Updated November 2, 2023
Introduction to Reverse Engineering
Reverse engineering is the process of analyzing a product, system, or software to understand its design, function, and components. Often, it involves dismantling an object to expose its underlying architecture, source code, or specifications, which can provide important insights for reproducing similar products or identifying vulnerabilities. Many industries, such as technology, software development, and manufacturing, commonly use reverse engineering to learn from existing systems or to create compatible or interoperable solutions. The goals are:
- Complexity Co-Operation.
- Recovering the Lost Information.
- Determining the Side Effects.
- Higher Abstraction Synthesis.
- Providing the Facility for Reuse.
Table of Contents
- Introduction
- Why We Use?
- Process
- Methods
- Examples
- What are Some Legal Cases or Ethical Issues?
- What is Legal Implementation?
- Is it Unethical to Reverse Engineer?
Why Do We Use Reverse Engineering?
People primarily engage in reverse engineering for the following reasons:
- Interoperation of the System Requires Developing Interfaces: Use this when no documentation is available or when legacy systems are involved.
- Corporate or Military Spying: You can use it to copy your competitors’ product design and attempt to understand how to develop the market for that product.
- Documentation of the Product Improvements: If the documents provided for the products do not meet the standards, we can use reverse engineering to update the product’s documents to higher standards.
- Obsolescence Factoring Out: The lifespan of many components of products is short. It can be used to construct the components of the products with the materials currently available if the component of the product is not available for purchase. If there is no maintenance or support of a product from the original manufacturer, then also reverse engineering is required.
- Modernization of the Software Products: If the business encounters a specific challenge it cannot solve, it can employ reverse engineering to understand the legacy system and address the problem. Migrating the legacy systems to new platforms can be done with the help of reverse engineering.
- Adaptions of Security: You can manage and remove copyrights to facilitate piracy with the help of this. If you clearly understand the operation of the product, you can use reverse engineering to implement strict protocols.
- Fixing the Flaws in the Product: Reverse engineering the products that the original manufacturers do not support can help fix the existing problems.
- Making Copies of the Original Product: The process of making copies of the original product is also known as cloning.
- Reverse Engineering Serves as an Educational Tool: Reverse engineering can help us understand both successful and unsuccessful designs, and we can use the knowledge gained through this understanding to build upon it in the future.
- Reduction of Cost: Reverse engineering helps you understand a product’s structure and components, enabling you to replace expensive original components with more affordable alternatives.
- Waste Products Can Be Reverse-Engineered and Redesigned: You can reverse-engineer useless products and put them into use by restructuring them again.
- Competitor’s intelligence: It can be used to understand what the competitors are doing rather than what they are stating they are doing.
Process of Reverse Engineering
Reverse engineering involves multiple processes, with distinct steps for reverse engineering a software product as opposed to a pharmaceutical product. However, both processes share a common goal: uncovering the production process of the finished product and comprehending the requirements for its creation.
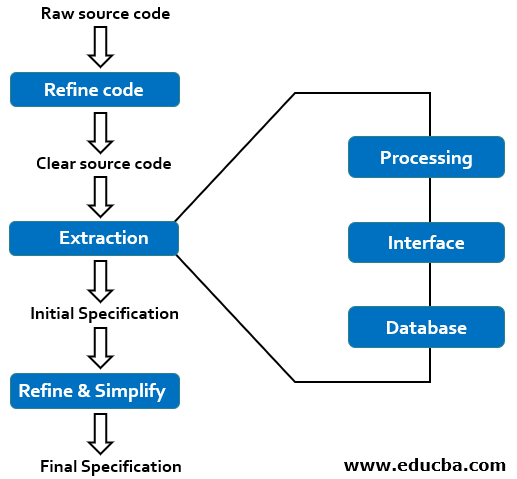
The steps involved in software reverse engineering can be described using the below diagram:
Here’s an overview of the steps you’ve listed, with some explanations and additional details:
- Collect Information: Gather all available information about the system or object you want to reverse engineer. This may include documentation, software, hardware, or other relevant resources.
- Record Functionality: Document the system or object’s high-level functionality and purpose. Understand how it works.
- Examine the Information: Analyze the collected data and information to gain a deep understanding of the system’s components, behavior, and underlying technologies.
- Record Control Flow: Map out the control flow of the system. This involves identifying the sequence of operations, functions, and components the system uses to achieve its functionality.
- Extract the Structure: Identify the structural elements of the system, such as classes, modules, components, and their relationships. This helps us understand how the system is organized.
- Record Data Flow: Trace how data moves through the system. To understand how information goes through input, processing, and output, we need to consider data structures and manipulation.
- Review Extracted Design: Review and refine your understanding of the system’s design. Ensure that your understanding is accurate and comprehensive. This step often involves iterations as you gain more insights.
- Generate Documentation: Create comprehensive documentation that describes the system’s architecture, components, functionalities, data flow, and other relevant details. This documentation should be detailed enough for others to understand and recreate the system.
