Updated July 5, 2023

Definition of Digital Forensics
Digital forensics is also known as computer forensics, an application to determine a scientific examiner method for digital attacks and crimes. It is an essential condition of both laws and business in the modern era of technology and might also be advantageous and growth in its career.
It is also defined as “the way of identifying, preserving, examining, and analyzing the digital evidence, by validating the procedures, and its final representation of that digital evidence in the court to evident few legal questions regarding the crime and attacks.”
What is Digital Forensics?
Digital Forensics is identifying, preserving, examining, and analyzing digital evidence by validating the procedures and final representation of that digital evidence in the court to identify a few legal questions regarding the crime and attacks. It is a method of discovering proofs from digital media like a PC, mobile or cellular devices, servers, or networks. It gives the forensic department group the elite procedures and equipment to resolve difficult digital cases of crimes.
Digital Forensics Team will help the forensic team analyze, inspect, identify, and preserve the digital evidence populating digital devices.
Objectives of Digital Forensics
Below are a few objectives of using digital forensics:
- Evidence to Court: It recovers, analyzes, and preserves digital and forensic evidence to help the department’s investigation to present the evidence in court.
- Identifying the Culprit: It aims to cause the attacks and identify the main culprit behind the crimes.
- Legal Procedures: To ensure the evidence found at a suspicious crime scene is uncorrupted, we design the methods for collecting and preserving the evidence.
- Data Redundancy: Recover the deleted files and subdivide them from digital media to validate them.
- It also encourages you to find the evidence instantly and makes you identify the impact of the culprit on the crime or the attacks.
- Storing the evidence or the proofs by the procedures in the way of legal custody in the court of law.
Process of Digital Forensics
In the field of Digital Forensics, we follow a pattern where we first identify each case, then preserve and analyze the evidence. We document the findings in a manner that enables us to present the evidence in the court of law, ultimately helping to identify the culprit in the crime.
Digital forensics involves the following steps:
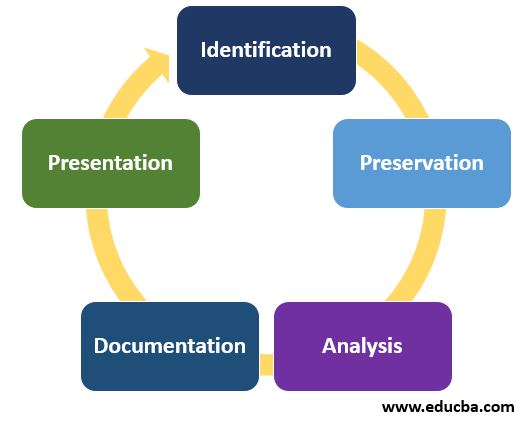
1. Identification
It is the first and fore more step in the process, including the forensic process, like where the evidence is found, where it is preserved, and how it is stored.
Electronic Device media includes PC, digital phones, IPads, etc.
2. Preservation
An isolating place stores the evidence to secure and preserve it from theft. People are prevented from buying digital devices to ensure no proof is meddled with.
3. Analysis
In this phase, the inspection group will reform the chunks of evidence and determine the outcome based on the resulting proofs or evidence. But it may sometimes take several iterations to discover the support on a criminal case.
4. Documentation
In this stage, all possible evidence of data is drawn from the given inputs. It will help in rebuilding the crime scene and analyzing it. The investigators document the correct documentation of the crime scenes by mapping the crime scene, sketching it, and then relating its photographs with the documents.
5. Presentation
To conclude, we summarize and explain the documents.
Types of Digital Forensics
There are a few types of digital forensics that include below:
- Disk Forensics: It will deal with deriving the evidence from digital storage media like USB Devices, DVDs, CDs, etc., by gathering the active files or modifying or deleting them.
- Network Forensics: It is generally a sub-part of digital forensics relating to the monitoring and detecting system network traffic to extract crucial data for all legal evidence to present at the court.
- Wireless Forensics: It is a part of the networking forensics type that aims for wireless forensics to allow the tools needed to gather and extract evidence from networking wireless traffic.
- Database Forensics: This type of digital forensics relates to the forensic study and collection of databases and their relevant metadata. It follows investigating techniques to query the database to collect the evidence.
- Malware Forensics: This branch of forensics handles identifying malicious code and studying malware issues related to their workload, trojans, viruses, etc.
- Email Forensics: This forensic branch handles the recovery of the trashed data and analyses the contents of the emails, including the emails that are deleted or the calendar or the contacts in the email.
- Memory Forensics: A forensic analysis collects the data from the computer’s cache memory or RAM dump and then gathers the evidence.
Advantages of Digital Forensics
Below are a few advantages of Digital Forensic:
- To assure the security of the digital forensic system.
- To gather the proof in the law of court, which may point to action on the culprit in the crime scene?
- It assures the forensic team to capture relevant information if their digital systems or traffic are not working as expected.
- Accurately track the series of cybercriminals’ crimes anywhere throughout the world.
- Gathers extracted, processed, and interpreted the forensic evidence to prove the cybercriminal’s action in the law.
Disadvantages of Digital Forensics
Below are a few disadvantages of Digital Forensic:
- There should not be tampering with the digital evidence presented in the court. We need to demonstrate that the data is free from corruption.
- Storing electronic records is very costly.
- Legal advisors should have more knowledge of digital devices.
- It should give the court more secure and easily understandable evidence.
- The Court of Law accepts the evidence only if the tools follow specific standards.
- If the investigating officers are not knowledgeable, the evidence they provide to the court is useless. The judge may discard them.
Conclusion
Digital forensic Tools are much more accurate and helpful to investigating officers who try to find the culprits performing digital crimes or attacks. Digital Forensics is also utilized in digital criminal cases, including theft of intellectual property, industrial damage, employment issues related to job security, and investigations of fraud cases.
Recommended Articles
We hope that this EDUCBA information on “What is Digital Forensics?” was beneficial to you. You can view EDUCBA’s recommended articles for more information.

