Updated February 21, 2023
Introduction to Bitbucket OAuth
First, Bitbucket did not support OAuth, but now it is supported OAuth. Normally OAuth means Open Authorization; it provides third-party services to the developer to request reading, writing, and access to the repository as per requirement. It also provides the exchange information functionality without any password. Our past OAuth execution just won big or bust admittance to assets. As an engineer building incorporations or additional items, you had less control. Also, a few activities that were impractical using OAuth, like cloning, are currently conceivable through OAuth2, empowering another arrangement of extra and reconciliation functionalities.
What is bitbucket oauth?
OAuth is the common validation technique for client communications with HTTPS distant URL for Git storehouses when 2FA is dynamic. Once a customer application has an OAuth access token, it tends to be utilized instead of a client’s secret phrase. Peruse more with regards to Bitbucket’s OAuth execution.
Bitbucket’s OAuth execution keeps the guideline determinations for OAuth 2.0, which is outdated. It carries out a nearly unique piece of OAuth 2.0 Refresh Tokens. Bitbucket’s Access Token’s lapse following 1 hour if it is not denied, rather than GitHub’s that terminate following one year. At the point when GitHub’s Access Tokens lapse, the client should expect in the standard OAuth verification stream to get another Access Token. Since this happens, in principle, once each year, this is somewhat easy. Since Bitbucket’s Access Tokens lapse consistently, it is a lot to anticipate that a client should go through the OAuth verification stream consistently. Bitbucket executes invigorate Tokens. Revive Tokens are given to the customer application simultaneously as Access Tokens. They must be utilized to demand another Access Token afterward, provided they have not been denied. As such, the help for Bitbucket and its utilization of its OAuth in the Git Credentials Manager contrasts with how VSTS and GitHub are executed.
As a matter of course, for verifying against private Git archives, Bitbucket upholds SSH and username/secret key Basic Auth over HTTPS. Username/secret phrase Basic Auth over HTTPS is additionally accessible for REST API access. Furthermore, Bitbucket upholds App-explicit passwords, which can be utilized using Basic Auth as username/application explicit secret key.
Use of bitbucket oauth
Now let’s see why we need to use Bitbucket OAuth as follows.
OAuth was made as a reaction to the immediate verification design. This example was made renowned by HTTP Basic Authentication, where the client is provoked for a username and secret word. However, essential Authentication is as yet utilized as a crude type of API verification for server-side applications. Rather than sending a username and secret phrase to the server with each solicitation, the client sends an API key ID and mystery. Before OAuth, locales would invite you to enter your username and secret key straightforwardly into a structure, and they would log in to your information (for example, your Gmail account) as you. This is frequently called the secret key enemy, for example.
A unified character was made for single sign-on (SSO) to make a superior framework for the web. In this situation, an end client converses with their personality supplier, and the character supplier produces a cryptographically marked symbol which it hands off to the application to confirm the client. The application confides in the character supplier. However, long as that trust relationship works with the marked statement, you’re all set.
BitBucket Cloud OAuth
Now let’s see how we can enable Bitbucket Cloud OAuth as follows.
- First, we need to generate the redirect URI in our account; generated URI we can use with authorization services, and by using this URI, we can determine the source of login requests.
- In the second step, we need to generate a client ID for authorization services. The ID and mystery you store in the confirmation module tell the Bitbucket Cloud approval administration that each login demand is approved.
- When you have created the data, YouTrack uses it to confirm with the Bitbucket Cloud approval administration, duplicate the qualities into YouTrack and empower the module.
