What Is Chain of Custody?
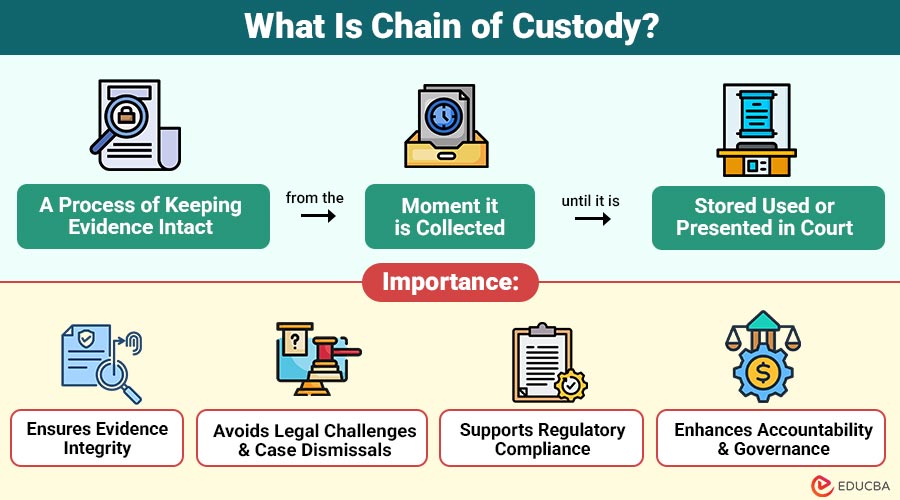
Chain of custody refers to the process of maintaining the integrity of evidence or materials from the moment they are collected until they are used, stored, or presented in court. It ensures that handlers keep the evidence safe, do not tamper with it, and maintain it as the original item.
A well-maintained chain of custody is essential across various fields, such as:
- Criminal justice
- Cybersecurity
- Laboratory testing
- Healthcare and pharmaceuticals
- Environmental compliance
- Corporate investigations
- Supply chain logistics.
By ensuring trust and transparency, the chain of custody strengthens the credibility of evidence and supports fair legal or administrative outcomes.
Table of Contents
- Meaning
- Importance
- Key Elements
- Step-by-Step Process
- Examples
- Digital Evidence
- Common Challenges
- Best Practices
Why Chain of Custody Is Important?
The importance of the chain of custody goes far beyond merely tracking evidence. It is a foundational requirement that protects the integrity of the entire investigation or compliance process.
1. Ensures Evidence Integrity
It guarantees that evidence remains in the same condition as when it was collected. This integrity is crucial for:
- Criminal convictions
- Fraud investigations
- Cybercrime cases
- Scientific research
- Quality control audits.
If anyone compromises the evidence at any point, the entire case can collapse.
2. Avoids Legal Challenges and Case Dismissals
Courts frequently dismiss evidence when someone breaks the chain of custody. Missing signatures, undocumented transfers, or suspicious gaps in the timeline may lead to:
- Evidence exclusion
- Weakened prosecution
- Loss of credibility
- Acquittals due to reasonable doubt.
A strong chain of custody prevents these issues and protects the legal process.
3. Supports Regulatory Compliance
Industries such as pharmaceuticals, healthcare, food safety, and environmental testing must adhere to stringent regulations. It provides proof that:
- Samples were handled properly
- Testing conditions were controlled
- Protocols were followed
- No tampering or contamination occurred.
Compliance auditors often rely on these logs to verify operational transparency and accountability.
4. Enhances Accountability and Governance
With clear documentation of every person involved, a chain of custody promotes a culture of responsibility. It becomes easier to:
- Trace errors
- Identify unauthorized users
- Detect conflicts of interest
- Assess operational performance.
This makes the chain of custody valuable not only in investigations but also in internal governance and oversight.
Key Elements of a Strong Chain of Custody
A robust system consists of multiple interconnected components. Each component protects evidence integrity and ensures traceability.
1. Unique Identification
Every item must have a unique marker for precise tracking. This can be:
- Barcode labels
- QR codes
- RFID tags
- Microchips
- Serial numbers
- Digital fingerprints or hash values (for digital evidence).
