Difference Between CEH vs CPT
Certified Ethical Hacker – It is not uncommon for people to talk about a website being ‘ hacked’, and you might have seen news reports about popular websites being hacked by a group of people or by an individual. In the cyberworld, the people who perform such ‘criminal’ acts are called hackers. They may be intelligent programmers or network administrators who may be doing it for the thrill of it or to steal information or take control of a website or portal.
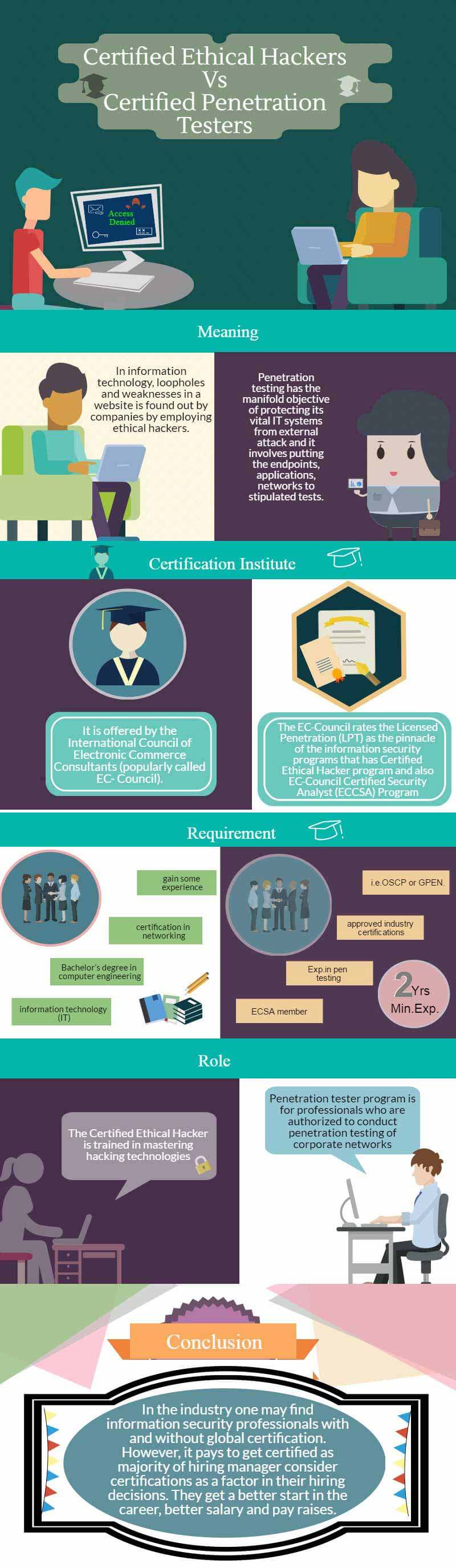
In order to find loopholes in a system or a property, the best method is to employ a thief and find it out. In information technology, companies’ loopholes and weaknesses are found out by companies by employing ethical hackers. They are trained certified people with years of experience to detect loopholes so that companies can plug it soon and prevent huge loss in case of an unsuspected hacking or virus attack on a site.
The severity of the cyber attacks can be gauged from the US White House action plan to spend $19 bn on cybersecurity initiatives, including educating consumers to use two-factor authentication. This follows recent hacking that compromised US citizens’ personal data- in November; Federal authorities charged three men for intruding into systems of nine financial institutions, including JP Morgan, Dow Jones, Scottrade and eTrade, putting the data of 100 mn customers under risk.
A study by the Ponemon Institute in 2014 showed that the average cost of a data breach for the affected company is $3.5 mn.
Many industry research and survey reports have indicated rising security breaches in websites and computer networks, thereby increasing trained or licensed ethical hackers’ opportunities.
Head to Head Comparison Between CEH vs CPT (Infographics)
Following are the top difference between CEH and CPT:
How to become a Certified Ethical Hacker?
There are many institutions offering hacker training courses, but ultimately it should lead you to get the Certified Ethical Hacker (CEH) certification offered by the International Council of Electronic Commerce Consultants (popularly called EC- Council).
