Why is Cloud Email Security Critical?
Most breaches still start the same way: with an email. A subject line that looks routine. A link that feels safe enough to click. A request for payment that does not raise alarms until the money’s already gone, unless cloud email security is in place to detect and stop it. Attackers use email because it works. Phishing harvests credentials. Ransomware spreads from one careless download. Business email compromise (BEC) scams drain accounts without ever dropping a file. For smaller organizations, even a single incident can be devastating. Systems go offline.
Revenue disappears. Trust with customers evaporates overnight. That’s why cloud email security has become the backbone of business defense. Built-in filters can not see everything. Cloud-based protection extends across users, devices, and networks, closing gaps that attackers count on.
What Cloud Email Security Really Means?
Email security is not one product or plug-in. It is not the spam filter that ships with your inbox. It is a strategy built on the assumption that someone will eventually click, and that attackers will occasionally slip past defenses. The point is not just blocking attacks, but also containing the damage when they succeed.
Cloud email security makes that possible. By connecting directly to hosted platforms like Microsoft 365 and Google Workspace, it monitors mail flow at the source. Suspicious logins, malicious third-party apps, or unusual mailbox rules do not hide for long. Protection follows users wherever they work, not just at the network edge.
Why Cloud Email Security Matters for Businesses?
Email carries what adversaries want most: contracts, invoices, account credentials, and financial approvals. Breaking into that channel does not just expose data; it interrupts the business itself.
Recent breach data indicate that ransomware is involved in nearly half of all documented incidents. Business email compromise continues to lead in direct financial losses. Both highlight the same point: default filters were not designed for this.
Organizations that treat cloud email security as a foundation are not only protecting files; they are also safeguarding their data and information. They are preserving continuity, reputation, and trust.
The Threats You are Facing in Email Security
- Phishing: Phishing is still the most common entry point. A fake invoice, a shared doc, a password reset. All it takes is one click.
- Business Email Compromise (BEC): Attackers posing as executives or vendors. The request looks normal until the money’s already gone.
- Spoofing: Forged sender details that make a malicious email look like it came from someone you trust.
- Ransomware: A single link or file can lock systems across a network. Recovery costs far more than prevention.
- Spam: Mostly noise, but inside the noise are links and payloads tuned to slip past filters.
These threats do not stay still. Attackers continually refine what works and discard what does not. Cloud email security helps businesses stay ahead by identifying patterns early and stopping attacks before they spread.
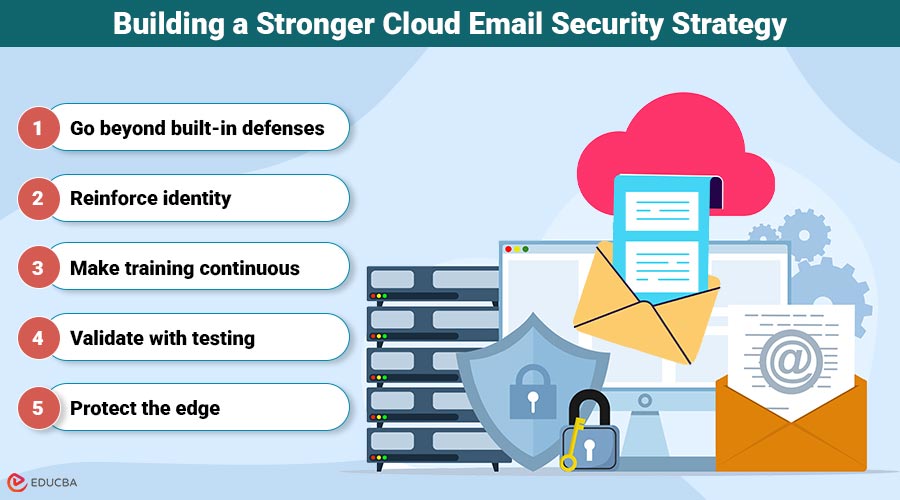
Building a Stronger Cloud Email Security Strategy
Technology matters, but people and processes do too. A strong defense combines all three.
- Go beyond built-in defenses:Native email clients prioritize usability over resilience. A dedicated cloud email security platform provides the adaptive filtering and deep analysis they lack.
- Reinforce identity: Multi-factor authentication, conditional access, and strong identity controls reduce the risk of takeover.
- Make training continuous: Human behavior can not be patched. Ongoing awareness keeps employees alert to phishing and impersonation.
- Validate with testing: Cloud penetration testing and simulated phishing campaigns expose weak points before adversaries find them.
- Protect the edge: Endpoint defenses, anti-malware, and VPN use for remote teams close gaps across distributed workforces.
- The principle is simple: every additional layer shrinks the attacker’s room to maneuver.
Prevention First with Cloud Email Security
Attackers will keep aiming at email. That’s not changing. Mistakes will happen, but the security strategy does not need to collapse because of them. A proactive model built on cloud email security demonstrates to customers and partners that your business prioritizes trust as a non-negotiable value.
The question is not if your inbox will be targeted, but when. The organizations that prepare now will be the ones still running tomorrow.
Final Thoughts
Email remains the number one entry point for cyberattacks, and businesses can no longer rely on default filters or outdated defenses. Cloud email security is not just an IT upgrade; it is a business necessity. By combining advanced technology, identity protection, and ongoing employee awareness, organizations create a resilient shield against phishing, ransomware, and business email compromise.
The companies that invest in cloud email security today are not only avoiding breaches but also protecting their reputation, customer trust, and long-term continuity. In a landscape where threats evolve daily, prevention is not optional. It is the standard.
Frequently Asked Questions (FAQs)
Q1. What is an email security policy?
Answer: It is the combination of technologies, practices, and rules that keep email accounts and communications safe from unauthorized access or attack.
Q2. Why is email security important for businesses?
Answer: Because email underpins operations, without adequate protection, attackers can steal client data, financial information, or intellectual property, risks that extend beyond IT and impact brand reputation.
Q3. What are the most common email threats?
Answer: Phishing, business email compromise (BEC), spoofing, ransomware, and spam continue to be the leading risks. Each demands layered defenses.
Recommended Articles
We hope this guide on cloud email security was helpful. Explore related articles on phishing prevention strategies, ransomware protection, and building stronger business cybersecurity frameworks to gain deeper insights into safeguarding your organization against evolving threats.