A unique ID eliminates confusion and prevents mix-ups during transfer or examination.
2. Complete Documentation
Documentation is the core of the chain of custody. It should include:
- Detailed item description
- Case information
- Collection details
- Names and signatures of handlers
- Reason for evidence handling
- Seal numbers
- Environmental conditions, if relevant.
The log must be continuous, with no missing entries or inconsistencies.
3. Secure Handling and Packaging
Proper handling practices protect evidence from:
- Contamination
- Physical damage
- Data corruption
- Moisture, heat, or exposure.
Different types of evidence require specialized containers, such as evidence bags, swab tubes, anti-static bags, vials, or secure digital storage.
4. Controlled Storage
Storage facilities should follow strict controls, such as:
- Restricted access
- Lock-and-key or biometric entry
- Temperature or humidity control
- Digital vaults for electronic files
- Surveillance monitoring.
Secure storage strengthens the chain of custody and prevents unauthorized access.
5. Transparent Transfer Process
Every transfer must be:
- Recorded
- Signed by both parties
- Time-stamped
- Justified with purpose
- Validated against prior logs.
This component ensures an unbroken chain from origin to final use.
The Chain of Custody Process: Step-by-Step
1. Evidence Identification and Collection
At the scene or source, evidence is:
- Identified by trained personnel
- Collected using appropriate tools
- Avoided contamination (using PPE, gloves, swabs, etc.)
- Photographed or recorded before collection
- Immediately placed in suitable packaging.
The first handler becomes responsible for initiating the chain of custody.
2. Labeling and Documentation
Proper labeling includes:
- Item details
- Case number
- Collector’s identity
- Date and time
- Type of evidence
- Location of collection
- Seal numbers.
This first record serves as the basis for all subsequent entries.
3. Evidence Packaging
Different categories need different packing standards:
- Biological samples: sterile, breathable bags, refrigerated
- Digital evidence: anti-static bags, Faraday bags
- Chemical samples: sealed vials
- Weapons or physical items: tamper-proof containers.
Packaging must prevent deterioration and ensure compliance with the chain of custody.
4. Secure Storage
The team stores the evidence in a secure facility after packaging it. This includes:
- Evidence lockers
- Freezers for biological materials
- Digital forensic labs
- Temperature-controlled vaults.
Logs must clearly show who accessed the storage and why.
5. Transfers and Handoffs
Every handoff must follow strict chain of custody protocols:
- Signature of the releasing person
- Signature of the receiving person
- Time and date of handoff
- Purpose of the transfer
- Condition of the evidence.
This ensures transparency and prevents disputes.
6. Examination and Analysis
During analysis:
- Analysts open the evidence under controlled conditions
- Analysts log every action taken
- Digital devices may undergo imaging or cloning
- Laboratory instruments may record testing parameters.
After examination, evidence is resealed with new tags and documented.
7. Final Storage or Presentation
After all tests:
- The team returns the evidence to secure storage
- Or moved directly to court
- Or used in administrative hearings
- Or archived for long-term retention.
The final resolution maintains the chain’s integrity.
Examples of Chain of Custody
1. Criminal Investigations
Examples include:
- DNA samples collected from a crime scene
- Weapons or tools recovered
- Documents seized during a raid
- Digital devices like phones or laptops.
The chain of custody ensures that the evidence presented in court is authentic and reliable.
2. Digital Forensics
Digital chain of custody requires:
- Imaging of hard drives
- Hash verification
- Encrypted storage
- Access logs
- Forensic workstations.
This guarantees data integrity during cybercrime investigations.
3. Environmental Testing
Soil, water, air, or chemical samples require:
- Temperature control
- Sampling protocols
- Hazard labeling
- Logging each transfer between labs.
Government agencies rely on a chain of custody documentation for regulatory enforcement.
4. Logistics & Supply Chain Management
Businesses use a chain of custody to track:
- Pharmaceuticals
- High-value items
- Hazardous materials
- Perishable goods
- Customs documentation.