It is not easy for just anyone to become an ethical hacker or a certified ethical hacker as previous experience in the IT industry is a requirement for any formal education in this domain. Ideally, an ethical hacker should have a programming background with a bachelor’s degree in computer engineering or information technology (IT). The first step is to get a certification in networking, gain some experience in the area before going for the Cisco CCNA certification (Cisco Certified Network Associate). It is a certificate that validates a professional’s ability to understand, configure, operate, configure and troubleshoot medium-level switched and routed networks and also includes the verification and implementation of connections via remote sites using WAN.
Thereafter, it is better to go for earning additional certifications in Security, CISSP or TICSA. This will enable the person to get a position in information security. At this stage, it will be better to gain experience in penetration testing. A penetration test involves the assessment of the security of IT implementation is done in an organization. It is done with the objective of identifying the vulnerabilities present in the network. The areas that are vulnerable include servers, operating systems, wireless networks, mobile devices, service, configurations and applications. These tests can be done manually or by running automated programs.
Thereafter, after gaining more exposure in the industry, one can try for the international Certified Ethical Hacker (CEH) certification provided by the International Council of Electronic Commerce Consultants (EC –Council). According to EC, the Certified Ethical Hacker program is the pinnacle of the most desired information security training programs for professionals.
Apart from networking lessons, an ethical hacker should have knowledge of Unix/Linux commands and distributions, programming in C, LISP, Perl or Java. Knowledge of databases such as MySQL will also come in handy for ethical hackers.
Apart from technical knowledge, they also need to have problem-solving and people skills or social engineering. They should get people to disclose their credentials, restart or shut down systems or execute files.
There are five phases in ethical hacking- 1) Reconnaissance, 2) Gaining Access, 3)Enumeration, 4) Maintaining Access and 5) lastly covering your tracks. Reconnaissance involves gathering information about an intended target of a malicious hack by probing the target system. The ports scan to find weaknesses in the system and find vulnerabilities around the firewall and routers. Once it is detected, the means to access the system can be worked out by the hacker. There are two types of reconnaissance- active and passive.
Passive reconnaissance may have nothing to do with information security or IT systems, but it could be knowledge about company routines- the times when employees arrive and leave. Or it could be internet protocol (IP) changes, naming conventions, hidden servers, or networks. The hacker monitors the flow of data to see at what times transactions are taking place and the traffic routes.
Gaining access to the system is the most important phase of the hacker attack. It can happen over local area network (LAN) or internet, local access to a PC, or even offline access. It includes stack-based buffering overflows, denial of service (DoS), and session hijacking.
The enumeration or scanning phase involves examining the network based on information gathered during reconnaissance. The tools used are dialers, port scanners, network mappers, sweepers and vulnerability scanners.
Maintaining access is vital to keep it for future use. Sometimes they maintain exclusive access through backdoors, Trojans, and rootkits. The final stage is covering tracks to avoid detection by security personnel. The certified Ethical Hacking (CEH) program covers these topics in detail and is tested by EC-Council before awarding certification, which qualifies the candidate to take up challenging assignments in the industry.
The exam tests the knowledge and skills of candidates in the following areas-
-
- Telecom, networks, cyber media, and IT systems
- Have a broad understanding of security protocols associated with the operating systems-MAC Linux and Windows,
- Should be able to hack hack into a computer system of an organization to assess its vulnerabilities and weaknesses with due permission-
- Undertake preventive and corrective measures against malicious attack
- They should be adept at identifying and cracking different types of passwords and thwart password attacks.
- Understand cryptography and encryption techniques with private/public key infrastructure.
- They should have knowledge of cyber-attacks, including Trojan, URL, obfuscation, identity theft and social engineering.
Penetration Testing
Penetration testing has the manifold objective of protecting its vital IT systems from external attack, and it involves putting the endpoints, applications, and networks to stipulated tests. It enables security professionals to ward off any possible threat well in advance by initiating remedial action where vulnerabilities are found.
Regular pen testing helps companies know beforehand what all security risks the IT system is exposed to. Timely remedial measures prevent hackers from intruding into the network, compromising valuable data. It avoids the cost involved in a security breach that could run into millions of dollars and loss of image regarding customer protection of data and business-to-business information involving third-party data. Penetration testing helps an organization to meet compliance/auditing regulations such as GLBa, HIPAA, and Sarbanes-Oxley. Companies can save significant money by way of fines related to security non-compliance with penetration testing. They will be able to comply with testing as mandated by federal FISMA, PCI-DSS, or NIST.
