Difference Between Hackers vs Crackers
Most of us dread with the term Hacking. We are of the opinion that hackers are a threat to our computers and can take out whatever secret information they want to. But, that is not the case, and here we bring to you the exact difference between what a hacker and a cracker is. This will end all the myth regarding hackers. The Hackers and the Crackers are precisely the people who have extensive knowledge about computers and networks ranging from how they are built, how they work, the programming, the codes and everything else that relates to security. Generally, people are of the opinion that there is almost no difference between the two. However, this is not true. The two work for opposite interests. While one may work for good, the other works completely for malicious and criminal reasons. This is where the line is actually drawn between the two.
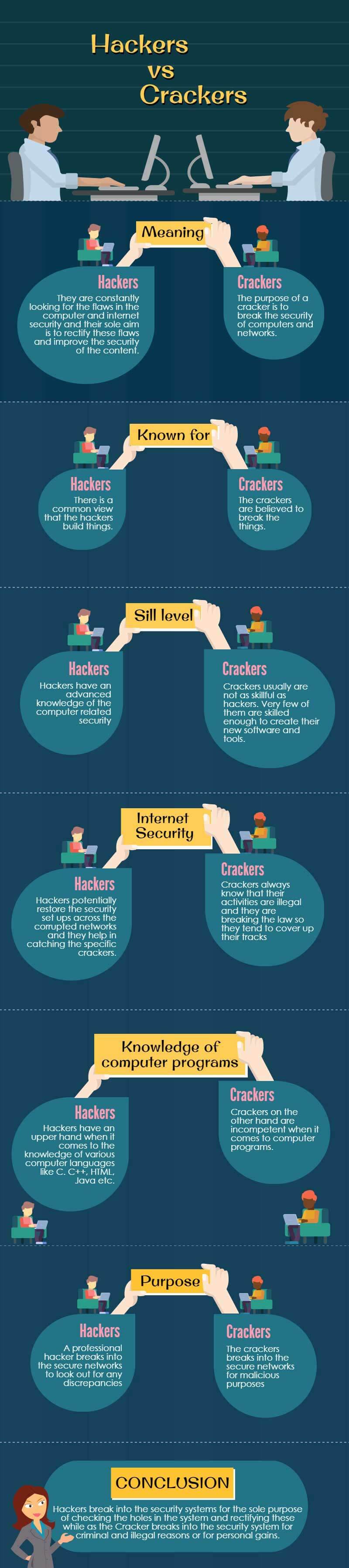
To put it in simple terms, one may define a hacker as someone who identifies the security systems’ flaws and works to improve them. While a cracker maybe someone who unethically exploits highly sensitive information and uses the flaws in the security systems to his advantage. The crackers usually breach the internet security and, without paying royalties, gain access to various software. On the other hand, hackers are internet security experts who may even be hired for locating and identifying the loopholes in the internet security systems and fix these loopholes and flaws. The hackers use their knowledge to help security systems, and the crackers use their knowledge to break the laws and disrupt security. The two are sometimes called as White Hats and Black Hats. The Hackers being the good guys, are called white hats, while black hats usually refer to the crackers which violate computer security for personal gains.
Head to Head Comparison Between Hackers vs Crackers (Infographics)
Following are the top difference between hackers vs crackers:
All about Hackers
The original use of the term hacker dates back to the 1950s when at the Massachusetts Institute of Technology, some students had a strong desire for experimenting and learning about technology. A hack back then meant something very original and ingenious and solely meant to explore the arena of computers and technology. Currently, the terms are used in a rather negative sense. And this is because most of the times, people confuse the term hacking with cracking. But it is totally not to be confused with crackers. We will deal with the crackers in detail later.
White Hats, as they are sometimes called, are mostly the programmers. They acquire advanced knowledge of programming, computer languages and codes. They are the ethical hackers who stay within the limits of the law. They do not access any system or network illegally. They are constantly looking for flaws in computer and internet security, and their sole aim is to rectify these flaws and improve the security of the content. The companies hire these white hats in order to audit and check their network security. These hackers work as professionals and correct the flaws with their advanced knowledge of the area and reduce the risk that might put the security of the company at stake. They discover the weak points in the network securities, work tirelessly, and put in their best efforts to seek solutions to these network issues. They establish the reason behind these loopholes and work for fixing them.
What interests these Hackers?
They are interested in knowing how things work. They like to explore and discover computer systems, programming and networks. While some may only be interested in learning things, others turn their passion into their profession, thus making them professional hackers. They are essentially very well acquainted with all sorts of software tools, techniques and codes that the crackers know. They know how a cracker would attempt to attack any content which is meant to be secure on the websites and across computer systems. They design exactly such software and tools that a cracker would use, and then they work on improving the system with more security tools and techniques. This ensures that the computer systems and the network systems become secure enough to not be thwarted by the crackers. The white hats also break in the security, but their purpose of breaking in is entirely non-malicious. They do this only to test their own systems for security purposes, and they do it legally with the permission of various companies and firms that hire them for this job. White hats come under the banner of ethical hacking, which doesn’t involve any illegal practice of hacking. Professional hackers mean no harm to any company or individual.
