Updated April 1, 2023
Introduction to Firewall Rules
The firewall rules we need to use to manage the incoming traffic as well as the outgoing traffic. In the network, we are mainly following the two protocols like TCP and UDP. The TCP protocol will provide the message with acknowledging reliability. But on the other hand, in the UDP protocol, we are not getting any reliability on the message delivery to acknowledge. At the firewall level, generally, we are using the TCP protocol. Here, the firewall will work on level 7. Level 7 is nothing but an application level. On the firewall level, we can directly apply the policy at the application level also. The firewall rules management will vary from platform to platform like the OS, Hardware, etc. We can also manage the firewall rule in terms of the software level and the hardware level.
Syntax of Firewall Rules
In syntax, we can categories it into two different parts. First, it is on the actual hardware level, and second, it is on the operating system level.
- Hardware Level: We are having a number of firewall hardware devices available in the market. Every device belongs to a different vendor and having different features as well as the configuration. Hence, there are different methods to configure the file rules.
- Operating System: Every operating system like Linux, Windows, MAC has its own firewall. Here, if we need to do the firewall rule changes, you can use the UI or the CLI depending on the operating system availability.
Syntax:
firewalld [OPTIONS...]
- firewalld: We can use the firewalld keyword in the syntax or command. It will accept different arguments like compatible options etc. As per the provided input, the firewalld will be able to do the changes in the firewall level. Therefore, the firewalld command will help to manage the different firewall related tasks as well.
- OPTIONS: As per the requirement, we can provide the different flags as the option that is compatible with the firewalld command.
How Firewall Rules Works?
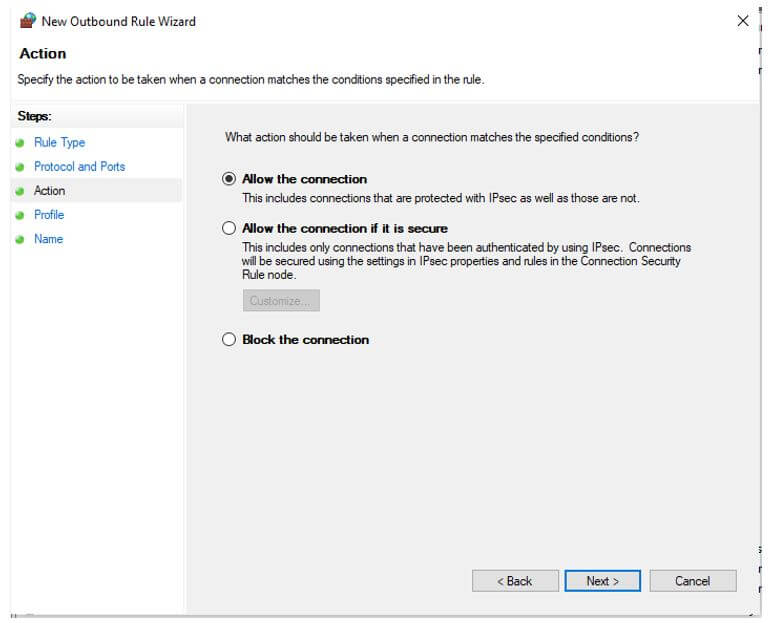
- As we have seen, the firewall rules are for traffic filtration. While we are adding any firewall rules, the rules entry will be made in the firewall config. When any network traffic comes, then the files will check the set of rules available. As per the rules, the firewall will take the decision. The decision has three options like accept, drop, or reject. Every action has its own meaning. The same keyword will help the firewall to take the necessary action on the same. In other words, the accept, drop or reject is acts as an action for the firewall. As per the necessary action, the firewall will take the necessary action. If accepted, the firewall will allow the network traffic to flow on the specific URL or the port. If it is a reject action, then the firewall will block the network traffic to flow on the specific URL or the port and provide the error message like “unreachable” error. If it is a drop action, then the firewall will drop the network traffic to flow on the specific URL or the port without any error message.
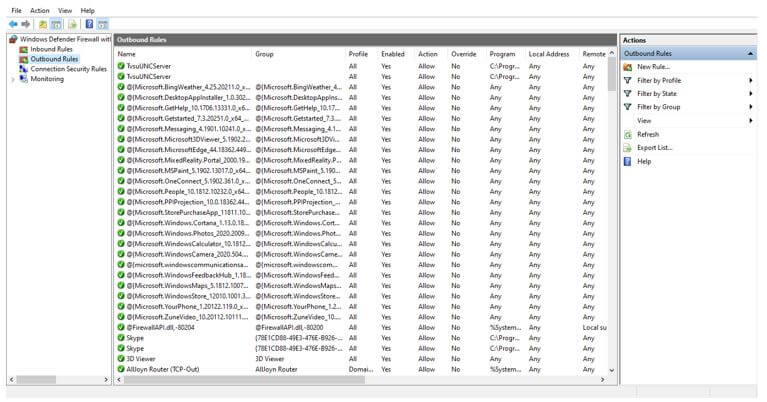
- In the firewall rules, it depends on the incoming and outgoing traffic. In the normal server and client communication, there is incoming and outgoing traffic. The incoming traffic will help to understand the network tariff or the network packet is coming from the external world. The traffic is having basic information like the port no, URL address, data information, etc. In the incoming firewall rule, we need to identify that the data or the network traffic comes from the external world. Which is correct or not. If it is correct, then only the firewall will allow passing the traffic to the system. Similarly, there is outgoing traffic. Normally in the outbound rule, we are open for all the network traffic. It will depend on the requirement that we need to define the outbound rule or not.
