Updated April 20, 2023

Introduction to Linux User Permission
The following article provides an outline for Linux User Permission. In Linux, like any other operating system, simultaneous multiple users to work on the same server. The working of one user does not disrupt the working of another. In the long run, when multiple users work simultaneously, there is a possibility of sharing files across each other and this leads to a condition where there is the risk of exposing some classified piece of information or even lead to data loss due to multiple users having the access to write or modify.
To counter this issue, Linux has a feature of restricting the users on the basis of who should have what power and that the entire concept of which user needs to get what power lies with User Permission. And with the upcoming concept of a cloud-based system, user permission in Linux now plays an even bigger role for the developers to carefully look at.
Syntax of Linux User Permission
Let us look at the syntax of the user permission. Whenever one looks at user permission, only one thing resides in the minds of people looking towards it and that is how to change. But, that is just one part of it and the other part is on the how part along with extra utilities which user permission in Linux is capable of.
Given below are the 5 commands:
1. chmod: This command is used for modifying the access rights.
Syntax:
chmod <Permission Number>FileName2. su: This command enables the actions to be taken as a superuser.
Syntax:
su3. sudo: This command is also same as su.
Syntax:
sudo4. chown: This is used for changing the file ownership.
Syntax:
chown <username> FileName5. chgrp: In order to change file’s group ownership, this command is used.
Syntax:
chgrp <New Group> FileNameThough the next topic in the current section might not be exactly syntactical, but it is an important concept to learn about and this topic is users and groups. These are the entities to which the ownership and permission rules are applied to. Users are nothing but set of ids that can belong to a user of the system or maybe a placeholder for some admin work, which are either responsible for running non-interactive processes or background processes which are referred to as system users and the other is responsible for running interactive process by logging into the system and these users are referred to as regular users. Before we saw about superuser, which is nothing but a “big boss” which can override anyone’s permission.
On the other hand, Groups are nothing but a collection of zero or more users. Also, it is not necessary that a user belonging to a certain group can’t be a part of another group. This is very similar to a distribution list we have at workplace. One can be in a distribution list of HR’s mails and own’s team’s mail as well.
How does Linux User Permission work in Linux?
In order to know the working principle of user permission in Linux, we need to know small components which build the entire channel of user permission.
Where do we find the user permissions?
Syntax:
ls -lOutput:

Description:
Here the first block refers to the different modes which are present for a particular filename. The filename is mentioned as the last block like dummyfile.sh, newfile.txt. In the next section we will get to know the different components when we input ls -l.
Components of user permission:
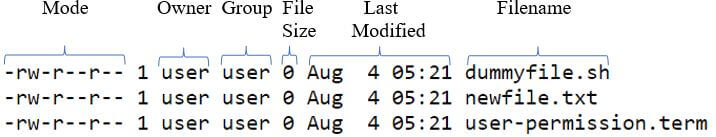
Here the mode is the major component in knowing user permission. Along with that, Owner and group are the second important things which plays an important role in understanding who the group individual will be affected by the permission.
In the next few sections let us see Mode, Owner and Group individually and in detail.
1. Mode: Mode comprises of various sub-components.
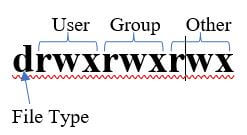
2. File Type: The first section mentions the File type. In a scenario, there are 2 types of files where one of them is normal and eventually represented by hyphen (-) and the other is special file type and typically represented by a character. For example, d means that the filename is eventually a directory. There are a lot of other special files but not a piece of essential information keeping this article in mind.
3. Permission Class: The next 9 characters refers to the permission class and each triad refers to each of the 3 groups. User is the one who is the owner of the filename, Group is the cluster to which the user belongs to and others is all the users who don’t fall in the cluster of Group.
Each of the classes have 3 different symbolic permission and they are:
- R: This refers to provide only read access to the file.
- W: This refers to provide write access to the file, which includes read access as well.
- X: This refers to provide execute access to the file, which includes read and write access as well.
In case any of them is not to be provided we use hyphen in place of that. For example, r– means that the file will have only read access to the class.
Now that we have understood the different aspects of user permission, next we would look at how do we change the permission of a particular file. For this we will use the chmod syntax.
Example
For the file dummyfile.sh we would first try to run the file, and in the process, we would encounter an error. Next we will change the user permission of user to executable and then try to run again and analyze the output.
Code:
Before executable permission
ls -l
./dummyfile.shChanging the permission
chmod 744 dummyfile.shExecute script
./dummyfile.shOutput:
Before executable permission
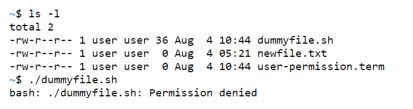
After changing the permission

Execute script
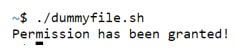
Explanation:
- The main idea here is to understand how we arrived at number 744. Here’s rule of thumb. If file needs read access, then 4, if it additionally needs write then add 2, and additionally, if it needs execute add 1.
- So, for user class, we have all 3 access, i.e. 4+2+1 = 7. For the other 2 permission class we have only read and hence 4.
Conclusion
With this we have taken a deep dive into user permission in Linux by looking at smaller aspects first in the start and then collectively started adding up and finally able to showcase a shell file getting executed when we changed the permission. One important thing before we wind up is to understand with great power comes great responsibility and hence the permission needs to be well thought of before providing that permission to user or group or others.
Recommended Articles
We hope that this EDUCBA information on “Linux User Permission” was beneficial to you. You can view EDUCBA’s recommended articles for more information.