Reverse engineering can be an intricate and time-intensive procedure, which might demand technical expertise, tools, and resources. The specific steps and level of examination can change based on the complexity of the system or object being reverse-engineered. Additionally, the legality of reverse engineering can be a concern in some cases, so it’s essential to ensure that you have the legal rights to reverse engineer the target and adhere to relevant laws and regulations.
Reverse Engineering Methods
Here are the explanations for these reverse engineering methods:
- Disassembly and Decompilation: Disassembly involves converting machine code (binary) back into assembly language, a more human-readable program representation. Decompilation goes further by attempting to recreate high-level source code from the disassembled assembly code. Both methods help analysts understand and modify software without access to the source code.
- Static and Dynamic Analysis: Examining a program’s code without executing it is known as static analysis. This process involves inspecting the source code, binaries, or intermediate representations to identify vulnerabilities or detect behavior. In contrast, the dynamic analysis consists of running a program and monitoring its behavior, memory usage, and interactions with the system in real-time to identify issues that occur during runtime, security flaws, or malware behavior.
- Binary Reverse Engineering: Binary reverse engineering analyzes compiled executables or firmware directly without access to the source code. This method involves disassembly, debugging, and analysis of binary files to understand how software or firmware works, identify vulnerabilities, or create patches and modifications.
- Reverse Engineering Software and Hardware: This method analyzes software and hardware components. When applied to software, it involves dissecting and understanding software applications or firmware. When applied to hardware, it consists of deconstructing and studying the physical components of devices or systems, such as circuit boards or integrated circuits, to understand their design, functionality, and potential modifications or improvements. This statement implies that it has applications in cybersecurity, product development, and system maintenance.
Examples of Reverse Engineering
Here are some examples:
- Software Reverse Engineering: Analyzes compiled code to comprehend its functionality, source code, and vulnerabilities. Developers often use it to create patches or modifications or to identify security flaws.
- Hardware Reverse Engineering: Involves dissecting and analyzing physical devices, such as electronic components, to understand their design functionality and potentially replicate or modify them.
- Cybersecurity: In this context, experts use it to analyze malware, identify its behavior, vulnerabilities, and attack vectors, and develop defenses and security solutions against it.
- Protocols: Analyzing communication protocols used in networking, IoT, or industrial control systems helps in interoperability, security assessment, and creating compatible implementations.
- Product Compatibility: Companies use it to understand competitors’ products and design compatible or similar features.
- Legacy System: Maintenance uses documentation when critical systems or databases lack it.
- Video Games: Gamers or modders reverse engineer video games to create mods, uncover hidden features, or even develop emulators for playing old games on new platforms.
- Aerospace: Aerospace engineers use reverse engineering to analyze and replicate components or systems for maintenance or replacement.
- Medical Device: Research, improvement, and development of compatible accessories for medical devices ensure patient safety and healthcare advancements.
- Consumer Electronics Reverse Engineering: Reverse engineering consumer electronics like smartphones or tablets can help third-party manufacturers create compatible accessories or understand proprietary technologies.
What are Some Legal Cases or Ethical Issues?
New court decisions show that reverse engineering techniques’ legal and ethical existence is used to get interoperability for an independently developed computer program. Lexmark filed a lawsuit against SCC in Dec 2002, accusing it of violating copyright law and the DMCA. SCC reverse-engineered the code used in the Lexmark printer cartridge to create compatible cartridges. According to the world of computers, Lexmark claims that SCC’s Smartek chips contain copyright-protected Lexmark technology. The program manages the interaction between Lexmark printers and toner cartridges; without it, rehabilitated toner cartridges will not operate with Lexmark’s printers. “The court ruled that ‘copyright law should not be used to prevent interoperability between the goods of one company and those of their competitors, in a U.S. decision. “The DMCA does not prohibit code developers from using reverse engineering to access electronic protected copyright material if they do so to achieve interoperability with an independently developed computer program,” the Copyright Office said in October 2003.
What is Legal Implementation?
- Patent protection protects the concept behind a new product’s operation.
- Copyright Protection only covers a product’s form and design.
According to NPD Solutions, a patent is a warning sign to a rival to discourage competition. Only NPD-solutions says a rival can do one of the following if interest is in an idea: RE is usually performed using the Chinese or clean-room wall. Clean-room, It is done sequentially.
Is it Unethical to Reverse Engineer?
This problem is widely discussed, and apparently, there is no exact answer to the split. That of intellectual properties is the number one claim against reverse engineering. Because Lexmark and businesses like them spend time and money developing products, they find it unethical that others might reverse engineer their products. There are also items that these activities, such as Bit Keeper, have harmed. Why should businesses and individuals spend large amounts of resources on acquiring intellectual property that rivals could reverse at a fraction of the cost?
Conclusion
Reverse engineering is a highly versatile and essential practice that allows us to uncover the inner workings of software, hardware, and other systems. This practice is an integral part of industries ranging from cybersecurity to product development. It enables us to enhance, secure, or adapt technologies as per our requirements. As technology advances, the ability to reverse engineer is a critical skill that fosters innovation and ensures the integrity of complex systems.
Recommended Articles
We hope that this EDUCBA information on “Reverse Engineering” was beneficial to you. You can view EDUCBA’s recommended articles for more information.