Updated April 6, 2023
Introduction to Penetration testing phases
Penetration testing is a set of processes that investigates a system’s different problems and tests, analyses, and offers solutions. It is focused on a step-by-step approach for performing penetration testing. Here is the list of different steps or penetration testing phases.
A successful penetration testing method would provide both automatic and manual procedures for assessing a company’s security defenses. The following seven measures should be used in a thorough penetration test:
1. Define the purpose of a penetration test: Identifying which programs should be checked and how they should be tested
2. Reconnaissance of the systems that have been tested: Identifying known vulnerabilities and checking systems for exploits
3. vulnerability assessing and the threat modeling phase
Exploring data on vulnerabilities and developing a threat model
4. The exploitation phase
Performing the vulnerability in order to gain access to the target network or device.
5. Active Intrusion attempts phase: Installing a governance framework and obtaining access to further networks on the target network
6. Post-test exploitation and risk identification phase: Vulnerabilities and flaws in security mechanisms are listed.
7. Penetration testing report preparation: Creating a report that includes a management review as well as technical information.
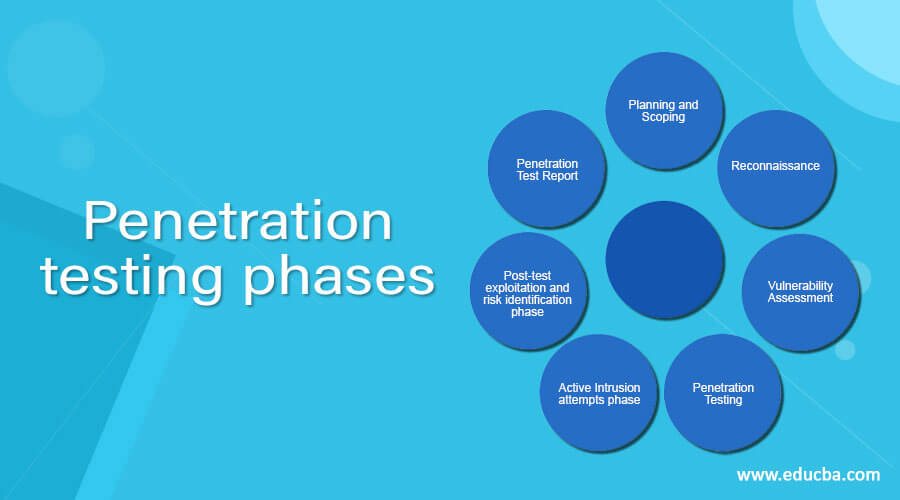
Phases of Penetration testing
We are going to see these penetration testing phases in detail.
1. Planning and Scoping
Defining testing scope is generally established with the penetration test provider. It should contain the test plan and the extent of intrusion that is permitted when vulnerabilities are found. Penetration testing is a white hat procedure in which the attacker is a tester who follows the scope definition’s rules of engagement. Before initiating the penetration test, the ethical hacker must sign a confidentiality document because he or she may have access to classified data and information.
2. Reconnaissance
In this phase, the tester tries to gather as much knowledge as practicable about the organization’s systems, future objectives, and weaknesses during the reconnaissance period. Penetration testers mostly focus on open source intelligence and independent IT device scans. Information about the organization’s internal processes may or may not be accessible to the penetration tester. In certain situations, a company will guide an attacker to particular vulnerabilities or targets that they are worried about.
The following are some examples of information gathering techniques:
- Search engine querying
- WHOIS or DNS lookups
- Social engineering techniques
- Tax records of the company and other public records
- user accounts, Email addresses, and social media profiles
- Port scans, ping probes, packet sniffing, reverse DNS, etc.
- Shoulder surfing
3. Vulnerability Assessment
In this phase, the penetration tester implements a probe on the target network, gathers preliminary data, and analyses the results to determine exploitation routes.
This phase could lead to insights such as:
- server’s directory.
- Open a secure connection to an FTP server.
- SMTP access points that send error messages with information about the network architecture.
- Probability to Remote code execution.
- Vulnerabilities in cross-site scripting
- An internal code-signing certificate can be used to sign and insert new scripts into the network.
4. Penetration Testing
A penetration tester uses automated tools to search target properties for vulnerabilities in this phase. These tools usually have their own files that provide information about the most common vulnerabilities. On the other hand, testers discover Network Exploration, which includes the discovery of new networks, routers, and other equipment. It also includes Host Discovery which defines available ports on these devices using.
5. Active Intrusion attempts phase
If a penetration tester has accomplished breaching the security perimeter or exploiting a target device, they can activate malware or some method to enable continued access, much like a real advanced persistent threat. And if the system is restarted or maintained, the control function should be persistent and stay on the network.
6. Post-test exploitation and risk identification phase
Recommendations for closing vulnerability loopholes discovered in the environment can be an integral aspect of a penetration tester’s evaluation. Every major error found during the penetration test should be fixed by the penetration testing provider.
7. Penetration Test Report
Finally, the penetration tester gives the company a report. The test report should be communicated to two audiences: administrators and technological or security personnel. An executive summary that describes the penetration test plan in market terms and categorizes analysis results according to risk level. It’s for the business team, and it’ll be used to figure out what needs to be fixed and which problems pose an appropriate degree of risk.
Conclusion
This is a guide to the Penetration testing phases. Here we discuss the list of different steps or phases of penetration testing. You may also have a look at the following articles to learn more –