What is a Honeypot?
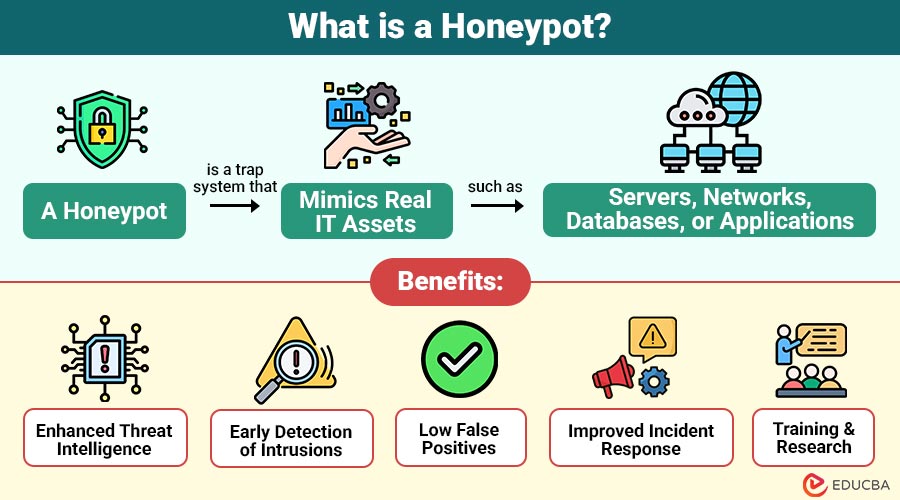
A honeypot is a trap system that mimics real IT assets such as servers, networks, databases, or applications. It is intentionally vulnerable or misconfigured to attract malicious actors. When attackers engage with the honeypot, security teams can monitor their tactics, techniques, and procedures.
In simpler terms, honeypots act like bait: they look appealing to hackers but serve the sole purpose of observation and analysis. Honeypots are proactive and intelligence-driven, in contrast to conventional security systems that emphasize prevention.
Table of Contents:
Key Takeaways:
- Honeypots act as digital decoys, tricking attackers into revealing techniques without harming real systems.
- They provide valuable threat intelligence, helping organizations adapt defenses against evolving cyberattacks effectively.
- Low false positives make honeypots reliable tools for detecting genuine malicious activity quickly and accurately.
- While powerful, honeypots need careful isolation, monitoring, and updates to prevent misuse by attackers.
How Does a Honeypot Work?
Here are the key stages that explain how a honeypot functions in cybersecurity:
1. Deployment
Security teams set up a honeypot to look like real servers or databases, tricking attackers into thinking they’ve found a valuable target.
2. Attraction
Fake weaknesses, like passwords or documents, are added to the honeypot to attract attackers and make them try to break in.
3. Engagement
When attackers interact with the honeypot, security professionals carefully observe their activities and study behaviors, techniques, and methods without risking harm to real production systems.
4. Data Collection
Honeypots carefully record everything attackers do—tools they use, files they move, exploits they try, and network info—giving detailed insights into their methods and motives.
5. Analysis
Security teams evaluate gathered intelligence to uncover attacker trends, refine existing defenses, build predictive models, and strengthen cybersecurity strategies against future intrusion attempts and emerging digital threats.
Types of Honeypots
They can be categorized according to their complexity and intended purpose:
1. Low-Interaction Honeypots
These honeypots show only a few fake services and allow little interaction. They catch simple attacks and automated scans, are cheap, easy to set up, and often have fake login pages.
2. High-Interaction Honeypots
High-interaction honeypots replicate real operating systems and applications, engaging attackers deeply. They yield detailed insights into attacker techniques but demand greater resources, strict monitoring, and careful risk management.
3. Research Honeypots
Designed for security research, these honeypots capture detailed insights into attacker behavior, malware evolution, and emerging exploits. They significantly advance global threat intelligence and cybersecurity defensive strategies.
4. Production Honeypots
Deployed in active enterprise networks, these honeypots act as early-warning systems. They detect intrusions quickly, minimize false positives, and complement existing security solutions by diverting attackers harmlessly.
Benefits of Honeypots
Here are the key advantages organizations gain by implementing these cybersecurity strategies:
1. Enhanced Threat Intelligence
Honeypots collect information on how attackers act and what tools they use. This helps organizations prepare for attacks, improve defenses, and stay more secure.
2. Early Detection of Intrusions
Acting as decoys, honeypots identify malicious activity faster than traditional security tools. They often detect intrusions before attackers compromise sensitive assets, enabling timely protective actions.
3. Low False Positives
Unlike intrusion detection systems, which may mistakenly flag harmless activity, honeypots only generate alerts when actual malicious interactions occur, drastically reducing false positives and wasted resources.
