Updated April 6, 2023

Introduction to Ansible Firewalld
In Ansible, we have many modules that provide us the ability to perform operational work on remote hosts. Especially, operations which are to be done on Linux remote hosts. One such module is named firewalld, which is used to manage firewall rules of Linux systems. In this topic, we are going to learn about Ansible Firewalld.
As we know that Linux systems can have a firewalld daemon that is used to allow/block access to/from services, networks, and ports by updating running or permanent firewall rules on the machine via firewall-cmd utility. The same is managed by Ansible using the firewalld module.
Explaining the Ansible Firewalld
Ansible firewalld is the module that is used to update firewall rules on remote hosts. The remote hosts are the Linux machines here. Ports can be TCP or UDP, which can be enabled or disabled. Similarly, services can be allowed or blocked.
We should note below points while working with Ansible firewalld module: –
- As per the latest Ansible firewalld module, the firewalld version on the hosts, where firewall rules will be modified, should have equal to or greater than 2.11.
- This module is not tested in Debian based
- Requires python2 bindings of firewalld. Where python2 bindings are not available, python3 bindings can be used but we must set ansible_python_interpreter to python3 interpreter path and install python3
- There is a known limitation in Ansible firewalld due to which zone transactions must explicitly be permanent. This also means that when we add a zone and want to perform immediate actions on it, we need to reload the firewalld service. But take care while doing that because reloading firewalld will undo all non-permanent actions performed
- This module is not guaranteed to have backward
Along with the above points, we should also know below terminologies which are heavily used in firewalld.
- Zone: Zone is a logical network location which can be arbitrary but can be defined in terms of the network from which traffic will originate, or a location to which your local network interface is connected.
- Services: Services are the series of ports and protocol combination which works as the socket, that our host is listening on, which then can be placed in one or more
- Ports: These are the logical constructs which are representing a service endpoint
How Does Ansible Firewalld Works?
Ansible Firewall has below available parameters and their respective acceptable values. Using the combination of these we can fulfill our requirements regarding modifying firewall rules on remote hosts, But we should always consider planning and all points discussed in the previous section before making any changes to target systems, also take the backup of rules before changing anything is also recommended.
Because handling rules in an ad hoc way will end up in a mess and we need to spend hours and network support to identify the problematic parts in our firewall rules.
- icmp_block: The icmp block we like to remove or add from or to a zone in firewall rules
- immediate: if the permanent parameter is used, should this be applied
- interface: The interface we like to remove or add to or from a zone in firewall rules
- permanent: Should the configuration be in permanent rule, which persists across reboots or in running configuration temporarily. When this is “no”, then by default immediate is “yes”.
Acceptable values are either “yes” or “no”.
1. port: Name or port or port range to remove or add to or from firewalld. When giving ranges, it must be in the form of PORT/PROTOCOL or PORT-PORT/PROTOCOL for port
2. rich_rule: rich rule to add or remove to or from
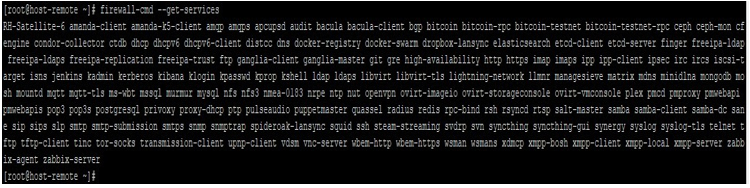
3. service: The service which needs to be added or removed to or from firewalld. The service must be listed in the output of the “firewall-cmd –get-services” command on remote
4. source: The source network you would like to be removed or added to or from in firewalld rules.
5. state: Enable or disable a setting. Below are acceptable values from which present and absent
are used in case of zone level operation.
- absent
- present
- enabled
- disabled
6. timeout: The time for which rule should be in effect when set as non-permanent
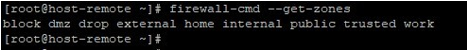
7. zone: The firewall zone to be added or removed. The public is default zone from upstream but this can be configured. Some out of box defaults are block, DMZ, external, internal, trusted, work. This list can be extended based on a per system
Example of Ansible Firewalld
Now by using examples, we will try to learn about Ansible firewalld, which you might have to use in day to day operations. We will take some examples, but before going there, we first understand our lab, we used for testing purpose.
Here we have an Ansible control server named ansible-controller and one remote host named host- remote. We will create playbooks and run Ansible commands on the ansible-controller node and see the results on the remote host.
Also, on the remote host, below is the current status of firewalld.
firewall-cmd --state
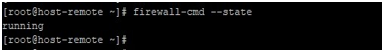
firewall-cmd --get-services
firewall-cmd --get-zone
![]()
firewall-cmd --get-zones
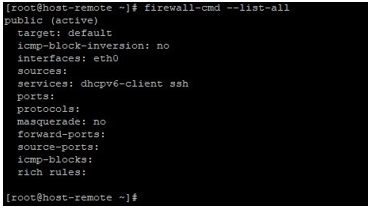
firewall-cmd --list-all
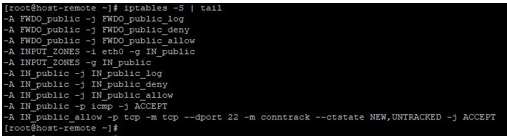
iptable –S | tail
- In this example, we will set https service permanently enabled on the remote host.
