Updated April 6, 2023
Introduction to Metasploit Framework
A Metasploit framework is a tool that is used to identify systematic vulnerabilities on servers and networks by cybercriminals and ethical hackers. Metasploit framework is very flexible and compatible with different operating systems and is open source, making it easily customizable. While using Metasploit, the team handling the pen testing can easily use a ready-made system or custom made to deploy it into the network or server to identify the weak spots of the network. After identifying the threats and weak spots, one can document them and address the network or server’s weaknesses and provide a solution for it.
Why do we need Metasploit Framework?
- Now a days, cybercrime and cyber attacks are very common. Hackers are always looking for chances to disrupt a network or for other unlawful activities. Once they identify any loophole in a network or a server, they attack and fetch sensitive information, creating a problem for the organisation or a government or country. For solving these issues, the Metasploit framework is used. The Metasploit framework can easily identify the weak spots of a network or a server. After the identification, it can get easily documented, and once the documentation is done, the organisation or the government can act on the weak spots and correct the weak spots before an attack happens. This is a very useful framework for companies, organisations or governments to save their sensitive information.
- As a result of its wide range of applications and its availability as open-source, now a days Metasploit is being used by most of the professionals from the field of DevSecOps to even the hackers. Metasploit is majorly used as it’s very easy to install and is reliable, which works on any system irrespective of platform or language. This software is very much popular amongst ethical hackers and hackers. There is an increasing need for professionals to understand and implement it on their systems.
How does Metasploit Framework Works?
- Metasploit uses port 3790 by default for running its features. After installing Metasploit. The information about the target can be accessed using port scanning, OS fingerprinting, OS fingerprinting and by using a vulnerability scanner for identifying the weak spots of the network. Metasploit is an open-source modular penetration testing program based on Ruby. Metasploit contains a suite of tools that allow us to test the vulnerabilities of network security of our network and do attack simulations and detections of escapes.
- For executing a precise action such as scanning or exploiting, the software is used, which is called the Metasploit module. Each and every task which Metasploit can perform is contained in the module. We can also say that the module is the core of the Metasploit framework. There are multiple types of the module, and each and every module depends on the purpose of the module and its action. The modules can be loaded at runtime, or they can even be loaded after initiating msfconsole.
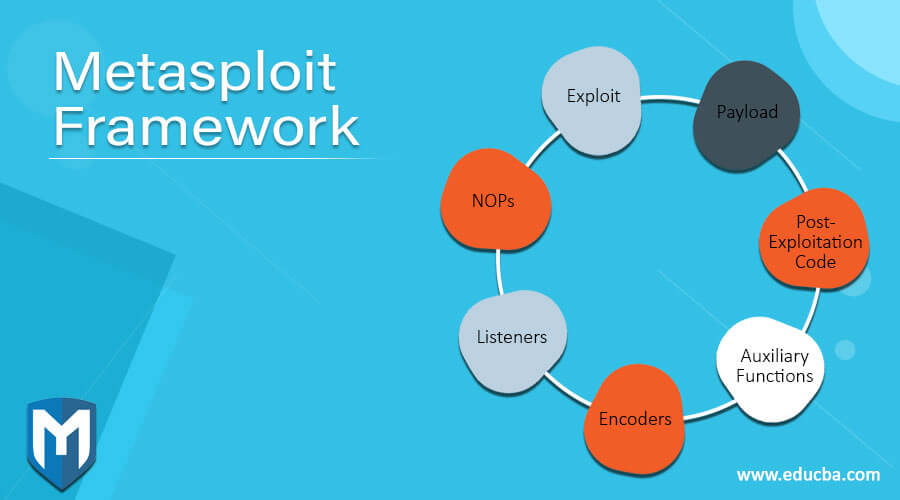
The following modules can be used in Metasploit.
1. Exploit
Exploit is a module of Metasploit which is used for taking advantage of the weak spots of the target system to create and access. The module performs a series of command to target a specific weak spot that got detected in a system or application. Exploit modules examples can be buffer overflow, web application exploits or code injection.
2. Payload
Payload is a module that includes a set of malicious codes which are run after effectively exploiting the target’s system infiltration. A set of instructions are included in this module which the target system could perform after getting compromised. The payload module also allows to control the way of connecting to the shell and crafting the system’s motive, which is the target after obtaining the control of that system.
There are different features available in the payload module, including small codes or even a small application. The payload module can open a command shell or meterpreter. A meterpreter is a highly innovative payload that allows us to write the DLL files, which strategically generate some new structures as required.
3. Post-Exploitation Code
Post exploitation code is a module that helps in testing deep penetrations. It permits us in gaining greater access and for collecting further information regarding the target system. Applications, hash dumps and service enumerators are some of its examples.
4. Auxiliary Functions
Auxiliary functions are a set of supplementary tools and commands which have no requirement of payloads for running. This module can be used for executing random functions which are not required to be linked with exploitation. Denial of service attacks (DoS), scanners, sniffers. SQL injection tools and fuzzers are some of the examples of the Auxiliary function.
5. Encoders
Encoders are a set of tools that are used for converting information or codes. For exploitation, the encoding of shellcodes are very important. Encoders are a kind of sensing devices that provides feedbacks that are used for determining digital signals.
6. Listeners
Listeners are a kind of malicious software that conceals itself for getting access to the target system. The metasploit framework has specific handlers which relate to the sessions being produced by the payloads. A listener can also sit actively and listen to the incoming connection or even get implanted to a bind shell and wait for the tester system’s connection. Bind shell always sits inactively to listen for an attacker who is making connections or sending instructions.
7. NOPs
No operation is abbreviated as NOP and is a type of instruction that prevents the payload from crashing. A set of arbitrary bytes is generated by the NOP, which is used to bypass the standard IPS/IDS NOP sled signatures.
Advantages and Disadvantages of Metasploit Framework
Given below are the advantages and disadvantages mentioned:
Advantages:
- One of the Metasploit framework’s major advantages is that it is open source and is actively developed.
- In Metasploit, switching between the payloads is very easy. Quick access is provided in Metasploit for changing the payloads which are using the commands. Adding a user or getting remote access to the desktop becomes easier in the Metasploit framework.
- Metasploit like Armitage provides a user-friendly GUI along with third-party interfaces. The penetration testing projects get easier because of these interfaces, which offer different services, including functions at a click, easy to switch worskspaces and vulnerability management.
Disadvantages:
- Metasploit framework is very difficult to learn.
- If the framework is not used correctly, it can crash your system.
- A deeper knowledge about the exploit environment is required.
Conclusion
On the basis of the above article, we saw about the Metasploit framework and how it works. We saw the usage of the Metasploit framework and its advantages and disadvantages.
Recommended Articles
This is a guide to Metasploit Framework. Here we discuss the introduction, why do we need the Metasploit framework? working, advantages and disadvantages. You may also have a look at the following articles to learn more –