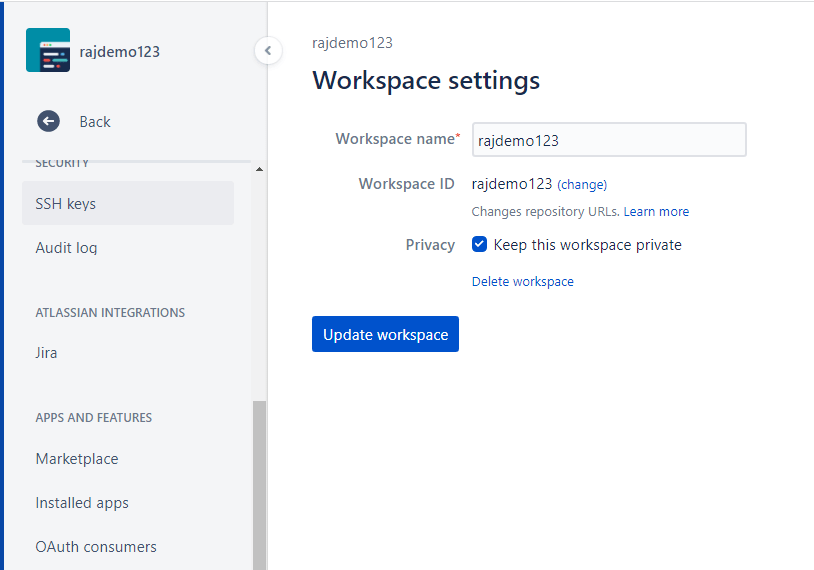
Under the workspace, we have the setting option, and inside the setting, we can see the OAuth consumer, as shown in the following screenshot.
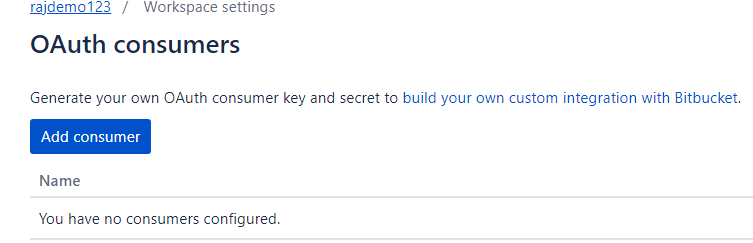
After clicking this button, we will get the Add consumer option, as shown in the following screenshot.
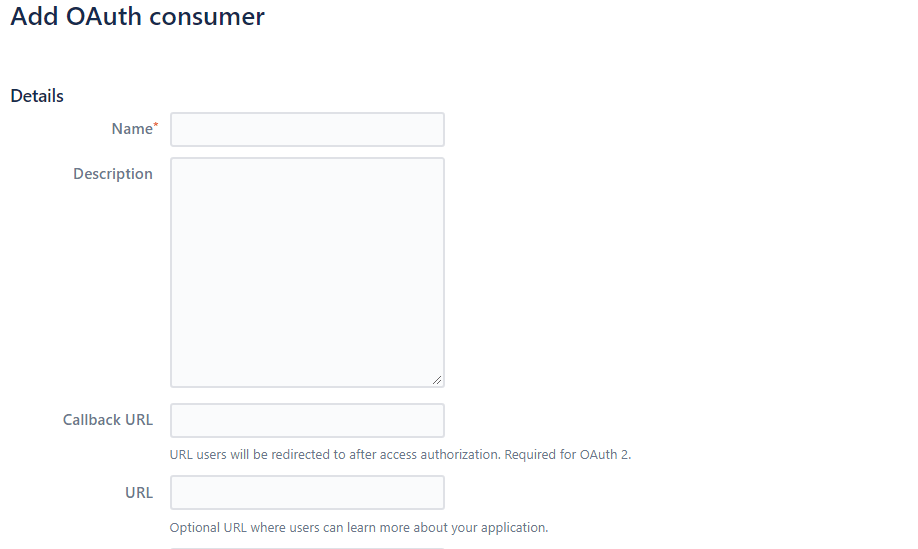
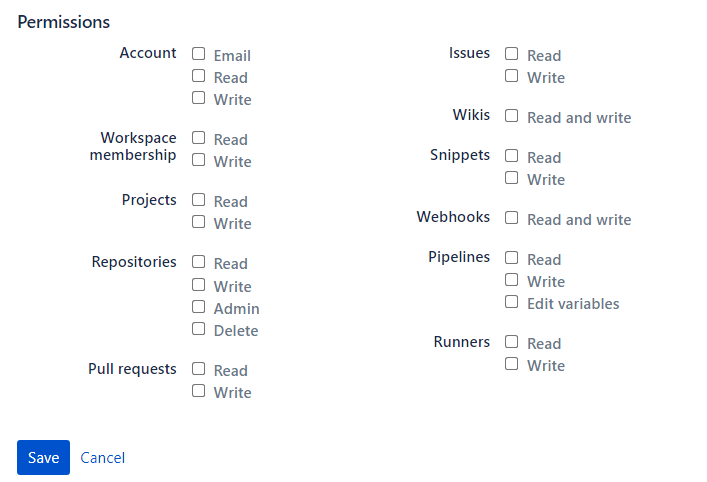
After clicking the Add consumer button, we will get some options and permission, as shown in the following screenshot.
