Updated February 21, 2023
Introduction to Multiple Access Protocol
The multiple access protocol is essential to limit collision and avoid crosstalk between the channels if there is no dedicated link between the sender and receiver to communicate or transfer data between two devices.
What is a Multiple Access Protocol?
The data link control is sufficient to handle the channel when a sender and receiver have a dedicated link to transmit data packets. Assume there is no reliable communication or data transfer path between two devices. In this instance, numerous stations simultaneously access the channel and broadcast data across it. It could result in collisions and crosstalk.
For example, in a press conference, reporters ask questions to the organizer at the end of his talk, and then numerous reporters ask doubts and questions simultaneously. Therefore, to avoid confusion, the organizer should regulate the audience at that time.
Multiple Access Controlled
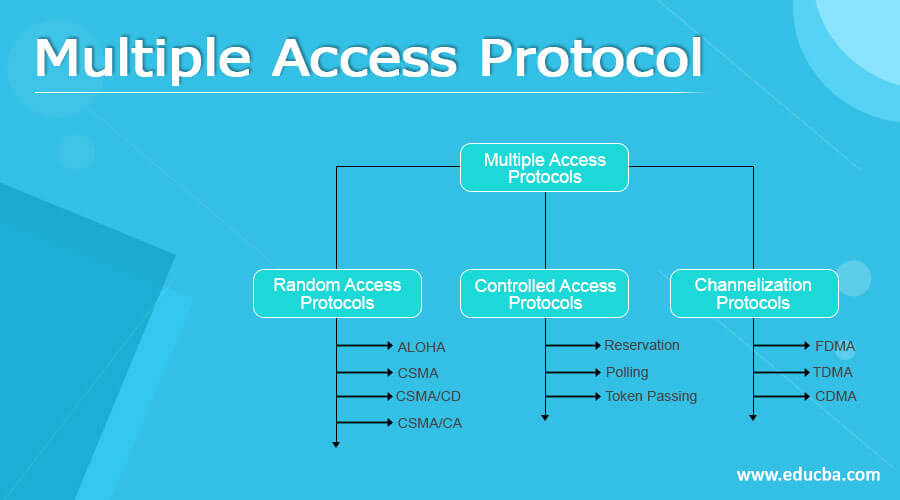
- FDMA (Frequency Division Multiple Access) — The bandwidth is divided into equal bands, allowing each station to have its bar. The eliminate crosstalk and noise, guard bands have been introduced to ensure no two bands overlap.
- The bandwidth is shared between stations in Time Division Multiple Access (TDMA). Time is separated into slots, and stations are assigned to transmit data during these slots.
- However, there is a synchronization overhead because each station must know its time slot. Adding synchronization bits to each space solves this problem. Another problem with TDMA is propagation latency, which can be overcome using guard bands.
- Code Division Multiple Access (CDMA) – All transmissions are simultaneously carried on a single channel. There is no such thing as bandwidth or temporal division.
- If several people in a room speak simultaneously, flawless data reception is also conceivable if just two people say the same language. Similarly, data from many stations can simultaneously be delivered in different coding languages.
Multiple Access Protocol Categories
Below are the different categories of Multiple Access Protocols:
1. Random Access Protocol
This protocol ensures that all stations have equal superiority, meaning no station has a higher priority than another. Depending on the status of the medium, any station can transfer data (idle or busy). It has two characteristics:
- There is no set timing for data transmission.
- There is no set order in which stations deliver data.
Random access protocols are further classified into the following categories:
a. ALOHA: This protocol was created for wireless LANs, but it can also be used for shared media. Multiple stations might broadcast data simultaneously, resulting in collisions and jumbled data.
- Pure Aloha: When a station transmits data, it waits for a response. If the acknowledgment does not reach within the given time, the station waits a random time (Tb) before re-sending the data. Because different stations take varying amounts of time to remain, the chances of another accident are reduced.
- Slotted Aloha: It’s identical to pure aloha, except that we divide time into slots, and data can only be sent at the start of each place. If a station runs out of time, it must wait for the next available slot. It lowers the chances of a collision.
b. CSMA: Carrier Sense Multiple Access – reduces collisions by requiring the station to sense the medium (idle or busy) before transmitting data. It transfers data if the channel is idle; it waits for the track to become inactive. However, there is still a probability of a collision in CSMA because of the propagation delay. Station A, for example, will first sense the medium before sending data. Then, it will begin transferring data if the channel is found to be idle. However, suppose station B wishes to send data and senses the medium. In that case, it will also find it idle and send data by the time the first bit of data is transmitted (delayed due to propagation delay) from station A. As a result, data from stations A and B will collide.
c. CSMA/CD: Carrier sense multiple access with collision detection. If a collision is detected, stations can stop data transmission. For further information, see CSMA/CD Efficiency.
d. CSMA/CA: The sender receives acknowledgment signals as part of the collision detection procedure. The data is successfully delivered if there is just one signal (its own), but if there are two signals (it is own and the one with which it collided), a collision has occurred. A crash must significantly influence the received signal to discriminate between these two instances. In wired networks, however, this is not the case. Hence CSMA/CA is employed.
The CSMA/CA protocol avoids collisions by:
- Interframe space: The station waits for the medium to become idle before sending data (to minimize collision due to propagation delay) but remains for a long time, known as Interframe space or IFS. After that, it checks if the medium is still idle. The station’s priority determines the size of the IFS.
- Contention Window: The time divided into slots is known as the Contention Window. When the transmitter is ready to transfer data, it selects a random number of slots as the wait time, which doubles each time the medium is not found idle. If the medium becomes busy, the procedure is not restarted entirely; instead, the timer is restarted when the channel becomes idle again.
- Acknowledgment: The sender retransmits the data if the feedback is not received before the time-out.
2. Access Control
That station sends the data, and all other stations have approved it. For more information, see Controlled Access Protocols.
3. Channelization
The existing bandwidth of the link is shared in frequency, time, and coding among numerous stations to allow them to access the channel simultaneously.
Multiple Access Protocols CSMA Access
- 1-persistent: The node detects the channel and sends the data if idle; it constantly checks the medium for idleness and transmits unconditionally (with one probability) as soon as the track becomes idle.
- Non-persistent: The node detects the channel and sends the data if idle; otherwise, it examines the medium after a random time (not continuously) and transmits if it is discovered idle.
- P-persistent: The node detects the media and delivers data with a p probability if idle. If the information isn’t sent ((1-p) probability), it waits a while and then rechecks the medium; if it’s still idle, it sends with p probability. This process is repeated until the frame is sent. Wifi and packet radio technologies both use it.
- O-persistent: Node superiority is determined in advance, and transmission occurs in that order. Node waits for its turn to send data if the channel is idle.
Conclusion
- The multiple access protocol handles multiple channels between sender and receivers.
- This protocol operates multiple channels between two devices and handles networks for communication.
Recommended Articles
This has been a guide to Multiple Access Protocol. Here we discussed Multiple Access Protocol with its categories, CSMA access, and a detailed explanation. You can also go through our other suggested articles to learn more –