Updated April 4, 2023
Introduction to Oauth2 vs OpenID
Oauth2 is defined as a framework for authentication which is open-source that helps users to secure their access in the form of pins and passwords with several applications in place. A token is used to access the application so that the passwords are not shared among any of the tools being used by the user. OpenID is an authentication protocol where users can authenticate any sites using the same user id and password if the sites agree for the same. This will eliminate the need of having several passwords and user ids created against similarly behaving websites.
Head to Head Comparison Between Oauth2 vs OpenID (Infographics)
Below are the top 5 differences between Oauth2 vs OpenID:
Comparison Table of Oauth2 vs OpenID
| Oauth2 | OpenID |
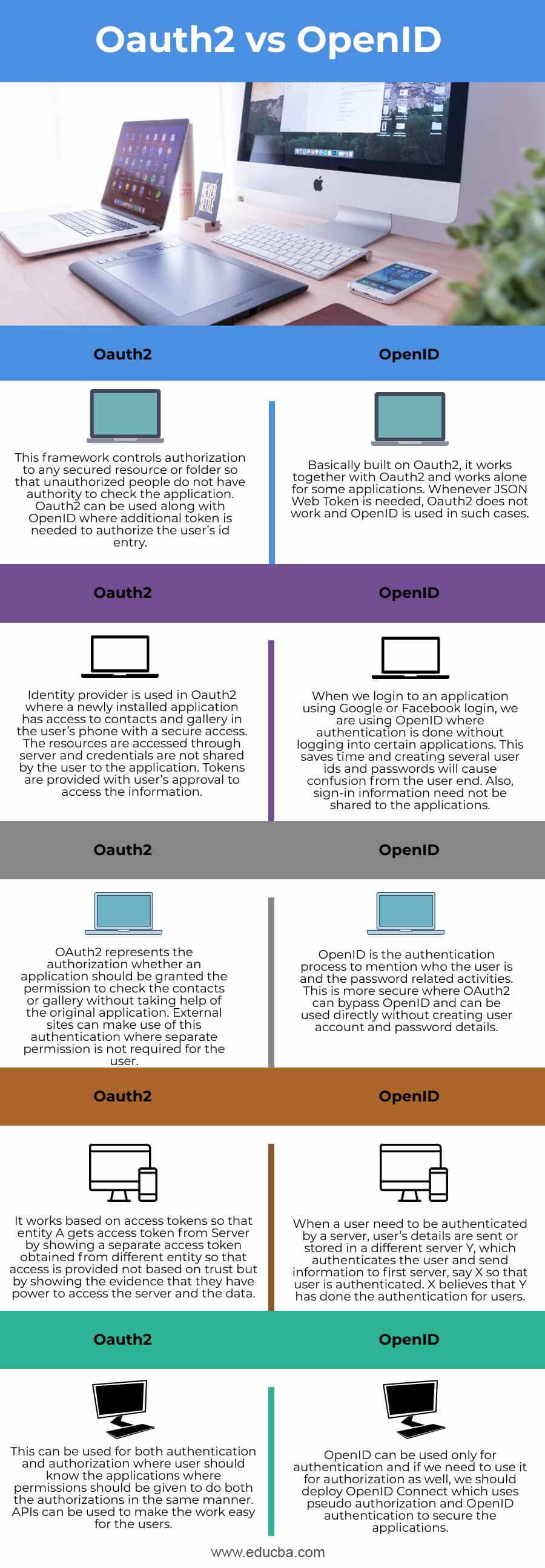
| This framework controls authorization to any secured resource or folder so that unauthorized people do not have the authority to check the application. Oauth2 can be used along with OpenID where the additional token is needed to authorize the user’s id entry. | Basically built on Oauth2, it works together with Oauth2 and works alone for some applications. Whenever JSON Web Token is needed, Oauth2 does not work and OpenID is used in such cases. |
| Identity provider is used in Oauth2 where a newly installed application has access to contacts and galleries in the user’s phone with secure access. The resources are accessed through the server and credentials are not shared by the user to the application. Tokens are provided with the user’s approval to access the information.
|
When we login to an application using Google or Facebook login, we are using OpenID where authentication is done without logging into certain applications. This saves time and creating several user ids and passwords will cause confusion from the user end. Also, sign-in information need not be shared with the applications. |
| OAuth2 represents the authorization of whether an application should be granted the permission to check the contacts or gallery without taking the help of the original application. External sites can make use of this authentication where separate permission is not required for the user. | OpenID is the authentication process to mention who the user is and the password related activities. This is more secure where OAuth2 can bypass OpenID and can be used directly without creating a user account and password details. |
| It works based on access tokens so that entity A gets an access token from Server by showing a separate access token obtained from a different entity so that access is provided not based on trust but by showing the evidence that they have the power to access the server and the data. | When a user needs to be authenticated by a server, the user’s details are sent or stored in a different server Y, which authenticates the user and sends information to the first server, say X so that the user is authenticated. X believes that Y has done the authentication for users. |
| This can be used for both authentication and authorization where users should know the applications where permissions should be given to do both the authorizations in the same manner. APIs can be used to make the work easy for the users. | OpenID can be used only for authentication and if we need to use it for authorization as well, we should deploy OpenID Connect which uses pseudo authorization and OpenID authentication to secure the applications. |
Key Differences of Oauth2 vs OpenID
- Access token is used by OAuth2 which helps in making requests for the same user in different applications. Also, additional resources can be authorized with the same OAuth2 access. Users should provide the application details and website details and OAuth2 does not have a discovery option by itself. A parameter should be added to the system for logging in or the user should create an API to make the login process direct. OpenID does not require users to enter the website details as they have a discovery mechanism of their own. Optimized user experience is provided by the application so that users need not check the authentication repeatedly. There is a disadvantage in the discovery process that some websites will not recognize OpenID in which case we need to provide the details of the authentication process. Registration of the applications can be easily done with the help of any public key exchange.
- Both OAuth2 and OpenID uses common architecture that makes the process easy for users. Identity of the users is protected using OpenID whereas access to the resources is protected using OAuth2. Authenticity is considered using different mechanisms but the underlying framework is similar. The signature for each authorization process and the registration is different for both OAuth2 and OpenID. Authenticity of each request has to be verified before giving access to the folders and applications which might require OTP or extra authentication from the Google site depending on the application.
- A simple example for both the applications is explained here. When I login to an application today, it should know that I have logged in yesterday and probably I will login tomorrow so that it will ask me whether it should save my identity. This is an example of OpenID. When I login to an application and it asks whether it should post a birthday wish on behalf of me or tweet from my account without knowing my password is an example of OAuth2.
- Unique URI is used in OpenID where the identity provider manages the users needs and authenticates on behalf of the user. Delegated authorizations are provided so that users can manage the application for a longer time than intended in OAuth2. It has extensions as well which help users to manage more applications with the same user id and password at the same time. OpenID has federated authentication where a client is liable to accept the providers initially and they can block certain providers if they don’t wish to login to their website.
Conclusion
Both the applications provide a separate and secure gateway to access the resources and manage them without much hassle in entering the password always. Framework need not be learned by users and they are considered as both powerful and secure in terms of authorization and authentication. Usage of both differs and hence we cannot recommend one over the other.
Recommended Articles
This is a guide to Oauth2 vs OpenID. Here we discuss key differences with infographics and comparison tables, respectively. You may also have a look at the following articles to learn more –

