Updated May 22, 2023
Introduction to Tor Browser, Anonymity, and Other Browsers
Most of you may have heard about the Google Chrome browser, Opera, Mozilla Firefox, and the like of it. But only some of you may have heard about the infamous and dark Tor Browser. So, what exactly is it? It’s not famous among people who are happy with their day-to-day chores.
But are a specific set of people, or as I would say, the better phrase would be A different world where people use Tor Browser as their day-to-day browser. What are its specifics? How does it differ from Chrome or Mozilla? Is it user-friendly?
Does it have loads of services inbuilt similar to that of Chrome? Does it come with a built-in Flash player, incognito tabs, or private browsers like Firefox or Opera? The answer is NO! It is nowhere near the term user-friendly.
It doesn’t have any features like Google Chrome. It’s not highly customizable like Mozilla Firefox. It’s prolonged when compared to Chrome or Firefox. Then what makes Tor Browser extremely famous among people with high curiosity? Let’s take a deeper look at that.
Tor Browser
First of all, the Tor browser is not user-friendly. If you think of using it as a daily-usage browser, you should stick to Mozilla Firefox(and NOT CHROME). The main reason for that is that Tor is slow. WAIT! That’s not the only reason. The main reason is that it’s highly volatile. Yes.
Tor Browser is an open-source browser built especially for anonymity. Anything you do use the Tor Browser stays anonymous. It bounces off your IP address through several servers worldwide before reaching the particular spot you searched for—a screenshot for the IP address of what my computer shows when using a Tor browser.
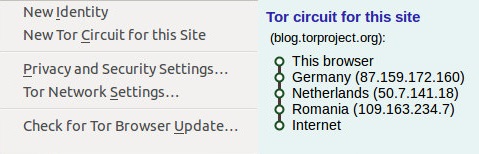
Image Source: torproject.org
Yes. It routed my IP address all across the globe before getting connected to the internet. Besides, if you want to change the IP address, you can straightaway click on the New Identity, and your last connection point will change, which will change your IP address. Else, if you want a new circuit, you can even do that, which will change all the countries’ routed IP addresses.
Tor Browser vs Google Chrome vs Mozilla Firefox vs Opera
Following are the comparisons:
1. Opera Mini
Firstly, Opera is almost similar to that Google Chrome. May it be looks or feature-wise. But I would discard Opera here, the main reason being it’s a closed-source browser. It means it’s secure. It is, but since it’s a closed-source browser, we need to know what’s happening behind the scenes. So, I will straight away discard it here.
2. Google and Privacy
The next one is Google Chrome. Everyone’s favorite browser of all time. The most secure browser. Is it? Is it true? No! I don’t think so. Let me give you an example in an old-fashioned way. Let’s say you are going out for dinner one evening. You have a massive house with built-in security features, like cameras, motion detectors, automated alarms, and reinforced security doors.
But you are still paranoid. So, would you give your keys to a renowned thief(just because he knows all the flaws), thinking he would keep it more secure? Not. But that’s what we do with Google Chrome and all its stuff. The first thing is anything once on the internet is always on the internet—the second thing.
