What is Federated Identity?
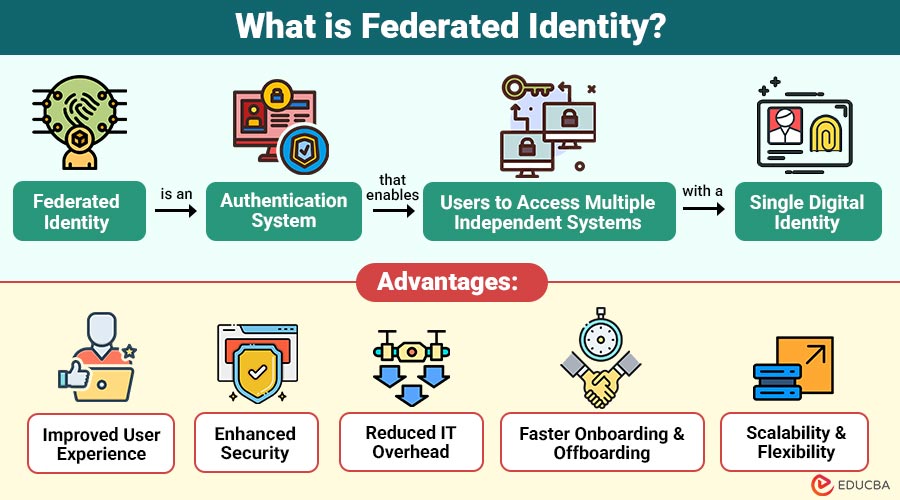
Federated identity is an authentication system that enables users to access multiple independent systems with a single digital identity. It establishes trust between different organizations or domains, enabling secure sharing of identity information.
In simple terms, federated identity lets users sign in once and seamlessly access multiple services without needing to authenticate again.
Example:
- Logging into a third-party website using a Google account.
- Using corporate credentials to access partner platforms.
Table of Contents:
- Meaning
- Key Concepts
- Working
- Common Standards
- Use Cases
- Advantages
- Limitations
- Advantages
- Limitations
- Real-World Examples
- Architecture
- Best Practices
Key Takeaways:
- Federated identity enables secure access across multiple systems with a single trusted digital identity, eliminating the need for repeated authentication.
- By centralizing authentication, lowering the number of passwords, and imposing uniform access controls, it enhances both user experience and security.
- Standard protocols like SAML, OAuth, and OpenID Connect ensure interoperability among enterprises, cloud services, and partners.
- Proper governance, monitoring, and least-privilege controls are essential to mitigate trust, availability, and privacy risks.
Key Concepts in Federated Identity
Below are the fundamental concepts that explain how federated identity enables secure authentication and trusted access across multiple systems and organizations.
1. Identity Provider
An identity provider authenticates users, verifies credentials, and issues secure identity assertions or tokens to trusted external service providers globally.
2. Service Provider
A service provider consumes identity assertions from an identity provider to securely grant users access to applications, resources, and services.
3. Trust Relationship
A trust relationship defines mutual agreements, policies, certificates, and security requirements, allowing service providers to rely on identity provider assertions.
4. Federation Protocols
Federation protocols are standardized frameworks that enable the secure exchange of authentication, authorization, and identity data across organizational boundaries between trusted systems.
How Federated Identity Works?
The federated identity process typically follows these steps:
1. User Access Request
A user attempts to access an application acting as a service provider, initiating a federated authentication request through secure redirection.
2. Redirection to Identity Provider
The service provider redirects the user to a trusted identity provider for authentication, without handling the user’s credentials or passwords.
3. User Authentication
The identity provider authenticates the user using passwords, biometrics, or multi-factor authentication to verify identity and establish trust securely.
4. Identity Assertion Issued
After successful authentication, the identity provider securely sends a signed identity assertion or token back to the service provider.
5. Access Granted
The service provider validates the assertion, establishes a session, and grants appropriate access in accordance with authorization policies and user attributes.
This flow ensures credentials are never shared across applications, significantly reducing security risks.
Common Federated Identity Standards
Federated identity relies on widely accepted industry standards to ensure interoperability:
1. Security Assertion Markup Language (SAML)
An XML-based standard enabling secure exchange of authentication and authorization data, widely adopted for enterprise single sign-on implementations.
2. OAuth 2.0
An authorization framework allowing applications to access user resources securely on another service without sharing user credentials directly.
3. OpenID Connect (OIDC)
Based on OAuth 2.0, this identity layer offers standardized profile data, user identity verification, and authentication.
4. WS-Federation
An XML-based federated identity protocol primarily used in legacy enterprise systems for authentication and trust-based access management.
Use Cases of Federated Identity
Below are common real-world scenarios where federated identity simplifies access management while improving security and user experience.
1. Enterprise Single Sign-On (SSO)
Employees log in just once to safely use all company systems, cloud apps, and partner tools. They don’t have to enter their username and password again for each service.
2. Cloud and SaaS Access
Companies use federated identity to connect cloud apps (SaaS) so that employees can log in once, follow the same access rules everywhere, and make it easier to manage user accounts.
3. Business-to-Business (B2B) Collaboration
Federated identity enables partners and vendors to access shared systems using their existing credentials, eliminating the need to create and manage separate accounts.
4. Social Login
Users authenticate using their existing Google or Microsoft identities, simplifying registration and improving the user experience across applications.
5. Government and Education Systems
Citizens or students can use a single trusted digital identity to securely access multiple government services or educational platforms seamlessly.
Advantages of Federated Identity
Below are the advantages organizations gain by implementing federated identity across applications and platforms.
1. Improved User Experience
Single sign-on minimizes login fatigue, reduces password confusion, and allows users to access multiple applications seamlessly with a single set of credentials.
2. Enhanced Security
Centralized authentication enforces consistent security policies, supports strong authentication methods, and significantly reduces password exposure.
3. Reduced IT Overhead
Federated identity eliminates the need to manage multiple user directories, reducing administrative effort, infrastructure costs, and the ongoing complexity of identity management.
4. Faster Onboarding and Offboarding
Centralized access provisioning enables quick user onboarding and offboarding, improving operational efficiency, security, and regulatory compliance.
5. Scalability and Flexibility
Federated identity supports easy integration of new applications, partners, and cloud services as organizational needs grow.
Limitations of Federated Identity
Despite its benefits, federated identity introduces limitations that organizations must address to ensure secure and effective implementation.
1. Trust Management Complexity
Managing trust relationships across multiple organizations requires strong governance, clear policies, ongoing coordination, and regular security reviews.
2. Dependency on Identity Provider
Service availability depends on the identity provider, so outages can prevent user authentication and disrupt access to multiple applications.
3. Integration Effort
Legacy systems often need customization, upgrades, or middleware to support federated identity standards and modern authentication protocols.
4. Privacy Concerns
Excessive sharing of identity data between providers can create privacy risks, regulatory compliance challenges, and potential issues with user consent.
Real-World Examples
The following examples illustrate how federated identity is applied across enterprise, consumer, and cloud environments.
1. Enterprise Workforce Access
A multinational company uses a centralized identity platform, such as Okta, to enable employees to securely access internal tools, cloud services, and partner systems.
2. Social Login for Applications
An e-commerce website allows users to sign in with their Google or Microsoft accounts, reducing friction and increasing conversion rates.
3. Cloud Infrastructure Access
Organizations integrate federated identity with cloud providers so developers authenticate using corporate credentials instead of cloud-specific accounts.
Federated Identity Architecture Components
Below are the core architectural components that work together to enable secure, scalable, and trusted federated identity implementations.
1. Authentication Services
Authentication services verify user credentials using passwords, biometrics, or multi-factor methods to confirm identity before granting access.
2. Directory Services
Directory services store and manage user identities, attributes, roles, and group memberships used during authentication and authorization decisions.
3. Token Issuance and Validation
Token services generate, sign, and validate security tokens or assertions exchanged between identity providers and service providers.
4. Policy Enforcement Points
Policy enforcement points evaluate access requests against defined security policies and permissions before allowing resource access.
5. Audit and Logging Systems
Audit and logging systems keep a record of what happens in a system so it can be checked later.
Security Best Practices for Federated Identity
Following these best practices helps organizations strengthen federated identity security while reducing risks and maintaining compliance.
1. Enforce Multi-Factor Authentication
Enforce multi-factor authentication at the identity provider to strengthen security, reduce the risk of credential compromise, and protect federated access.
2. Use Short-Lived Tokens
Use short-lived tokens with strong signing algorithms to minimize exposure, prevent replay attacks, and limit the impact of token leakage.
3. Review Trust Relationships Regularly
Regularly review trust relationships and access policies to ensure alignment with security requirements and remove outdated or unnecessary permissions.
4. Monitor Authentication Logs
Continuously monitor authentication logs to detect anomalies, suspicious behavior, and potential security incidents across federated environments.
5. Apply Least-Privilege Access
Implement least-privilege access controls so users receive only the permissions they need, reducing the attack surface and limiting potential damage.
Final Thoughts
Federated identity transforms how users authenticate and access digital services by replacing fragmented credential systems with a trusted, centralized identity verification system. It enhances security, improves user experience, and enables seamless collaboration across platforms and organizations. As digital ecosystems grow more complex, federated identity will remain a critical pillar of modern identity and access management strategies.
Frequently Asked Questions (FAQs)
Q1. Is federated identity the same as single sign-on?
Answer: No. Single sign-on is a user experience feature, while federated identity is the underlying trust and identity-sharing architecture that enables SSO across domains.
Q2. Does federated identity store user passwords?
Answer: No. Credentials remain with the identity provider and are not shared with service providers.
Q3. Is federated identity secure?
Answer: Yes, when implemented correctly with strong authentication, encryption, and governance controls.
Q4. Can federated identity work across organizations?
Answer: Yes. It is specifically designed to enable secure access across organizational boundaries.
Recommended Articles
We hope that this EDUCBA information on “Federated Identity” was beneficial to you. You can view EDUCBA’s recommended articles for more information.