4. Improved Incident Response
With detailed logs of attacker actions, honeypots empower teams to analyze incidents thoroughly, patch vulnerabilities quickly, and improve coordinated, effective responses to ongoing cybersecurity threats.
5. Training and Research
Honeypots are safe setups where experts watch hackers, practice defense strategies, and improve skills to protect organizations better.
Challenges of Honeypot
While these cybersecurity measures offer significant advantages, they also come with certain challenges:
1. Detection by Hackers
Experienced attackers may identify honeypots through unusual behaviors or system fingerprints, choosing to avoid them entirely, reducing their usefulness in real-world scenarios.
2. Maintenance Overhead
High-interaction honeypots need constant care, updates, and monitoring to prevent misuse, which can be time-consuming for cybersecurity teams.
3. Limited Coverage
It only collects data from threats directly targeting them, leaving other potential attack vectors unmonitored, limiting their overall threat visibility and effectiveness.
4. Risk of Exploitation
If honeypots lack proper isolation, attackers may hijack them as platforms to launch secondary attacks, unintentionally amplifying risks to the organization.
Use Cases of Honeypots
Here are some real-world scenarios where these techniques are commonly applied:
1. Malware Analysis
Honeypots collect new malware in real situations, helping researchers study how it works, spreads, and where systems are weak to improve security.
2. Insider Threat Detection
Placing internally helps organizations detect suspicious employee actions, catching unauthorized access attempts and preventing potential insider threats before they escalate.
3. Spam Detection
Email honeypots act like fake email accounts to attract spammers, collect their messages and IP addresses, and help organizations block them, improving email security.
4. Deception in Enterprise Networks
Enterprises strategically deploy as decoys within networks, diverting attackers away from critical systems and gathering intelligence without compromising real assets.
5. IoT Security
IoT honeypots mimic vulnerable smart devices, capturing attack patterns against connected ecosystems, helping researchers strengthen IoT defenses against botnets and large-scale exploits.
Real World Examples
Here are some well-known implementations that highlight their practical applications in cybersecurity:
1. The Honeynet Project
A collaborative global research initiative employing honeypots to analyze cyber threats, generate intelligence, and openly share findings with the wider security community.
2. Kippo Honeypot
Kippo is a type of security tool called a medium-interaction honeypot. It pretends to be an SSH server to attract hackers. It records their login attempts, the commands they try, and the ways they try to break into a server. This helps study and understand hacker methods.
3. Glastopf
Glastopf pretends to be a vulnerable website to trick hackers into trying attacks like SQL injection or cross-site scripting, helping researchers learn how web attacks happen and evolve.
4. Dionaea
Dionaea is a tool that catches malware spreading through networks or shared files, helping experts study it and create better antivirus protection.
Best Practices for Deploying Honeypots
Here are some essential guidelines to ensure honeypots are deployed effectively, securely, and provide maximum value in cybersecurity defense:
1. Isolation
Place them in a fully controlled, isolated environment so attackers can’t use them to reach real systems.
2. Monitoring
Implement robust, continuous real-time monitoring and logging mechanisms to accurately capture attacker behaviors, tools, commands, and methods for effective threat intelligence gathering.
3. Regular Updates
Regularly update systems and settings to match real technologies and vulnerabilities, keeping the deception believable and effective against attackers.
4. Integration with SIEM
Connect logs and captured intelligence to centralized SIEM platforms, enabling advanced correlation, deep analysis, and improved organization-wide threat visibility and response.
5. Layered Security
It works together with firewalls, IDS/IPS, and antivirus tools to improve threat detection, without replacing your current security systems.
Final Thoughts
Honeypots are a powerful cybersecurity tool that blends deception, research, and intelligence gathering. They do not replace traditional defenses but act as a strategic complement, offering early detection, threat insights, and invaluable data for security teams. By deploying effectively, organizations can stay one step ahead of cybercriminals—turning attacks into opportunities for learning and strengthening their defenses.
Frequently Asked Questions (FAQs)
Q1. Are honeypots legal?
Answer: Yes, honeypots are legal as long as they are used ethically for research and defense, not for entrapping attackers.
Q2. Can attackers detect a honeypot?
Answer: Yes, skilled attackers may recognize signs of a honeypot. That is why realistic deployment is crucial.
Q3. Do honeypots replace firewalls and IDS?
Answer: No, honeypots complement other security tools. They are not meant to replace preventive defenses.
Q4. What industries benefit most from honeypots?
Answer: Financial services, healthcare, government, and any sector dealing with sensitive data gain significant value from honeypots.
Recommended Articles
We hope that this EDUCBA information on “Honeypot” was beneficial to you. You can view EDUCBA’s recommended articles for more information.