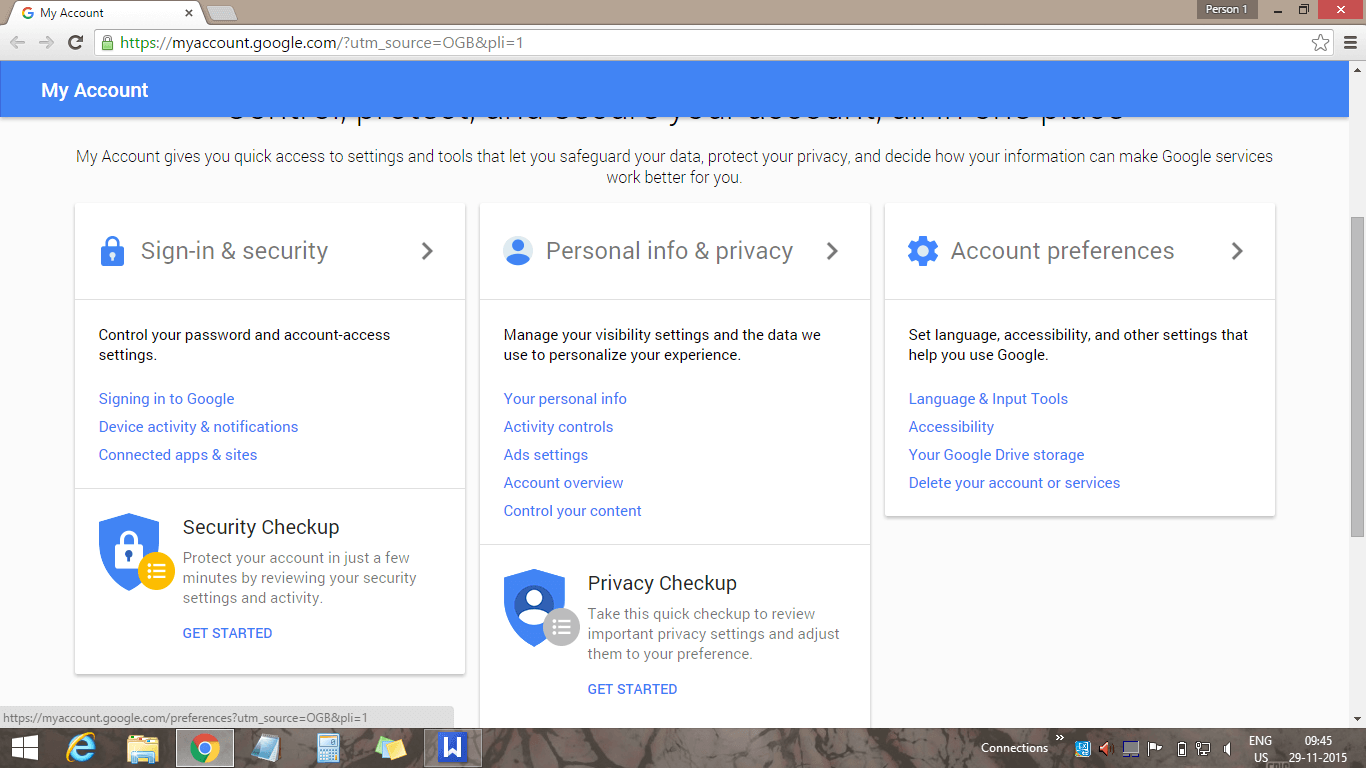
Google is the master in storing this stuff and that, even without you knowing that. Don’t believe me? Follow the below steps, and see what you get:
- Login to your Gmail id from Chrome.
- Click the profile picture or the extreme top-right and click on My Account. You will see a page similar to this:
Image Source: google.com
- Click on ‘Your info.’
- Now here, you may want to check the list of things, but to be specific, check the first tab: Your searches and browsing activity.
It enables by default. Once you open this, you will see all the stuff you browsed or searched for, including the passwords and everything from the day you created your account till today. Yes, it will keep all the records from the day you made your account, whether two years ago or a decade ago.
Even if you delete everything, the content stored on the Google server will still not get deleted. The question here is, why does Google need to keep all of this data? So much Data from every person on the web. Here is what my previous example suggested. It doesn’t matter how secure the Google Browser is if Google itself is the Keeper and the Robber.
People often won’t change the browser even after knowing this, stating: “It’s okay if Google knows everything; at least there should be someone keeping tabs on everyone.” Then here is my question about that. “So you know me. At least a little? Then why don’t you give ME your password? I will keep it secure, I promise.” The people fray away when I say this.
It means people are ready to give all their life details to some random person working at Google who has yet to be well-known. So much for absolute security here. Besides, people have so many things shared on google plus, drive, keeper notes, Gmail contacts, synchronized play store, etc.
The final impact of this becomes like a drug to an addict. You may wish to leave it but can’t despite knowing everything. Because socializing is more important to people than privacy, which is the ultimate reason for their accounts to get hacked, think, what would happen if some random person hacks into your account?