- We will use a playbook with below content: –
---
- hosts: all tasks:
- name: here we enable http in firewall rules firewalld:
service: http state: enabled permanent: yes
When we execute it like below we get below output: –
ansible-playbook ansible_firewalld_enable_service.yaml
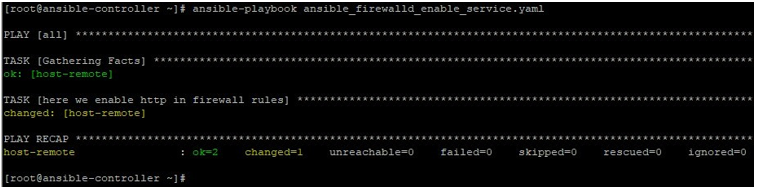
When checking in the remote host that which service is in the open list. We can see that under services we have now http listed.
firewall-cmd --list-all

- In this example, we will see how to enable a port in remote host, for this we have a playbook like below content: –
---
- hosts: all tasks:
- name: here we enable 443 port in firewall rules firewalld:
port: 443/tcp state: enabled
After executing it we get below output: –
ansible-playbook ansible_firewalld_disable_port.yaml
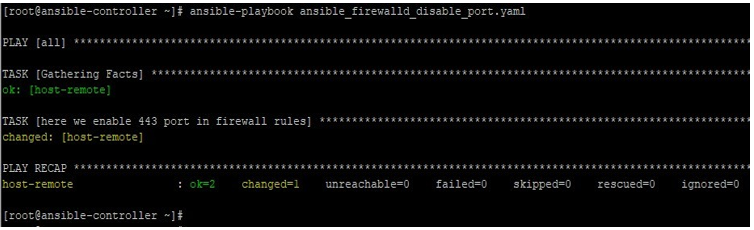
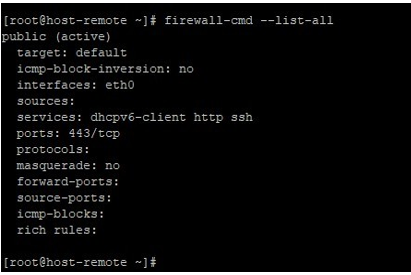
Now checking on the remote host, we will see this port is listed in the output of –list-all now like below, but it was not there previously: –
firewall-cmd --list-all
- In this example, we will enable an ip range for a zone, for this we have a playbook like below, Note here that as we are doing a zone related transaction so for this to work we need to make it permanent and also immediately reload firewalld on the remote host, like below: –
---
hosts: all tasks:
name: here we enable a network for a zone in firewall rules firewalld:
source: 10.10.10.10/24 zone: internal
state: enabled permanent: yes
name: we have to reload firewalld else zone transactions will not be realised command: firewall-cmd --reload
After executing this playbook we get the below output: –
ansible-playbook ansible_firewalld_enable_source_network.yaml
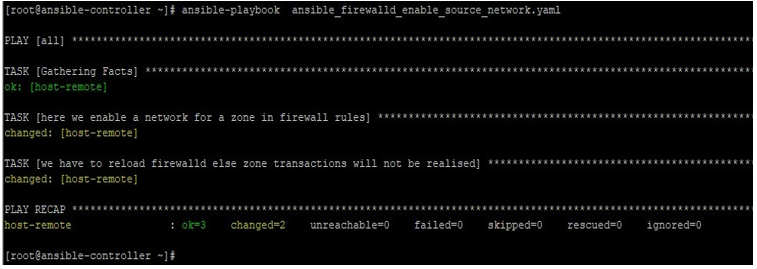
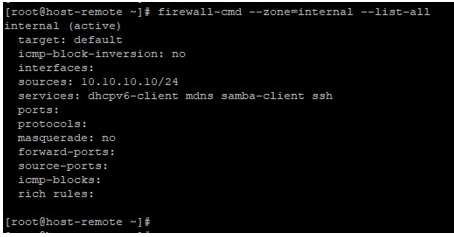
On the remote host, we can see that the mentioned network is listed on the concerned zone’s allowed list
firewall-cmd --zone=internal --list-all
Conclusion
As we have seen that Ansible firewalld is a very powerful module which can be very useful if you have supported network and your remote hosts are supportable in all ways. But points to note that it is not an easy task to have a track of all the firewall rule, especially when we have permanent and non- permanent rules. So that preparation is needed before-hand.
Recommended Articles
This is a guide to Ansible Firewalld. Here we discuss the introduction to Ansible Firewalld along with the working, detailed explanation and respective examples. You may also look at the following articles to learn more –


