Updated February 18, 2023
Introduction to Redis EXPIRE
Redis expire one of the key sessions that can be used to determine whether a key will be available or not during a user session by allocating a certain amount of time for doing so. The persist command also enables the use of other related areas in the application timeout complexity for each key linked to timeout, regardless of whether it is volatile or non-volatile redis cache terminology.
To set a timeout that has passed with a key fully depleted, the contents must have expired along with the related timeout. We can use keywords like del, set, and getset commands for actions that conceptually store the default commands. This indicates that all actions are saved as key-value pairs with timeouts replaced. For instance, timeout operations increment the key values for methods like INCR, LPUSH, and HSET that push data. By setting the expiration time with the appropriate format, such as seconds, milliseconds, etc., using the SET and EX keywords.
Key Takeaways
- Set a timeout on each key; it will automatically set and expire the datas.
- By using Expire keyword, the timeout will be set.
- It has default types like NX, XX, GT, and LT each set have different timeout functionalities.
- 0 and 1 have the default timeout exception, whereas 1 denotes timeout was set, and 0 defined timeout was not set.
- Expire would return 0 as default and not alter the timeout.
How to Use Keys Expire Command?
The expire command is used to define a key timeout. The timeout is essential for performing redis key operations on users’ sessions. By using some controls connected to the SET and GETSET commands, these will be immediately cleared. Whether the key is volatile or non-volatile, the persistent key will operate using an expiration timeout. Keys already present in the Redis cache will be renamed using the rename function.
It throws the Invalid exception, which means that it is no longer valid for message encryption and decryption. Redis expire is mostly used to set keys with expiration dates that are not stored in the Redis cache. There are numerous ways to pass away the Redis keys that proactively and reactively elicit the time.
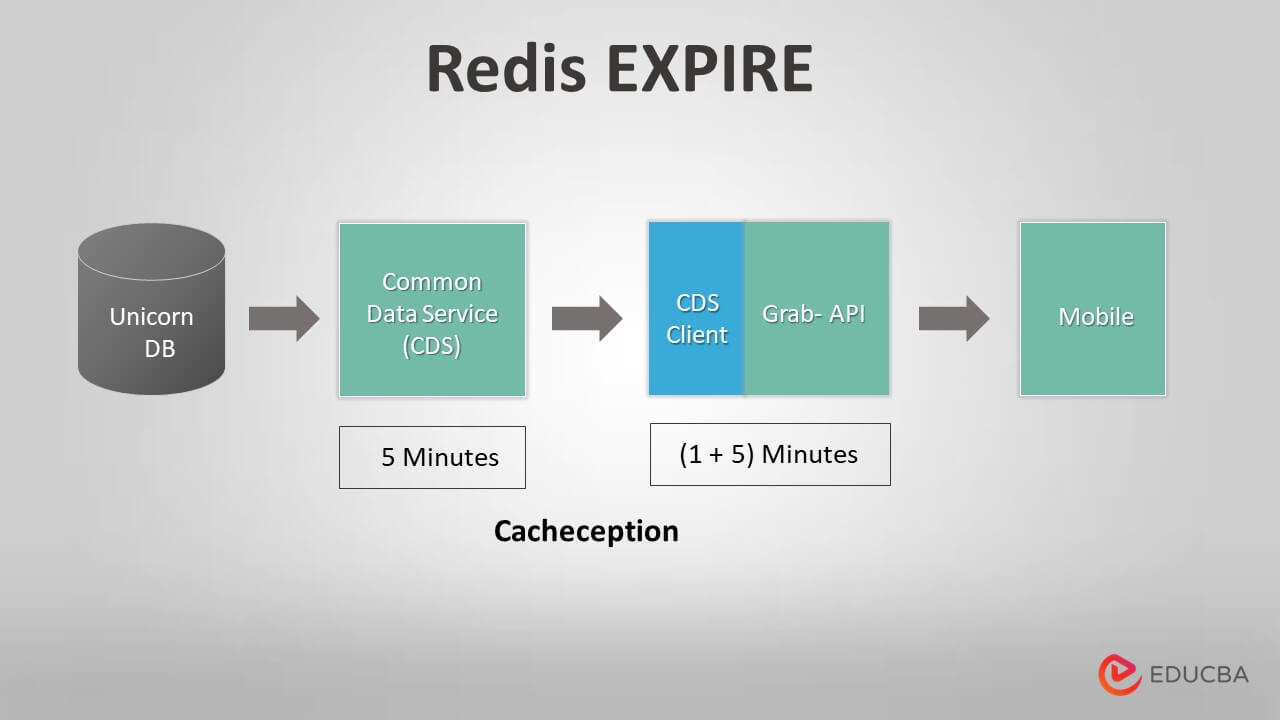
The cache exception regarding the key from the user session that is valid and invalid is shown in the above diagram. The Redis TTL command will assist in obtaining the amount of time still left in an existing key and its values because, in Redis language, a key’s value is frequently dynamic and is linked to timeout expiration. To run the TTL for key expiration and track the countdown, the timeout will overwrite the key contents that already existed in the Redis cache. Beginning with 300 seconds, the time is counted down to 0, at which point the key value, such as -1 or -2, is returned.
