Updated June 16, 2023
What is the Full Form of OTP?
In this article, we will learn about the Full Form of OTP: OTP stands for ‘One-Time Password,’ a numeric password generated specific to the transaction and valid for a limited time.
How Does an OTP Work?
A traditional static password system requires the user to set a password to login into an account or to authenticate a transaction. The user must input the same password each time they run the process.
The system generates dynamic one-time passwords (OTPs) valid only for a specific transaction or a limited time period. Once expired, the same OTP cannot be reused to complete the transaction or any other session. The randomly generated OTP is unique to the transaction and session and will not resemble OTPs generated in subsequent sessions.
How to Get an OTP?
In the article Full Form of OTP. The two most common ways an OTP is generated are explained in brief below.
1. Time-Based One-Time Password (TOTP)
- This system uses an algorithm that considers the current date and time as a basis of authentication for its input.
- The OTP generated is valid for a limited duration from the time of its generation. Once the time limit expires, the OTP becomes invalid for authenticating the transaction and needs to be regenerated.
- The freshly generated OTP is unique and unrelated to the previous OTP, also valid for a specified period from the time of its generation.
- The time period for which a TOTP is valid is usually in increments of 30 seconds, that is, 30 seconds, 60 seconds, 90 seconds, and so on.
2. Based on Mathematical Algorithms
- The system selects a starting value called the ‘seed’ and applies a mathematical algorithm to create a password series. The system then saves the resulting passwords.
- The values are then dispensed in reverse order as OTPs in different login sessions.
- Deciphering the algorithm or function from the end value, i.e., the received OTP, is nearly impracticable.
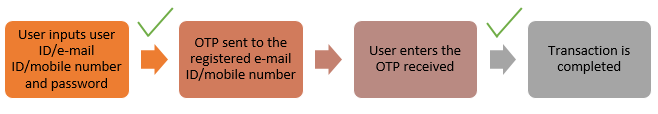
OTPs, particularly TOTPs, are increasingly used as part of a two-factor authentication system, which works as follows:
- The user must first enter his user ID/e-mail ID/mobile number and password.
- The system first approves the entered credentials and sends an OTP to the registered e-mail ID or mobile number.
- The user then inputs the OTP received in the system.
- Upon verification of the OTP entered, the system approves and completes the transaction.
Thus, the static password set by the user authenticates the transaction initially, and the system-generated OTP serves as an additional layer of security for further authentication.
Methods of Delivering OTP
OTP can be delivered in multiple ways, some of the common ones being:
- Shown on mobile apps processing the transaction.
- Sent as a text message to the registered mobile number.
- Mailed to the registered e-mail ID.
- Automated voice calls from a centralized server conveying the OTP.
Examples of OTP
In the article, Full Form of OTP. OTPs are generally 6-digit numeric codes unique to a user session and transaction. Following are some examples of how an OTP might look like:
- 568479
- 983013
- 631178
OTP vs Static Password
In the article Full Form of OTP. Below we explain the difference between OTP vs Static Password:
| Static Password | OTP |
| Static passwords are set by the user in line with the requirements specified by the system. For instance, the system may require a password containing at least one numeric character and symbol. | The system generates numeric codes for OTPs. |
| A static password, once set, is used by the user to authenticate at the time of every login or transaction, i.e., the same password is used for authentication for every user session or transaction. | Once generated, an OTP is valid for a specific period, user session, or transaction. A fresh OTP generates during every new login or transaction execution. |
| Static passwords provide a lower level of security than OTPs since they are more susceptible to theft of passwords and hacks. | OTPs are a more secure form of authentication since a unique password is generated for every user session or transaction, and the algorithm is hard to decipher or hack. |
Benefits of OTP
A more secure form of authentication:
- Replay attacks can exploit your vulnerability to static passwords by intercepting data transmissions, such as passwords, to carry out fraudulent transactions without your knowledge.
- Users should only use one-time passwords (OTPs) once, and they are specific to a particular user session and transaction. Even if someone intercepts the OTP, it cannot validate any future transactions, as a new OTP would need to generate.
- Every subsequent OTP bears no visible resemblance to the previous one and, therefore, cannot be easily guessed.
- Complex algorithms generate OTPs, making it difficult to derive the original OTP from the generated code.
- When used in a two-factor authentication system, OTPs provide an additional layer of security in combination with static passwords.
Conclusion
OTPs, when used in a two-factor authentication system, provide additional security instead of static passwords. Although more secure than a static password, OTPs can also be susceptible to cyber-attacks. To protect user interests, it is advisable not to disclose OTPs and static passwords to any third parties.
Recommended Articles
This is a guide to the Full Form of OTP. Here we discuss how OPT works? 2 ways to get OPT with examples, along with the benefits of it. Also, know the difference between. You can also go through our other related articles to learn more –