Updated March 17, 2023
Introduction to Digital Signature Cryptography
Digital signature cryptography is nothing but a process of encrypting the digital certificates, using various encryption algorithms like Message digest, message digest 5, Secure Hash algorithm, ElGamal encryption, etc., that encrypt the digital certificates to avoid the attacks on digital certificates and provides the security.
The Cryptography of a digital signature is possible with two key terms:
- Private Key
- Public Key
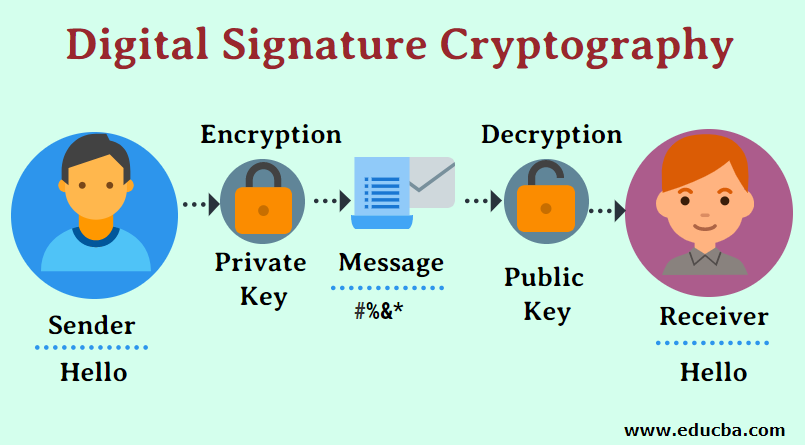
Private Key: The account holder holds a key which is a random hexadecimal number. Private Key will be confidential to the account holder rather than exposed to the real world.
Public Key: A random hexadecimal number that is shared publicly. To create a public cryptography digital signature, the message will be signed digitally first; then, it is encrypted with the sender’s private key and with the public key of the receiver. To decrypt the messages shared between the sender and receiver, the receiver has to decrypt the inner layer of the information with the Public key of the sender and decrypt the information’s outer layer using the private key the receiver holds.
Digital Signature Cryptography Architecture
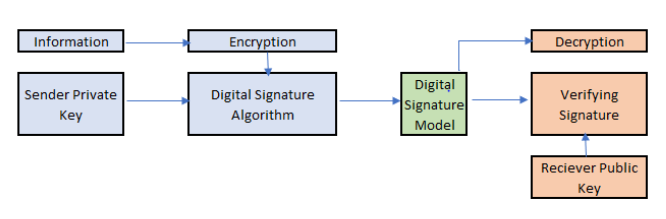
To perform digital signature using cryptography, the following has to be carried out:
The message/information should be encrypted using a hashing function with the sender’s private key in the sender end. The information will be forwarded to the receiver’s end with the intermediate digital signature model. The receiver verifies the digital signature by decrypting the information received using the hashing function on the receiver’s end. The decryption will be performed by extracting the inner layer using the public key and the private key’s outer layer. One major challenge to securely share information is to send the message in an encrypted format. In Cryptography, with a digital signature having a public key shared with the external world, there is a chance someone might spoof the encryption.
Encryption of digital signatures can be carried out in two major forms:
1. Digital Signature Followed by Encryption
In this method, the sender signature is exploited by the receiver and the information is shared with the external party without encryption. As this form is less secured, this is not preferable in the industry.
2. Encryption Followed by Digital Signature
The industry’s most common approach is encryption, followed by a digital signature where the sender sends the encrypted data with the digital signature. When the receiver receives the message on its end, it will decrypt the message shared by the sender using the sender’s public key and the receiver’s private key.
