Updated July 1, 2023
Introduction to Network Mapper
Network Mapper, also known as Nmap, is a tool for scanning and identifying at-risk ports and nodes in a network setup. It comes with Kali Linux and is used for validating network security. Nmap is an efficient tool with high performance for network examination. It is easy to access and allows for multiple types of scanning, such as TCP, UDP, and stealth.
What is Network Mapper?
Nmap is a network vulnerability scanner that identifies all the services running on various ports. It determines whether the ports are open, closed, or filtered based on the responses it receives from different types of scans, such as TCP scan, UDP scan, and Stealth scan. It first estimates the network speed and then performs the scan based on the speed. Applications like Nexpose run Nmap in the background.
Nmap is also an inbuilt tool in Kali Linux that offers an edge for conducting security checks. It utilizes the ICMP scan to identify the network speed and then processes the scan request submitted by the user. While Nmap can scan all available ports, it usually scans only the default ports. Nmap analyzes the server’s response to identify open ports and services and presents the scan results to the security analyst for verification.
Working with Network Mapper
In this section, we will consider an example of performing an actual scan on an active IP to understand all the active services on that system. The IP belongs to a live server running various services to help users leverage the server’s advantages. Some services run on particular ports. When Nmap scans for the default ports, it checks the common services that could be more useful than others.
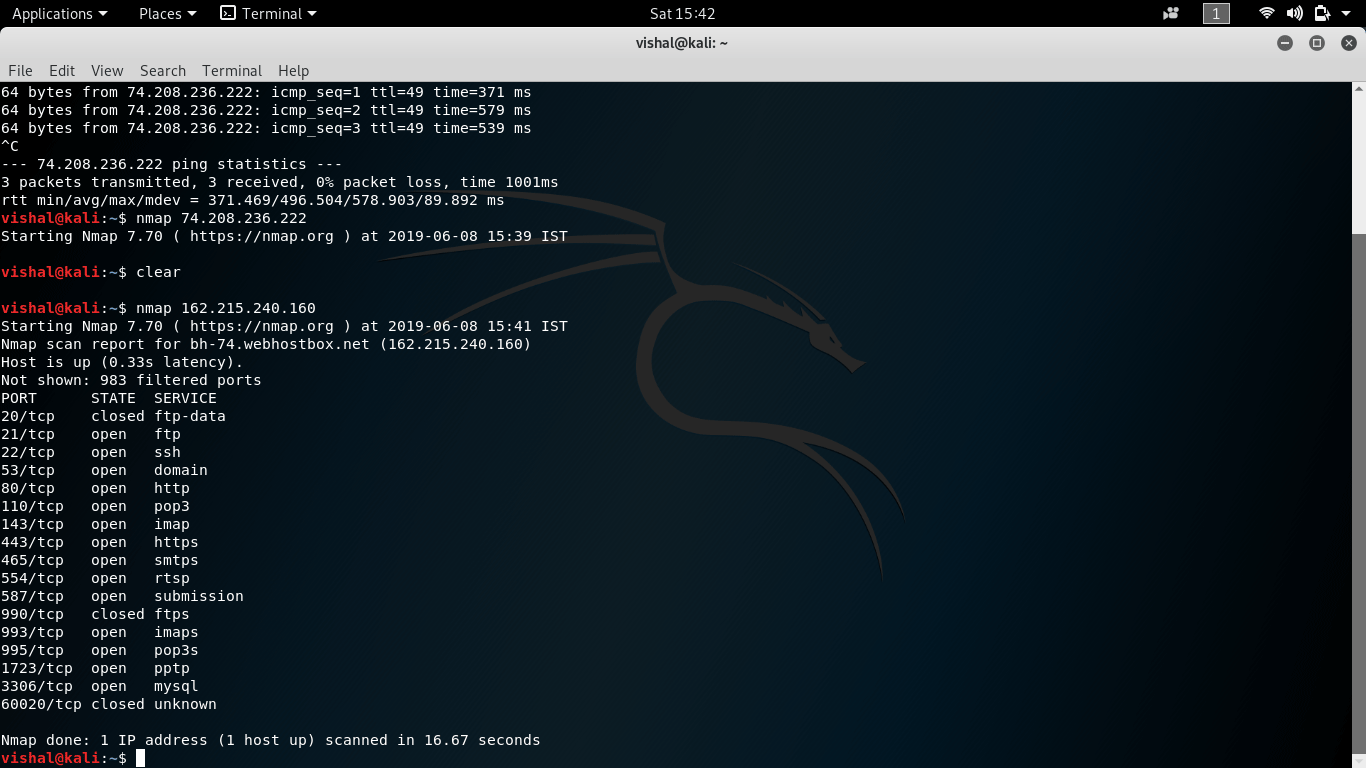
In the above picture, we can see that several services are up on the server. Some ports are open, while others are closed, but no filtered ports are detected based on the normal scan. It shows that ports such as 21, 22, 53, 118, etc., are open, running FTP, SSH, Domain, and POP3, respectively. The scan performed above is the default scan since we did not select any specific type of scan such as TCP, UDP, Stealth, or others.
The command executed in the terminal of Kali Linux has the Nmap keyword, which initiates the Nmap scanning. There are additional attributes like -sS, -sT, -sU that can be used with the Nmap keyword to scan the target system in the desired way. Here, we used the command Nmap 162.215.248.160, and as a result, Nmap presented all the port information, which shows how easy it is to work with Nmap. At the end of the scan, it also shows the total time required to complete the scan. Based on the outcome, the system analyst can determine if the system has any vulnerabilities.
Advantages of Network Mapper
The following are the advantages of Network Mapper:
1. Easy to use
Nmap is an inbuilt tool in Kali Linux that is very easy to use. One only needs to enter the IP address of the target that needs to be scanned, and all the services will be scanned.
2. Base for several applications
Several other applications use Nmap in the background to determine all the services. For instance, Nexpose is an application that uses Nmap internally to find vulnerabilities in any network.
3. Various scan types
Based on the requirements of a system administrator or any user, Nmap can perform different types of scans to achieve the desired results. For example, one can perform a stealth scan, which ensures that the scan on the target does not generate much noise in the network and thereby avoids log generation.
4. Network vulnerability scanning
Using Nmap involves finding the services running in the ports and their status, but the information produced as the outcome of the scan can be used to determine vulnerabilities in the system.
Career Growth
Anyone who wants to pursue a career in the security domain should have a working understanding of all the inbuilt tools available in Kali Linux, which are specifically designed for security testing. When it comes to having a working understanding of these tools, Nmap is the first tool that comes to mind. It is very useful for gathering details about the target. Based on that, one can determine what kind of attack will be suitable for the target.
Conclusion
Nmap is an inbuilt network scanning tool available in Kali Linux that security professionals use to safeguard their networks. It is very easy to use, and anyone concerned with network vulnerability assessment can learn it to gain a competitive edge in their career. There are other applications that also use Nmap to perform network scanning. Nmap has varying usage levels. A new user can use it as they explore the tool, while professionals can use it at an advanced level based on their expertise.
Recommended Articles
Here are some further related articles:


