What is Cyberwarfare?
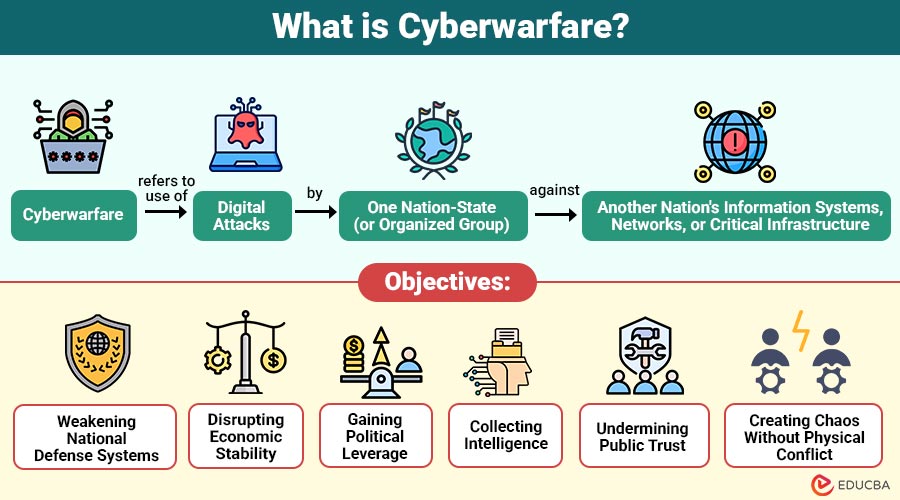
Cyberwarfare refers to use of digital attacks by one nation-state (or organized group) against another nation’s information systems, networks, or critical infrastructure. These attacks are often politically or militarily motivated and aim to disrupt, damage, or gain a strategic advantage.
Unlike traditional warfare, cyberwarfare:
- Does not require physical invasion
- Can be conducted remotely
- Often operates in secrecy
- May not clearly identify the attacker
It blends elements of cybercrime, espionage, and military operations into a new domain of conflict—commonly referred to as the “fifth domain of warfare” after land, sea, air, and space.
Table of Contents:
- Meaning
- Working
- Types
- Objectives
- Real-World Examples
- Impact
- Defensive Measures Against CyberWarfare
- How Can Individuals Stay Safe?
Key Takeaways:
- Cyberwarfare enables nations to conduct strategic digital attacks remotely, disrupting infrastructure without traditional military confrontation.
- It combines espionage, sabotage, misinformation, and economic disruption to achieve political or military objectives.
- Strong cybersecurity frameworks, international cooperation, and individual digital hygiene are essential defenses against evolving cyber threats.
- Cyberwarfare blurs the boundaries between war and peace, making attribution difficult and escalating global geopolitical tensions.
How Does Cyberwarfare Work?
Cyberwarfare involves coordinated digital operations designed to infiltrate and exploit vulnerabilities in target systems. The process generally includes:
1. Reconnaissance
Attackers collect intelligence about networks, employees, software vulnerabilities, configurations, and security defenses before launching targeted cyber operations.
2. Infiltration
Malware, phishing emails, or zero-day exploits are deployed to penetrate systems and gain initial unauthorized access.
3. Establishing Control
Attackers escalate privileges, move laterally across networks, install backdoors, and maintain persistent access within compromised systems.
4. Execution
The primary objective is executed, including data theft, infrastructure sabotage, service disruption, or coordinated misinformation campaigns.
5. Covering Tracks
Attackers delete logs, modify records, and use encryption and anonymization techniques to conceal identity and evade detection.
Types of Cyberwarfare Attacks
Cyberwarfare includes multiple attack categories, each targeting different aspects of national security.
1. Distributed Denial-of-Service (DDoS) Attacks
Attackers flood servers with excessive traffic, overwhelming systems and disrupting government, banking, or critical online services.
2. Malware and Ransomware
Malicious software infects systems, steals information, encrypts sensitive data, or destroys infrastructure to demand ransom payments.
3. Infrastructure Sabotage
Cyber attackers disrupt power grids, water facilities, transportation networks, and healthcare systems, causing widespread civilian disruption.
4. Cyber Espionage
State-sponsored hackers infiltrate networks to steal classified military, political, economic, or strategic intelligence information.
5. Information Warfare
Digital campaigns spread misinformation, propaganda, and manipulated narratives to influence public opinion and destabilize societies.
6. Election Interference
Hackers target voting systems, political parties, and social platforms to manipulate electoral processes and outcomes.
Objectives of Cyberwarfare
Cyberwarfare is not random hacking—it is strategic. Its objectives may include:
1. Weakening National Defense Systems
Cyber operations target military networks, communication systems, and defense infrastructure to reduce a nation’s operational readiness.
2. Disrupting Economic Stability
Attacks on financial institutions, stock markets, and supply chains destabilize economies and create widespread financial uncertainty.