All About Crackers
We have learnt about hackers, how they work, what their interests are and what they do. Now when we talk of crackers, we must know that crackers are also hackers. But their ways of works differ a lot. While a hacker works totally in the interest of a company or an individual, the cracker works totally in the opposite manner. The purpose of a cracker is to break the security of computers and networks. It is an illegal activity. They make use of their knowledge to make personal gains and breach security across networks. They acquire extensive knowledge and learning about computers, their programming, software, codes and languages and use them to break into computers for criminal gains.
The crackers are also known as Black Hats. They gain access to the accounts of people maliciously, and they can misuse the secured information across networks. They can steal credit card information; they can destroy important files, disclose crucial data and information or personal details and sell them for personal gains. Their purpose can range from little personal gains to bigger criminal interests. They can make employees of a company divulge highly secure information. They violate computer security. Once they have gained control over a system, they can do anything like steal data, destroy it, use it to their advantage etc.
What interests these Crackers?
While some crackers are driven by sheer publicity of their abilities in the field of hacking, some do it for criminal and malicious purposes. They intentionally breach the computer and network security merely for profit, or maybe there is a challenge in it. They are interested in gaining access to various programs and software without paying royalties. The only purpose they have is illegal hacking leading to security problems. There may be theft from credit card holders’ accounts, important data may be lost, and secure information may be divulged. Some crackers are interested in modifying the software by reverse engineering. And they do this merely for amusement or to showcase their knowledge and abilities.
Types of Crackers
There are various types of crackers that include script kiddies, packet monkeys, s’kiddiots, lamers, warez d00dz (dudes), and wannabes. Usually, they are less skilled and do not possess the necessary in-depth knowledge about programming and codes. They almost always rely on the software tools created by others to carry out their operations. Most of the times, they do not know what this program really does. They only know the process of cracking the security networks, and they lack advanced knowledge. They are not much of a threat, but their threats cannot be ignored. They basically deface the web pages and replace them with their designs.
Hackers vs Crackers
There is a common view that hackers build things, and crackers break things. These are basically two entirely different terms. They may seem similar, but there are differences between how the two actually work. While hackers who have advanced knowledge of computer-related security, crackers usually are not as skilful as hackers. Very few of them are skilled enough to create their new software and tools. So they generally rely on certain not so reputed, in fact, the disrepute websites to download several automated programs to execute their deed. Hackers try to counter the potential threats that the crackers pose to the computer and internet security across varied networks. Crackers always know that their activities are illegal and they are breaking the law, so they tend to cover up their tracks.
However, the professional hackers being competent enough and quite skilful with their work, potentially restore the security setups across the corrupted networks, and they help in catching the specific crackers. Although most of the crackers are less skilled yet many of them are able enough. They possess advanced skills and extensive knowledge, just like professional hackers. They have the ability to create tools and software that help them exploit all sorts of weak points that they discover in the highly secured programs. This makes it even difficult to catch these crackers. Because they do not leave a trail behind, the number of skilled crackers is very low, yet we should not ignore them. They certainly pose a serious threat to internet security.
By now, we are well aware that the hackers are the ethical professionals while the crackers break into the security systems unethically and illegally. Besides this ethical difference, one of the major differences between the two is their understanding of computer systems and security systems. Their ability and inability to create programs and software tools is a major difference between the two. The hackers can write codes in multiple languages. They have the upper hand when it comes to the knowledge of various computer languages like C, C++, HTML, Java etc. also; they have a complete understanding of what these codes do and how these software work. Crackers, on the other hand, are inept when t comes to computer programs. They boast about their abilities to break into the security systems and use them to their advantage. The difference here is clear. The crackers break into secure networks for malicious purposes while a professional hacker does not. So, therefore, it is just how they work, which makes them entirely different from each other.
Conclusion
We can thus conclude to say that the Hackers break into the security systems for the sole purpose of checking the holes in the system and works on rectifying these while as the Cracker breaks into the security system for criminal and illegal reasons or for personal gains. The white hats perform the security tests according to a legal contract. The black hats do not follow any such agreement. They do so to violate the security of the systems. While a cracker keeps the knowledge of any vulnerability n a security system to himself and uses it to his own advantage, the hacker does so in order to aware the concerned company or an individual about the possible breaking that could lead them to considerable losses at the hands of the Crackers. Basically, we can say that ethical hackers use and apply their knowledge and experience to help maintain the security of a computer system and a network.
While the crackers use their knowledge, which generally is not much advanced, to break the law? The two terms are sometimes used interchangeably, but we have to know that the difference between the two is quite big and considerable. We might even say that this is respectful to be a hacker and insulting to be a cracker. Hacking is potentially more harmful than cracking because hackers possess in-depth knowledge of the programs, codes, etc. However, since they work solely for developing the security systems, they really do not possess any threats to the security systems. The crackers, however, possess serious threats to internet security. And this is a growing menace in the current times. Therefore it is significant to take proper legal action against the prosecutors and thus reduce the threats. The two terms are significantly similar, but the difference lies in the manner each tends to work. That is what makes the two so different. Therefore, we must not confuse these two terms and remember to do hacking legally and ethically and never think of cracking.
Recommended Articles
This is a guide to Hackers vs Crackers. Here we discuss the head to head comparisons with infographics along with career opportunity and certification. You may also have a look at the following articles to learn more –

