Introduction to Computer Networks
A computer network is a digital telecommunications network that uses popular telecommunications technology to share resources between nodes, which are computer devices. It is the interconnection of multiple devices, commonly known as Connected Hosts, using multiple paths for sending/receiving data or media.
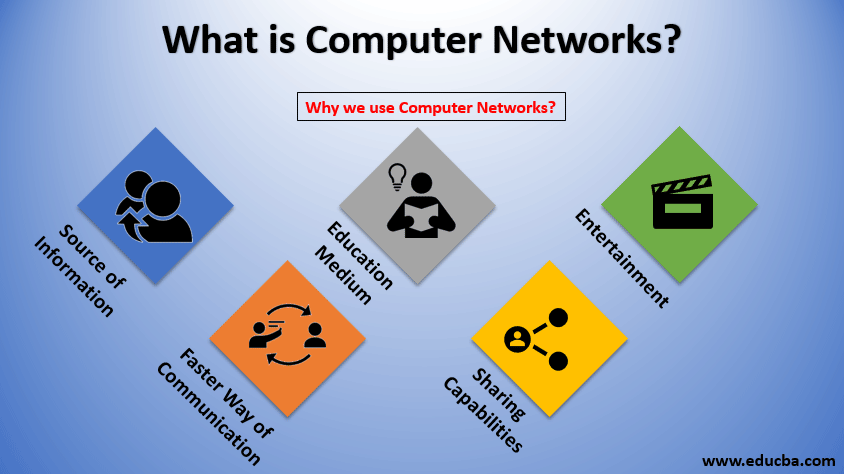
Why We Use Computer Networks?
The need for a present-day computer network can be well understood if we consider the following scenario: imagine a world with no e-mails, online news, blogs, and communication channels. Will, it is not unfair to human society as we need to connect among ourselves for better intellect on the global platform. There can be n number of cases that favor the importance of computer networks.
The below points are worth noticing.
1. Source of Information: The computer network was created with a vision to be a medium of information. Talking of the information can be anything forms as small as an inquiry about ticket reservations to weather forecast information and social media to watching movies online. Anything and everything under this sun under the spectrum of information exchange come under the concept of computer networks.
2. Faster Way of Communication: Definitely a faster and more accurate medium for procuring information. What we need in terms of the information we get on a click.
3. Education Medium: It is a trusted medium one can rely upon during the learning phase. Either it is students or professionals who look after the computer network as a medium of gaining information.
4. Sharing Capabilities: A user can share any kind of files locally or globally based on his needs by leveraging the benefits of computer networks; apart from this, the computer networks also make the user share their hardware like printers, scanners, and drives. In addition to this, it enables its users to share applications as well.
5. Entertainment: It was done to computer networks that we in our childhood days played internet games. It facilitates its users to play a single game with multi-users.
Importance of Computer Networks
There are multiple reasons why a computer network is essential for any kind of business, school, college (academics), and even individuals.
The below points are worth noticing –
- Cost Cutting: Every organization looks for a feasible way to reduce wastage. Computer networks do the same by managing resources efficiently. The hardware setup is a troublesome task for any business with a computer network; these hardware are interconnected and leads to resource pooling, avoiding unwanted software installation from time to time.
- Fix Your Storage-Related Problems: We know that a computer network puts its data to some central servers or repository which is accessible to employees or users as and when needed or as per authority, but under whatever reasons they need certain kinds of information, you are minimizing the storage consumption with increased efficiency.
- 24*7 Access on The Go: Isn’t it great if some information is accessible anytime, anyplace? Yes, because of that, we can get details whenever we need to.
- Data Security: a business can never think of being completely secured without protected access to network resources and files. You can grant access to a particular user community with a certain type of data utilizing computer network features.
As everything has some benefits associated with it, the same way there are some limitations as well which is even crucial for our readers to know.
Limitations
These limitations can have several reasons from a technology point of view, and at some time, the user’s community also contributes, let us see some of them –
- Security Threats: security breaches are possible to occur for any secured systems of technology. This is something we cannot ignore either we can be relaxed about it. There are threats all across the globe with evil minds trying to restrict their full potential. So we can say that these are under a constant threat of misuse.
- Need for Effective Handler: There are some responsible people behind any good thing. Some huge configurations and settings go behind the proper working of the computer networks. A full group of technicians is working behind it, which creates huge maintenance charges. If there is the slightest mistake, then the entire user community has to suffer the problems.
- Expensive Setup: setup is costly and also demands a constant check-up. Its initial setup is huge and depends upon the number of computers and other devices that needs to be connected. Devices like switches, hubs, and routers add a huge sum to the business.
Advantages
Some of the advantages are given below:
- A source that enhances communication and information
- A convenient way to share a resource
- Files sharing made easier.
- Highly flexible
- Cost-effective solution
- Boost storage capacity
- Creates more opportunities for IT
- It makes work collaboration easier.
- Quick file transfer
- Opportunity to learn and explore this technology
Conclusion
The quality of technical solutions serves as a success factor since humans have believed in information technology. We can consider computer networks an essential solution; it has a wide spectrum of potential suitable to an even a wide range of businesses in any format. In the above section, we tried to cover the possible pros of this technology, and at last, we are leaving our audiences with one concluding statement with the belief that our readers will emphasize on it.
“Until and unless you have full control over the workplace, you can never think of full control over the marketplace.”
Recommended Articles
This is a guide to What is Computer Networks? Here we discuss the introduction to Computer Networks and their importance, uses, and advantages. You can also go through our other suggested articles to learn more –