They (the hacker) would know everything about your life. It will ultimately lead to identity theft. Besides, if some person has physical access to your computer or even your browser, then there is a 99% possibility that he has access to everything. Try to do this:
- Open your Chrome browser.
- Click on the settings tab on the top-right side, a three-line button.
- Click on Settings, and search passwords in the search box.
- It will show you a manage passwords tab right below. Click on that, and lo and behold. Here are all the passwords you ever saved knowingly or unknowingly.
3. What about Mozilla? They say it’s Secure
Have you heard the quote, “Everything you hear is not true”? Nope. I am not cursing Mozilla here. Firefox is trying its best to keep up with the latest goofed-up security. It’s at least honest when it says it’s private browsing compared to Google Chrome.
If you want a decent day-to-day browser that doesn’t keep track of all your records, Mozilla is good. It has loads of customization. It is fast than Tor, if not Google.
The least possible configuration an inexperienced person can do is install Firefox and change the search engine to Startpage or Duckduckgo, which is anonymous and doesn’t keep track of search records. Keep a Master password to save all your passwords so that even if someone gets physical access to your browser, they won’t be able to capture it.
But the downside is that the government can still track you down since you use your own ip address here instead of Tor, where you bounce off multiple locations.
4. Tor Browser
Is Tor Browser really that secure? There is no specific answer to that. It depends on how you configure it. If you finish the Tor browser download, you can check the following.
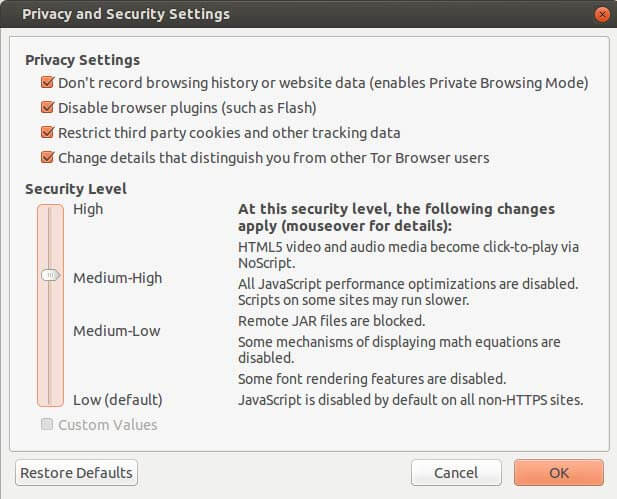
Click on the Onion logo on the Tor browser and then select Privacy and Security settings. Then you will have the below window:
Image Source: torproject.org
Here, you can set the level of security you want. Besides, there are other configurations you can do. There is also a tab for enabling https everywhere on the upper right-hand side of the browser. It’s an add-on from the HTTPS EVERYWHERE site, which is, by default, installed on Tor. Want the highest level of security, where no government and no MITM would suffice? Here is how you could do that:
- Set Security Settings on Privacy setting to High.
- Enable https Everywhere.
- Use DuckDuckGo as the search engine(it’s my personal choice, you can even use Startpage or ixquick, or Disconnect, which is Tor’s official)
- Usage of Proxy Address bonded with Tor.
- Use a VPN from other countries which do not have legal bindings with your country.
Yes. It is one of the best possible ways. On a lighter note, we don’t need this much. It is only for those Vigilant Hackers and Protesters who would use these techniques to keep themselves safe. Who knows? Paranoia is the key to the utmost security.
Conclusion
There is much more to Tor Browser than I have written in this blog. I have yet to comment about the deep web and the risks involved in the Tor web. But this would suffice to get you started or as advice to stay away from Google and all its products, which are not open-source.
One more browser is worth looking at, i.e., Iceweasal browser, which comes inbuilt with Kali Linux or the WHONIX Operating system, which relies solely on the Tor circuit for all its web-based activities from browsing to downloading stuff. Stay updated with my blogs for more on Privacy, Security, and Anonymity.
First Image Source: torproject.org
Recommended Articles
This has guided Tor Browser, Anonymity, and Other Browsers. We have discussed a brief overview comparing Tor Browser vs. Google Chrome vs. Mozilla Firefox vs. Opera. You may also have a look at the following articles to learn more –