Updated March 23, 2023
Introduction to IDS Tools
IDS Stands for the Intrusion detection system. It is a device or software application used to detect intruder activity, i.e. the malicious activities if performed by an attacker. So, the Intrusion detection system can be software or hardware or a combination of both, which can be used for detecting malicious activities. As our world is growing day by day from the data perspective, we need a more secure and reliable network so that we can keep the data route safe and secure. Here, we need IDS to make the data route more secure by providing high security as it stops all the malicious activities from entering in your network. In this topic, we are going to learn about IDS Tools.
Explanation of the IDS Tools
The IDS can be differentiated from firewalls in the term of a packet, i.e., a packet decoder. To do the rules analysis for IDS, there is a preprocessor in the snort engine that performs this action. The detection engine detects the intrusion by checking the packet and rules together.
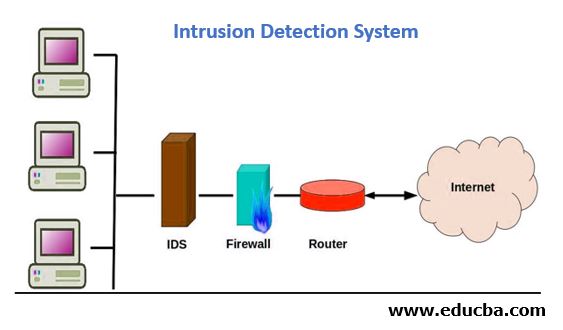
In the above figure, IDS plays a crucial role in protecting the network from malicious activities. All the inbound and outbound traffic passes from IDS, which makes the entire network more safe and secure. Here all the internet is added to the route table, i.e. we have configured the IP 0.0.0.0/0 in the route table in order to allow all the incoming requests from the router, i.e. the router will allow all the incoming traffic from anywhere. After that, the firewall is also configured in the route table where we can allow the request of different ports like HTTP requests can pass from port 80 and HTTPS can pass from port 443. HTTPS is more secure than HTTP requests as it is encrypted and uses SSL certification.
Here IDS will be integrated with both the client and firewall as such that all the requests will pass from the IDS tool. So, if all the traffic passes from the IDS, it makes the network more secure and safe by stopping malicious activities from passing through it. Sometimes it also protects the network by blocking the IP address from where the malicious activities are trying to access the network. Hence, IDS acts as a protection layer for the underlying infrastructure, which maintains the server to maintain the tasks.
Depending on their capabilities and complexities – they are divided into different groups. They use different signature and techniques in order to trace the malicious activities, i.e. they match the signature of the incoming traffic with the original signature; if it matches it will allow
- Network intrusion detection system(NIDS): In NIDS, the IDS are deployed on the network in order to deny the malicious activity from accessing the network.
- A host-based intrusion detection system(HIDS): In HIDS, the IDS are deployed on the host in order to deny the malicious activity from accessing the host.
- Perimeter Intrusion Detection System(PIDS): In PIDS, IDS is used in an external environment to detect the presence of an intruder attempting to access a perimeter.
- VM based Intrusion Detection System(VMIDS): In HIDS, the IDS are deployed on the VM (Virtual machine) in order to deny the malicious activity from accessing the host.
So, the IDS, whether it is placed internally, i.e. inside the firewall or outside of the firewall. It is used to detect malicious activities and stopping them from accessing the network by matching their signature with the original one. If the signature of the incoming traffic matches with the original one, then it will allow them to access the network; otherwise, it will deny them. There are different types of IDS tools based on where they are deployed, complexity and techniques which they use in order to detect malicious activities. All the inbound and outbound traffic passes from them.
Choosing an IDS
Steps for choosing the IDS:
- Identify your security needs.
- Determine the purpose of IDS.
- Network-based or host-based.
- Consider Application-based (Higher in cost).
- Research features – As all IDS doesn’t have the same feature.
- Determine what support is available as there are some open-source IDS tools that are feasible in every condition.
- Consider deploying more than one IDS – In order to attain more security, if the attacker is trying to disable one IDS, 2nd one will be functioning and will protect the environment.
Below is some highly rated IDS software:
- Cisco Secure IDS: Network-based, Scans and terminates connections.
- Snort: Host-based network intrusion; very flexible.
- AIDE: Host-based file and directory integrity checker.
- OSSEC: Host-based (Unix) System Checker.
- CheckPoint: Provide several IDS tools.
Conclusion
As our world is growing day by day, the amount of data traffic is also increasing. So, we need a more secure and safe network for the data transfer as we are moving forward. Also, from the organization’s perspective, to maintain business continuity or gain customer trust, the security of the network for any data is an important aspect. So here, IDS plays an important role from which all the inbound the outbound traffic passes from them, which stops all the malicious activities from accessing the network.
Recommended Articles
This is a guide to IDS Tools. Here we discuss the basic concept and steps for choosing some of the highly-rated IDS Tools. You can also go through our other suggested articles to learn more –