Cryptography Digital Signature with RSA
The following code snippet will explain how cryptography with a digital signature is implemented in real-time in python and also will explain how the encryption and decryption are carried out with digital signature using RSA. To perform cryptography with a digital signature, we require the pycrypto package installed, then write the below snippet.
importCrypto
fromPublicKey importRSA
fromCrypto import RandomTo perform cryptography with the digital signature, we require the initialization of private key and public key. We create a function to generate RSA keys which will have a private key and public key:
defrsa_keys():
l=1024
private_key = RSA.generate(l, Random.new().read)
public_key = private_key.publickey()
return private_key, public_key
The above snippet returns the private key and public key.1. Encryption Function
defencrypt(public_key,text):
c_text=public_key.encrypt(text,32)[0]
val_cipher=base64.b64encode(c_text)
return val_cipherWe use the above code to encrypt the message, which will take rsa_publickey and text as parameters to the encrypt function. The encrypt function will perform the public key encryption and generate the cipher; the generated cipher is returned when the function call is invoked.
2. Decryption Function
defdecrypt(private_key,val_cipher):
d_cipher = base64.b64decode(val_cipher)
text = private_key.decrypt(d_cipher)
return textCryptography with a digital signature using public-key encryption and text decryption carried out using the private key. To understand the meaning of encrypted text shared as a cipher, we have created a decryption function. The function takes private_key and the cipher generated by the encryption function. Using the decode method creates a decrypted cipher and uses the decrypt method; it will return the decrypted text.
3. Implementation
In this sample, we will look at how the encryption of text is carried out and how it is decrypted back to the original text using the private key is explained. The encrypt and decrypt function will be used in the sample to show how to cipher will be encrypted and decrypted.
Code:
importCrypto
fromPublicKey importRSA
fromCrypto import Random
importbase64
defrsa_keys():
l=1024
private_key = RSA.generate(l, Random.new().read)
public_key = private_key.publickey()
returnprivate_key, public_key
defencrypt(public_key,plain_text):
c_text=public_key.encrypt(plain_text,32)[0]
val_cipher=base64.b64encode(c_text)
returnval_cipher
defdecrypt(private_key,val_cipher):
d_cipher = base64.b64decode(val_cipher)
text = private_key.decrypt(d_cipher)
returntext
private_key,public_key=rsa_keys()
txt=b"Hello Peers!"
enc_cipher=encrypt(public_key,txt)
print('**'*10)
print("The ecncrypted text is {}".format(enc_cipher))
print('**'*10)
dec_cipher=decrypt(private_key,enc_cipher) #decryption
print("The decrypted cipher text is {}".format(dec_cipher))
print('**'*10)Output:
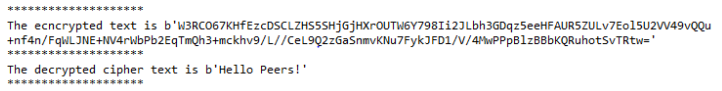
As we can see, the input text “Hello Peers!” passed to encrypt function is encrypted using the public key. The encrypted cipher passed as param to the decrypt function decrypts the original message shared using the receiver private key. To perform digital signature with cryptography will require the method ‘sign’ and ‘verify’, the sign will be performed by the sender using the private key, when the information is transferred to the receiver, verify function is carried out using the public key.
Merits & Demerits
Following are the merits and demerits explained.
Merits
- Improve the security of information transfer.
- Improve the workflow more digitalized.
- Better customer experience.
- Improve Business Efficiency and legal validity.
- Reduces manual effort and saves time.
Demerits
- It requires a lot of time for verification.
- It does not guard against vulnerabilities.
- The infrastructure and setting up of cryptography is not cost-friendly.
Conclusion
In the modern digital world, the digital signature algorithm with cryptography plays a vital role in providing a safe and secure environment and is one of the better tools for authentication. In the growing technological world, it will play a crucial part in terms of security against threats and vulnerabilities.
Recommended Articles
This is a guide to Digital Signature Cryptography. Here we discuss the Digital Signature Cryptography Architecture along with code implementation. You can also go through our other suggested articles to learn more –


