Updated March 23, 2023
Introduction to Threat Hunting Tools
The process of abnormal activity on the server may be the indications of compromise, intrusion, or exfiltration of data, which is called threat hunting. The simple fact that no system is a hundred percent protected is the central pillar of threat hunting. An organization may employ several security layers for protecting itself from threats with the best and the most current technology, but there is always a chance of advanced threats. The approach most companies have adopted is that a security solution protects against most attacks after it is deployed, but if a new type of attack occurs, even the most efficient artificial intelligence-based security solutions will have a hard time analyzing the new threat.
The alternative approach to deal with cyber-attacks is threat hunting than the network security systems with appliances such as firewalls to monitor the traffic flowing into the system. Such methods of defense are used in the investigation of threats after they have occurred; the threat hunting strategy searches through the networks, detects and isolates the threats and disposes of them before the traditional network security system rings an alert alarm after the threat has occurred. The process of threat hunting has become automated, and it makes use of analytics to identify potential threats or risks.
Types of Threat Hunting Tools
The threat hunting tools are of three types which are explained below:
1. Analytics-Driven
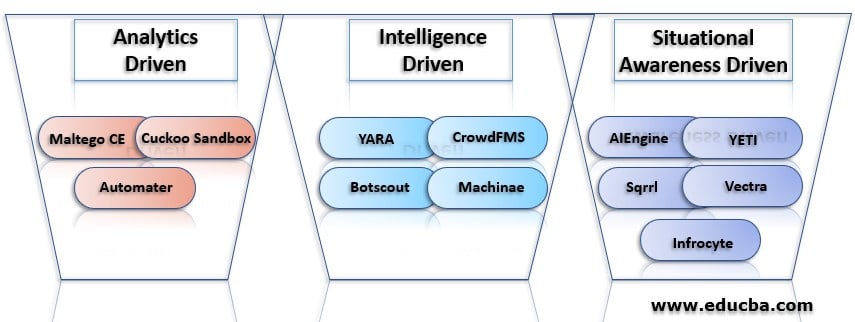
Analytics-driven threat hunting tools create risk scores and other hypotheses by using behavior analytics and machine learning. Maltego CE, Cuckoo Sandbox, automater are some of the examples of analytical tools.
- Maltego CE: Link analysis is created by using interactive graphs rendered using Maltego CE, a data mining tool. This tool is used for investigations online. The relationships between data portions from various sources on the internet are found, and if it is found to be a threat, an alert is alarmed.
- Cuckoo Sandbox: Disposal of suspicious files and up-to-date results can be done using a cuckoo sandbox tool, an open-source malware analysis tool. The information on the operation of malicious files to understand them better and to stop them is provided by the cuckoo sandbox tool.
- Automater: The data on an intrusion is provided by automated. We can choose the target, and results are reviewed by the automated from sources that are popular.
2. Intelligence Driven
All the data and reporting are pulled together and applied to threat hunting by using intelligence-driven threat hunting tools. YARA, CrowdFMS, Botscout, and Machinae are some of the examples of intelligence-driven threat hunting tools.
- YARA: Malware can be classified using a multi-platform tool called YARA. The descriptions of malware belonging to the same category based on patterns of text or binary are created by YARA. The boolean expression makes the description, and a set of strings and expressions determines the identity.
- CrowdFMS: Collection and processing of samples from a website that publishes the phishing emails details are done by an automated application called crowdFMS. An alert will be alarmed if a match to a phishing mail crosses the network.
- Botscout: Spams, server abuse, database pollution caused by bots can be prevented by not allowing the bots to register on forums using botscout. Internet providers, names, email addresses can be tracked, and elimination of bots can be done by identifying the source.
- Machinae: The intelligence is compiled from public websites and feeds on data related to security like domain names, URLs, email and internet providers addresses, etc. Machinae is free software and has good compatibility when compared to other security intelligence software in the market. It has a well-optimized configuration, and many inputs and outputs are supported.
3. Situational Awareness Driven
The trends of a company or an individual can be evaluated using assessments of risk or crown jewel analysis, which indicates how much risk they are running. Artificial Intelligence Engine, YETI are some of the examples of situational awareness that has driven threat hunting tools.
- Artificial Intelligence Engine or AIEngine: The network’s intrusion detection system can be modernized using an interactive tool called Artificial Intelligence Engine or AIEngine. Human interaction is not necessary for its learning and forensics of the network; detecting spams and collecting networks can be done using Artificial Intelligence Engine or ALEngine.
- YETI: To share the details all over the organization, we use the tool YETI. Companies acquire the data from partners whom they trust and share the data to inform everyone on the latest threats. There are threat hunting tools that are not available for free and must be paid to acquire them.
Some of the paid threat hunting tools are Sqrrl, Vectra, Infrocyte.
- Sqrrl: A threat hunting company is called Sqrrl. Advanced cyber tools are used to make their tools available to companies to track and hunt down threats. The platform provided by Sqrrl brings together link analysis, user and entity behavior analytics, multi-petabyte scalable capabilities. The attacker’s dwell time can be reduced dramatically by using Sqrrl, which is an incident response tool.
- Vectra: To stop the attackers in the network, we use a Vectra tool, which is fast and efficient. To find out the details of the attacker, artificial intelligence provides real-time attack visibility.
- Infrocyte: To identify threats and unauthorized activity on a network, we use a tool called infrocyte, which provides several solutions. Assessments of breach discovery making them fast and affordable to small businesses are being done by the tool infrocyte.
Conclusion
There are many applications of the tools mentioned above, and when they are used in combination, great defense can be established against cyber-attacks. Threat hunting adds significant value to the strategy of cybersecurity. The simple fact that no system is a hundred percent protected is the central pillar of threat hunting, and the threat hunter can identify and prevent the attacks proactively.
Recommended Articles
This is a guide to Threat Hunting Tools. Here we discuss the introduction and top 3 Threat Hunting tools with examples in detail. You can also go through our other related articles to learn more –