What is EDI Security?
Electronic Data Interchange (EDI) security refers to the measures and practices that protect the electronic exchange of important information between businesses. It employs measures like blockchain to defend against cyber threats and unauthorized access. EDI security also follows the established rules and standards to maintain trust and dependability during business transactions.
EDI has revolutionized how businesses communicate smoothly. However, as more and more businesses depend on EDI, enhancing its security is crucial. The world of EDI security is evolving rapidly, bringing exciting developments that guarantee businesses can share important information with confidence and strong protection.
Understanding the Shift in Threat Landscapes
The world of Electronic Data Interchange (EDI) security is at a crucial point, facing significant changes due to the ever-growing cyber threats. Understanding these shifts is essential to navigate the complex challenges surrounding data exchange. Now, let’s look at the key challenges:
1. Rise of Sophisticated Cyber Threats
Cyber threats have become more complex. Malicious actors use fancy techniques such as ransomware, phishing attacks, and sophisticated malware to target weaknesses in EDI security systems. To keep your digital information safe, you need to be proactive and strengthen the security of these systems against these tricky threats.
2. Vulnerabilities in Data Transmission
Intruders take advantage of vulnerabilities in EDI networks’ data transmission process. They seize unprotected data or manipulate the transmission of information, finding ways to access crucial data without permission. This shows that it is really important to have strong security to protect against these kinds of attacks.
3. Data Privacy and Regulatory Challenges
The increasing number of data privacy regulations complicate EDI security. The GDPR and CCPA are two examples of these regulations, and they make it necessary to take extra steps to ensure that personal and important information shared through EDI is kept safe.
4. Emerging Threats from Quantum Computing
The rise of quantum computing could be a problem for regular ways we keep information safe. Quantum systems are really powerful and might make our usual encryption methods not work as well. So, we must start thinking ahead and develop new ways to keep our digital information safe from these super-strong quantum-enabled threats.
How does Quantum Computing Impact EDI Security?
Encryption is a key protector of data integrity and confidentiality in EDI security. It uses advanced algorithms to secure transmitted data, making it unreadable to unauthorized parties. In response to the emergence of quantum computing, developers have actively created quantum-resistant encryption algorithms to combat future threats.
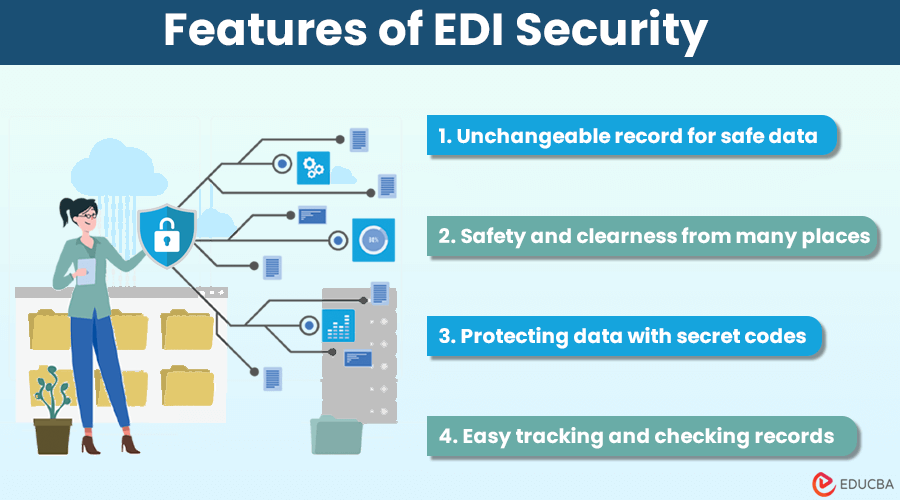
Key Features of EDI Security
EDI security adopts technologies such as blockchain to strengthen the overall security of electronic data interchange systems. Here are some key features:
1. Unchangeable Record for Safe Data
Blockchain acts like a super-secure digital notebook that creates an absolute record of transactions. Once it writes something down, it can’t be erased or changed. It ensures that all the information in digital documents is trustworthy.
2. Safety and Clearness from Many Places
Imagine keeping your important information in multiple places instead of just one. That’s what blockchain does. It spreads the data to keep your information safe if one place has a problem. Also, everyone involved can see what’s happening, which makes things clear and builds trust.
3. Protecting Data with Secret Codes
Blockchain uses secret codes to ensure the safety of information. Each piece of data has its secret code, and if someone tries to change something, it becomes really obvious. It keeps our information secure and prevents anyone from playing tricks.
4. Easy Tracking and Checking Records
Blockchain makes it easy to follow and check all the actions in a digital exchange. Everything is easy to track and check, whether buying or selling. It helps solve problems and ensures everyone is accountable for what they do.
Compliance and Regulatory Adherence
Businesses need to follow the rules and standards in their industry. EDI tools now work with specific rules like HIPAA and GDPR to ensure they protect information properly. It helps companies avoid legal problems and build trust with their coworkers. Here are some key points ensuring compliance and best practices in business EDI security:
1. Ensuring Data Integrity and Authenticity
The rules frequently require ensuring the safety of data in EDI transmissions. It employs encryption, digital signatures, and audit trails to verify the data’s origin, confirm its authenticity, and demonstrate that it remains unchanged. These measures aid in adhering to the rules and establishing trust in the information for everyone involved.
2. Standardization and Interoperability with Industry Norms
Businesses need to use the same formats for their data. It could be like ANSI X12, EDIFACT, XML, or other industry-specific protocols. Using these formats helps different businesses understand each other easily and follow the rules.
3. Documentation and Record-Keeping Practices
Businesses need to keep good records of their transactions and communications. It helps show that they follow the rules and makes it easier to solve problems or answer questions if there’s a disagreement.
4. Risk Management and Mitigation Strategies
Following the rules means being ready for things that might go wrong. Businesses need to think about possible problems, find ways to stop them and have backup plans just in case. It helps them stay on track and keep following the rules.
5. Continuous Monitoring and Adaptation
Following the rules isn’t a one-time thing. Businesses must keep watching and be ready to change if the rules or technology change. It helps them always follow the rules and stay on the right track.
Final Thoughts
Keeping electronic data interchange (EDI) secure is changing a lot. It is happening because there is a crucial need for strong protection against cyber threats. Adopting these improvements ensures safe data exchange and establishes trust and dependability in today’s business interactions.
The effort to make EDI security extremely strong is still happening. As technology improves, the plans and tools to keep data exchange safe must also improve. This way, we can look forward to a future where communication flows smoothly and securely in a strong protective system.
Recommended Articles
We hope this “EDI Security” article was informative and beneficial. To learn more, refer to the below articles.