Difference Between Symmetric Key vs Asymmetric Key
Data protection, in particular with modern communication networks, has become a monumental concern, leaving gaps that could be exploited for catastrophic consequences. This article addresses two common encryption methods used in Symmetric and asymmetric encryption to tighten communication security. The best way to continue this discussion is, in theory, to begin first with the basics. Therefore, we are going to look at the definitions of algorithms and the key concepts in cryptography and then dive into the key part of the discussion. In this topic, we are going to learn about Symmetric Key vs Asymmetric Key.
What is the Symmetric Key?
Symmetric encryption is a common Encryption form. It’s also the easiest of two methods. Symmetric encryption is carried out using a single hidden key known to all parties as to the ‘Symmetric Code.’ The key is used to encrypt information and decode it. The sender uses this key before the message is sent, and the receiver uses it to decode the encoded letter.
It’s a pretty straightforward procedure, and it doesn’t take much time as a result. Symmetric keys are preferred when transferring huge data. A good example of Symmetric encryption happens to be Caesar’s Cipher. AS, RC4, 3DES, DES, Blowfish, QUAD are used for modern approaches to symmetric encryption.
What is the Asymmetric Key?
Asymmetric Encryption is a modern and complex encryption style. Complex as it requires two encryption keys for data protection implementation. The keys are referred to as public keys. All who want to send a message can use the public key, as the name implies. On the other hand, the owner of the public key holds the private key safe.
The accessible key encrypts the information to be forwarded. It uses a particular algorithm. The secret key that the receiver has then decrypts it. Both processes are based on the same algorithm.
Head to Head Comparison Between Symmetric Key vs Asymmetric Key (Infographics)
Below are the top differences between Symmetric Key and Asymmetric Key
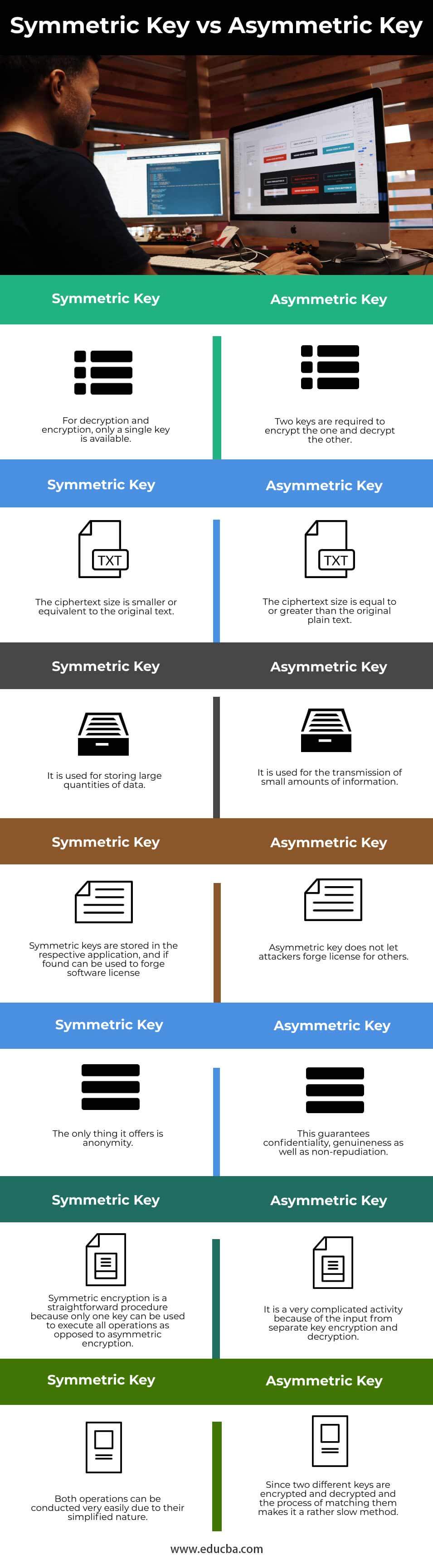
Key Differences in Symmetric Key vs Asymmetric Key
Below are some of the differences between Symmetric Key vs Asymmetric Key:
- Symmetric encryption uses a single key for message encryption and decryption. Nevertheless, the sender uses the public encryption key and the private decryption key in asymmetric encryption.
- In contrast to the symmetric coding algorithm, the execution of asymmetric algorithms is slower. That is due to the more complex and heavy calculation strain of the asymmetric encryption algae.
- The most widely used symmetric encoding algorithms are 3DES, DES, RC4, and AES. The most popular algorithm for asymmetric encryption, by comparison, are Diffie-Hellman and RSA.
- Asymmetric encryption is usually used to exchange secret key, but for transmitting a mass of data, Symmetric encryption can be used.
- Symmetric and asymmetric encryption is widely used in many applications. The Secure Sockets Layer (SSL) and the cryptographic Transport Layer Security (TLS) protocols that were built to ensure protected communication over the Internet are common examples of such hybrid systems. Unfortunately, the SSL protocols are now deemed dangerous, and their use will cease. In comparison, all major web browsers have found the TLS protocols secure and extensively used.
Comparison Table of Symmetric Key vs Asymmetric Key
Now let’s draft the comparison in the table below
| Symmetric key | Asymmetric key |
| For decryption and encryption, only a single key is available. | Two keys are required to encrypt one and decrypt the other. |
| The ciphertext size is smaller or equivalent to the original text. | The ciphertext size is equal to or greater than the original plain text. |
| It is used for storing large quantities of data. | It is used for the transmission of small amounts of information. |
| Symmetric keys are stored in the respective application, and if found, can be used to forge software license | asymmetric key does not let attackers forge license for others. |
| The only thing it offers is anonymity. | This guarantees confidentiality, genuineness as well as non-repudiation. |
| Symmetric encryption is a straightforward procedure because only one key can be used to execute all operations as opposed to asymmetric encryption. | It is a very complicated activity because of the input from separate key encryption and decryption. |
| Both operations can be conducted very easily due to their simplified nature. | Since two different keys are encrypted and decrypted, and the process of matching them makes it a rather slow method. |
Conclusion
Imagine a game in which two people (Asymmetric versus Symmetric) try to catch the other. Whenever the captured person encounters the runner, his / her pace increases so as not to get captured. This is exactly what currently takes place in the world of cybersecurity. The developer develops new algorithms in this case to keep the constantly improving cyber-criminal offender. It is also a must for consumers in the technology industry to embrace the latest developments. So in this article, we have seen what is Symmetric Key and Asymmetric Key along with key differences between them.
Recommended Articles
This is a guide to Symmetric Key vs Asymmetric Key. Here we discuss the Symmetric Key vs Asymmetric Key Key differences with infographics and comparison table. You may also have a look at the following articles to learn more –