Licensed Penetration Testing by EC-Council
The EC-Council rates the Licensed Penetration (LPT) as the information security programs’ pinnacle with the Certified Ethical Hacker program and the EC-Council Certified Security Analyst (ECCSA) Program.
The EC-Council LPT exam is the most challenging practical exam prior to awarding of certification. The course’s online version has over 39 intense modules and over 2300 slides that foray into complex aspects of penetration testing. The course provides 1100 tools to help them dive deep into the science of penetration testing.
The EC-Council says that the LPT exam was developed in collaboration with small and medium enterprises and practitioners worldwide after a thorough job, role, job task, and skills gap analysis. It simulates a complex network of a multi-national organization in real-time.
The online version of the course enables information security personnel to learn penetration testing from anywhere in the world and apply for an LPT license. The license is an assurance to your stakeholders that you possess the ‘hands-on skills-based competency to perform a thorough security assessment.
Eligibility criteria
Not all IT professionals are eligible to apply for EC-Council licensing, especially for Pen testing. The candidate has to be an ECSA member in good standing, have a minimum of two years of experience in pentesting, and have approved industry certifications such as OSCP or GPEN. Applicants can directly apply to EC-Council via an online web form.
The advantages of certification
- The certification allows candidates to practice penetration testing and consulting on a global basis.
- Industry acceptance as a legal and ethical security professional.
- Access to software, templates, and testing methodologies of EC-Council.
Although different agencies provide certification, EC-Council certification enables them to practice their skills so that they can function as a licensed penetration testers.
Although Ethical Hacking and Penetration fall in the realm of information security, their roles and functions are subtly different. The Certified Ethical Hacker is trained in mastering hacking technologies, while a licensed penetration tester program is for professionals who are authorized to conduct penetration testing of corporate networks.
The EC Council certification exam applications are accepted online from https://cert.eccouncil.org/lpt-application-form.html.
Ankit Fadia’s Certified Ethical Hacker is also a program that is recognized the world over. It was devised by a globally famous authority on computer security. It provides the latest tools, techniques, and methods used by cybercriminals and terrorists. It also shows how to fight them. Ankit Fadia also shows how he hacks into websites, accounts, mobile phones, and passwords right in front of your eyes.
The potential of penetration testing and ethical marketing is huge, with India’s leading service sector portal Naukri.com displaying 115 vacant positions in this area.
The roles of Certified Ethical Hackers (CEH) and Penetration testers differ, although they fall in the realm of information security. The CEH is responsible for protecting the IT systems by performing certain routines that protect the system from external threats. In this domain, experts are employed as security auditors, network security specialists, penetration testers, site administrators, and security consultants, depending on knowledge, ability, and experience. Experts in these areas with certification from EC-Council are in great demand in the government sector, military, and defense. Ethical hacking courses that align with EC Council’s syllabi prepare information security personnel to get EC-Council certification. They are offered by schools in the private sector, universities in several countries.
Conclusion
In this industry, one may find information security professionals with and without global certification. However, it pays to get certified, as most hiring managers consider certifications as a factor in their hiring decisions. They get a better start in their career, better salaries, and pay raises.
According to the US Bureau of Labor Statistics, demand for information security analysts is expected to grow 18% from 2014 to 2024, which is faster than most other occupations. In India, there are only 50,000 cybersecurity professionals, but the nation needs five million professionals by 2020, according to the National Association of Software and Service Companies (NASSCOM).
The country requires 77000 new ethical hackers every year, but at present, only 15,000 are trained in this area. Even the best hackers need to study more and get global certification to gain credibility. In tune with the rising demand for ethical hackers and penetration testers, several institutes have sprung up in the private sector, offering various courses.
According to McKinsey, about 70% of Indian companies are susceptible to cyber-attacks. In one recent incident, a company had to pay huge amounts of money to regain control of its stolen data.
In the USA, regulations are strict with respect to compliance. India doesn’t have the Health Insurance Portability and Accountability Act equivalent that the US Congress passed in 1996. The Act is meant to protect and handle confidential health information of America. It is difficult for companies that are non-compliant with HIPAA to do business in the USA.
Experts said, along with ethical hacking and penetration testing, Vulnerability Assessments are also gaining popularity but often gets confused with penetration tests.
Recommended Article
This has been a guide to the top differences between CEH vs CPT. Here we have discussed CEH vs CPT head to head comparison, key differences, along with infographics and a comparison table. You may also have a look at the following articles to learn more –