3. Gaining Political Leverage
Nations use cyber capabilities to pressure rivals, influence negotiations, and assert dominance in geopolitical conflicts.
4. Collecting Intelligence
Cyber espionage gathers sensitive political, military, and economic information to support strategic decision-making advantages.
5. Undermining Public Trust
Disinformation campaigns erode confidence in governments, institutions, media, and democratic processes within targeted societies.
6. Creating Chaos Without Physical Conflict
Cyberwarfare enables disruption and instability without conventional military engagement, avoiding direct physical confrontation.
Real-World Examples
Several incidents highlight how cyberwarfare has reshaped global security.
1. Stuxnet Attack (2010)
The Stuxnet attack (discovered in 2010) targeted Iran’s nuclear program. It reportedly damaged centrifuges at nuclear facilities by manipulating industrial control systems. This marked one of the first known cyber weapons designed to cause physical destruction.
2. Estonia Cyber Attacks (2007)
In 2007, Estonia experienced massive cyberattacks targeting government, media, and banking systems. The incident demonstrated how digital attacks could paralyze a highly digitized nation.
3. NotPetya Attack (2017)
The NotPetya attack first started in Ukraine but quickly spread worldwide. It caused billions of dollars in losses and disrupted large companies, shipping businesses, and global supply chains.
Impact of Cyberwarfare
Here are the major impacts of cyberwarfare on nations, economies, and societies:
1. Economic Damage
Cyber attacks cause massive financial losses, recovery expenses, operational downtime, and long-term economic instability across industries.
2. National Security Risks
Compromised military networks and defense communication systems weaken national security and expose strategic vulnerabilities.
3. Civilian Disruption
Attacks on healthcare, energy grids, and water supply systems directly impact daily civilian life.
4. Psychological Warfare
Disinformation campaigns spread fear, confusion, and mistrust, intensifying social divisions within targeted populations.
5. Global Instability
Cyberwarfare escalates geopolitical tensions, blurring boundaries between conflict and peace among nations worldwide.
Defensive Measures Against Cyberwarfare
Countries and organizations are strengthening cybersecurity defenses through:
1. Advanced Threat Detection
Organizations deploy AI-driven monitoring tools to identify abnormal network activity, detect intrusions early, and respond to threats quickly.
2. Zero-Trust Architecture
Security frameworks make sure every user or device is properly verified. No one can access the system without being regularly checked and approved.
3. Cybersecurity Training
Regular employee training programs reduce phishing risks, strengthen awareness, and improve response to social engineering attacks.
4. International Cooperation
Allied nations collaborate by sharing threat intelligence, coordinating defense strategies, and jointly responding to large-scale cyber incidents.
5. Dedicated Cyber Commands
Governments establish specialized military cyber units to defend infrastructure, conduct operations, and strengthen national digital security.
How Can Individuals Stay Safe?
While cyberwarfare targets nations, individuals can still be indirectly affected. Basic protective measures include:
1. Using Strong, Unique Passwords
Create complex passwords that include letters, numbers, and symbols, and ensure each account uses a unique password.
2. Enabling Multi-Factor Authentication
Turn on multi-factor authentication to hinder unwanted access even in the event that credentials are stolen.
3. Updating Software Regularly
Install software updates promptly to patch security vulnerabilities, fix bugs, and strengthen protection against emerging cyber threats.
4. Avoiding Suspicious Links
Unknown email attachments or links should never be clicked, as they may be phishing attempts or contain malware.
5. Backing Up Important Data
Regularly back up essential files to secure locations to ensure recovery in case of ransomware or a system compromise.
Final Thoughts
Cyberwarfare is a major 21st-century security threat, operating across borders and disrupting nations without the use of traditional weapons. Incidents such as the Stuxnet worm and the NotPetya ransomware demonstrate their global impact. As technology advances, governments and organizations must strengthen cybersecurity frameworks, enhance international cooperation, and uphold ethical standards to remain prepared against evolving threats on the digital battlefield.
Frequently Asked Questions (FAQs)
Q1. Is cyberwarfare considered an act of war?
Answer: It depends on the severity. If a cyberattack causes significant physical or economic damage, it may be treated as an act of war.
Q2. Can cyberwarfare cause physical damage?
Answer: Yes. The Stuxnet attack demonstrated that malware can physically damage industrial equipment.
Q3. Who conducts cyberwarfare?
Answer: Nation-states, intelligence agencies, and military cyber units primarily conduct cyberwarfare operations.
Q4. What industries are most vulnerable to cyberwarfare?
Answer: Critical sectors like energy, healthcare, finance, telecom, transportation, and defense are most vulnerable because attacks on them can seriously disrupt national stability and public safety.
Recommended Articles
We hope that this EDUCBA information on “Cyberwarfare” was beneficial to you. You can view EDUCBA’s recommended articles for more information.