Validating keys by running them through Common Data Services, often known as CDS, takes a few minutes. Then, the cache system will obtain the values from the CDS client and Grab-API to complete the cache action. The propagation time from the database replication specific region in Unicorns is changed to 60 or 1 hour while using the mobile data cache, which differs from the inter-service data cache. The master cache allows the master node to read and write the TTL time for each and every key. Slave Read Only.
Setting Keys to Expire Redis
Redis keys are typically constructed with an associated timeout to correct key expirations and maintain consistency in data behavior. Del is a keyword used to synthesize the operation for replicated nodes with associated files and data. The primary centralized method for expiration has data consistency issues for replicating datasets to keys. EX keyword was mainly required for the expire action. To obtain a correct behavior, the datas are sacrificed with consistency for key expires the DEL operation between the file called AOF.
Redis can be used to display the cache contents for the database queries, and it is mainly supposed to be used for all types of users. It expires time for html static content, including languages like Html, JS, CSS, and Redis for storing the session. The unique store contents are mainly referred to in Redis databases that created the disk for reading and writing contents in each user session on the Redis cache.
Steps to Create and Setup the Keys and validate whether it is Expired or Not.
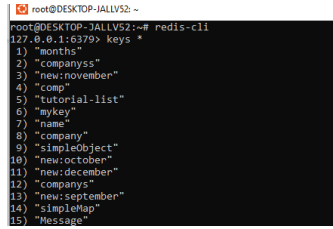
1. Navigate to Ubuntu Terminals.
2. Start the Redis-server and Redis-cli.
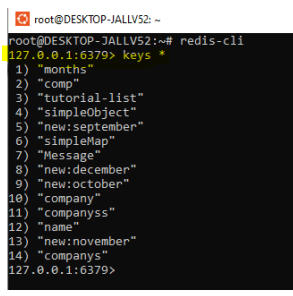
3. Then here we already created some keys on the cache. So, we can retrieve all the keys by using the keys * command.
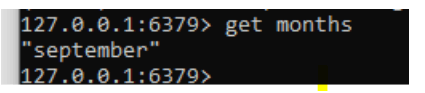
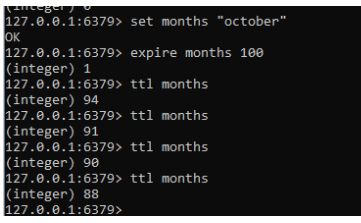
4. We can use any of the keys like month so the command gets months.
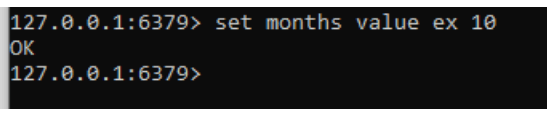
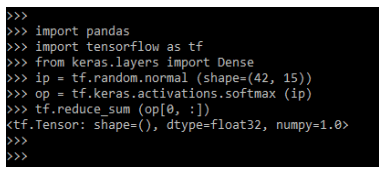
5. Set the key with timeout expiration for some format like seconds, then the command is like below:
Command:
Set months value ex 10Output:
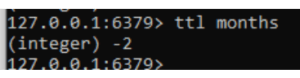
6. To check the expire time by using ttl months.
Redis Expiration Four Ways
Mainly the expire command will come out with additional operators to implement some additional conditions for setting the expiration time.
It has the following option types below:
- NX
- GT
- LT
- XX
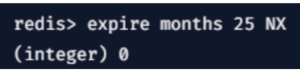
1. NX
It expires the key time if the key is set only then it has no expiry.
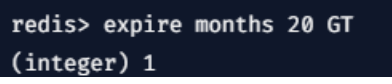
2. GT
If the key expiration time is set, then it creates greater than that of the current key.
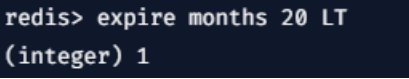
3. LT
It is the opposite of GT key expire options, so it shows less than the current one.
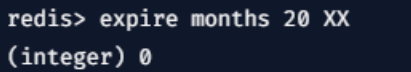
4. XX
Expire time is set to validate only if the existing key is expired.
Example of Redis EXPIRE
Given below is the example mentioned:
1. Keys *
2. Set comp “dell” EX 20
3. ttl comp
4. expire comp 20
Output:
FAQ
Given below are the FAQs mentioned:
Q1. Define timeout.
Answer:
The timeout or expiration time will be cleared automatically by using some default commands like GET, SET, DEL, etc. The user session will be cleared automatically.
Q2. What is the key expire accuracy?
Answer:
The expire accuracy is the default value and it will perform only if the expire error is thrown so that for the Redis 2.4 version it could be 0 to 1 second on timeout while in Redis 2.6 and later versions, the expire error is 0 to 1 millisecond timeout.
Q3. How redis keys expire?
Answer:
Whenever the user is to be accessed the existing key and that key is already on the timeout operation the key is denoted as expired.
Conclusion
Of course, this is insufficient because there are keys that have expired and will never work again. These keys should have expired by now, so every so often Redis tests a random subset of keys among those that have an expire set. The keyspace is cleared of all keys that have already expired.
Recommended Articles
This is a guide to Redis EXPIRE. Here we discuss the introduction, and how to use keys expire command. redis expiration four ways and example. You may also have a look at the following articles to learn more –