
Both the SSL and SSH (Secure Sockets Layer & Secure Shell) are Asymmetric key cryptography security protocols, and they aim to provide a confidential and secure exchange of data & connection across a public network or internet.
Recommended Articles
This is a guide to SSH vs SSL. Here we discuss the SSH vs SSL key differences with infographics and comparison table. You may also have a look at the following articles to learn more –