Examples of Firewall Rules
Given below are the examples of Firewall Rules:
Example #1
Firewall Rules: At the Windows Platform.
As we have seen, there are different firewall devices (from different vendors) available. Therefore, we need to follow different processes and methods in terms of the firewall rule. Similarly, we can manage the firewall rules in terms of the hardware or the software level also. Here, we are working on the windows operating system firewall rules.
Code:
It is not a specific syntax; we just need to follow the access flow.
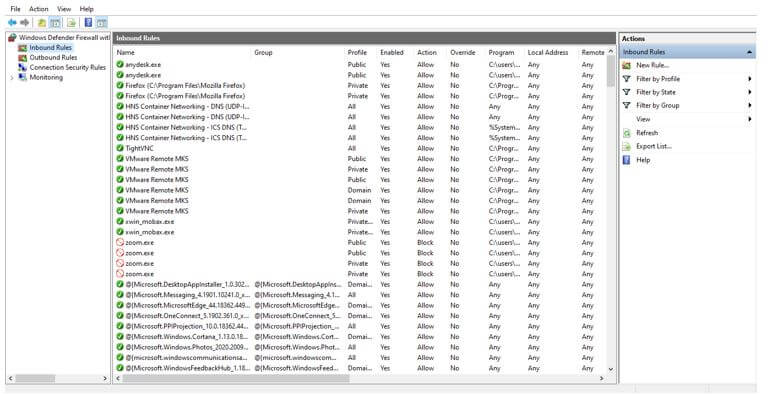
Windows key -> search for control panel -> windows firewall -> Advance setting -> Click for the new rules.
Explanation:
- As per the above flow, we are able to add the new firewall rule in the Windows environment. In the windows environment, it is a bit easy to do that. But we need an administrator or full access to the respective operating system.
Output:
Example #2
Firewall Rules: At the Linux Platform.
In every operating system, the firewall service is running on. We can also manage the firewall rules also. For example, it will help to allow or disable the network traffic in the system.
Code:
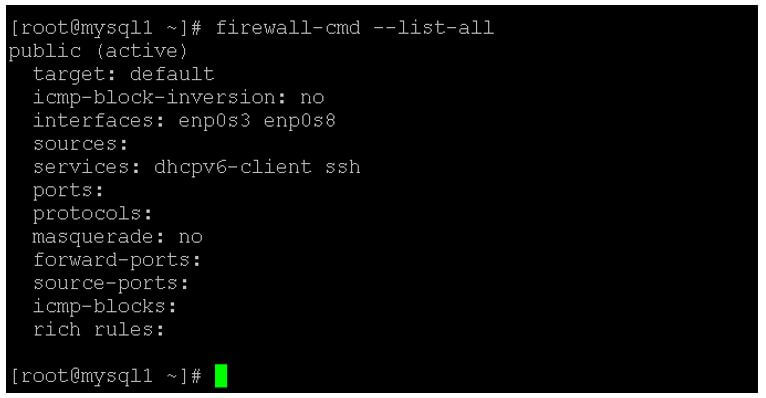
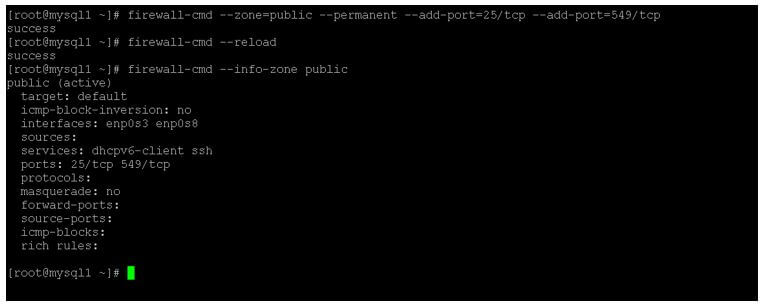
firewall-cmd --zone=public --permanent --add-port=25/tcp --add-port=549/tcp
firewall-cmd –reload
firewall-cmd --info-zone public
Explanation:
- As per the above command, we are using the 3 commands. As per the below screenshot, we are getting the default firewall zone information. We are doing changes in the firewall rules and adding the new rule with the ports 25 and 549 ports.
Output:
Conclusion
We have seen the uncut concept of the “firewall rules” with the proper example, explanation and command with different outputs. It helps to filter the inbound network traffic as well as the outbound network traffic. The firewall is working on the TCP layer at level 7.
Recommended Articles
This is a guide to Firewall Rules. Here we discuss the introduction, how firewall rules works? And examples, respectively. You may also have a look at the following articles to learn more –