This ensures authenticity, safety, and compliance.
Chain of Custody in Digital Evidence
The digital chain of custody is becoming increasingly important as cybercrime rates rise and investigations increasingly rely on data.
Key components include:
- Hashing to verify data integrity
- Write-blockers to prevent overwriting
- Encrypted digital vaults
- Access logs
- Metadata preservation
- Blockchain-based tracking systems.
Even a minor alteration in digital evidence can render it legally invalid, making the digital chain of custody critical.
Common Challenges in Maintaining Chain of Custody
1. Human Error
Examples:
- Mislabeling evidence
- Forgetting signatures
- Improper packaging
- Documentation gaps.
Training and digital systems can help reduce these mistakes.
2. Poor Infrastructure
Outdated storage facilities or manual documentation can compromise the chain of custody.
3. Insufficient Training
Personnel who lack knowledge of the chain of custody may unintentionally break procedures.
4. Unauthorized Access
Improper access controls make evidence vulnerable to tampering.
5. Technical Limitations
Lack of:
- Tracking tools
- Surveillance systems
- Audit trails
- Digital evidence tools.
Can weaken the process.
Best Practices to Strengthen the Chain of Custody
1. Implement Digital Tracking Systems
Use:
- RFID
- QR codes
- Cloud logs
- Blockchain records.
Digital tracking reduces errors and enhances transparency.
2. Conduct Regular Training
Personnel must be trained in:
- Packaging
- Labeling
- Documentation
- Legal requirements
- Digital evidence handling.
3. Standardize Procedures
Create and follow strict protocols, SOPs, and checklists.
4. Limit Access
Use:
- Biometric access
- Time-stamped entry logs
- Two-person rule in sensitive areas.
5. Perform Periodic Audits
Audits help identify inconsistencies early and improve the chain of custody process.
6. Maintain Redundant Documentation
Maintain duplicate logs (both physical and digital) to prevent loss or manipulation.
Final Thoughts
A proper chain of custody is the backbone of trustworthy investigations, credible evidence management, regulatory compliance, and strong forensic practices. Whether handling digital data, physical samples, or high-value materials, maintaining a transparent, unbroken chain of custody ensures accuracy, integrity, and legal admissibility.
By adopting digital tracking, utilizing secure storage, and adhering to standardized procedures, organizations can enhance their chain of custody framework and mitigate risks.
Frequently Asked Questions (FAQs)
Q1. What is the difference between chain of custody and evidence management?
Answer: Chain of custody refers to the documented process of tracking evidence from the time it is collected until it is used or presented in court. Evidence management encompasses the broader practice of storing, handling, and organizing evidence, including adherence to chain of custody procedures.
Q2. How long should the chain of custody records be maintained?
Answer: Evidence handlers should keep records for as long as they require the evidence for legal, regulatory, or organizational purposes. In some cases, this could be several years or even indefinitely, depending on jurisdiction and industry requirements.
Q3. How do digital tools improve the chain of custody?
Answer: Digital tools such as barcodes, RFID, cloud-based logs, and blockchain enhance tracking, reduce human errors, provide real-time monitoring, and create immutable records of every transfer or handling.
Q4. What is a tamper-evident seal, and why is it important?
Answer: A tamper-evident seal is a physical or digital security mechanism that shows if evidence has been accessed or altered without authorization. The process ensures that handlers maintain the integrity of the evidence throughout the chain of custody.
Q5. Is a chain of custody required for internal audits and investigations?
Answer: Yes. Organizations use chain of custody procedures not only for legal cases but also for internal audits, compliance checks, fraud investigations, and corporate governance to ensure transparency and accountability.
Q6. How is a chain of custody verified?
Answer: Investigators verify the evidence by reviewing logs, signatures, timestamps, digital hash values, seal numbers, and audit trails. Regular audits, system checks, and compliance reviews also help ensure accuracy and reliability.
Recommended Articles
We hope this in-depth article on the chain of custody helps you understand its meaning, process, and importance. Explore related articles to dive deeper into forensic procedures, compliance frameworks, and evidence management best practices.