We can select the permission and click the Save button per our requirements.
bitbucket oauth with Authenticate APIs
With the API Authentication application, It’s additionally conceivable to have the high-level elements that numerous venture groups were missing, such as applying straightforward lapse approaches by token, renouncing the badge of different clients, or assigning token creation. However, before we run a speedy examination of individual access tokens versus this new goal application, we should view what an outer master needs to say about the worth this new commercial center child brings to the table.
Now let’s see how we can set up the Authenticate API in Bitbucket.
- First, we need to select the setting of Bitbucket.
- In a second step, we need to click on the app password, which is presented inside the access management section.
- Now create a password.
- Give the application secret phrase a name connected with the application that will utilize the secret key.
- Select the particular access and authorizations you need for this application secret key.
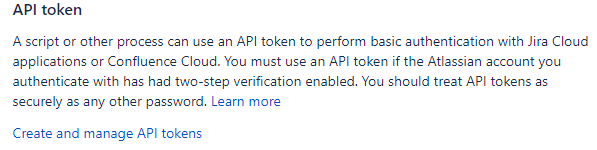
We have to Create and Manage the API token option inside the managed account, as shown in the following screenshot.
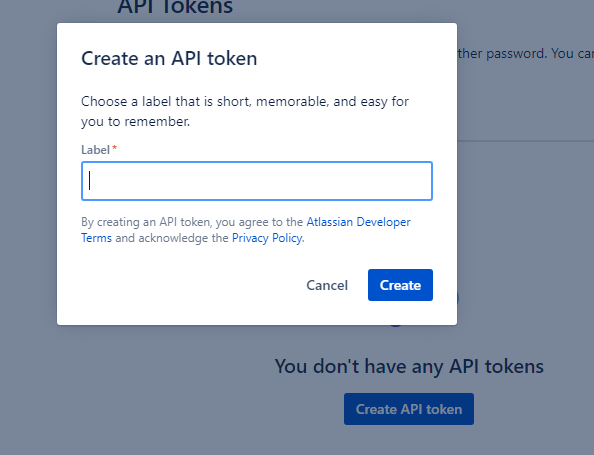
After clicking on this button, we get the following screen, as shown in the screenshot.
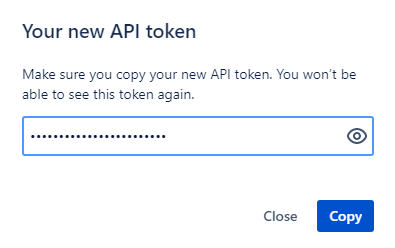
Here we need to provide a label and click on the Create button. After clicking the create button, we will get the following token, as shown in the screenshot.
Conclusion
From this article, we hope you get more knowledge about Bitbucket OAuth. Through this article, we get a basic idea about Bitbucket OAuth and try to explore the syntax and examples of Bitbucket OAuth. Finally, we can say that we learn how we can create an OAuth consumer and authentication APIs in Bitbucket.
Recommended Articles
This is a guide to Bitbucket OAuth. Here we discuss the basic idea of the Bitbucket OAuth and try to explore the syntax and examples. You may also look at the following articles to learn more –