Protecting Smart Devices with IoT Security
We are entering an innovative digital era where phones and computers are no longer the only devices connecting us to the world. Smart devices now perform a wide range of tasks from unlocking doors and turning on lights to monitoring security cameras, tracking health, controlling TVs, and even running factories and hospitals. This interconnected world is powered by the Internet of Things (IoT), offering unprecedented convenience and innovative possibilities. While these devices simplify life, they also bring serious security risks. Any poorly protected smart device, from a speaker to a camera, can be accessed by cybercriminals. With many devices poorly secured, always online, and rarely updated, IoT has become a prime target for attacks. With the growing number of connected devices, the question is no longer whether we should protect them it is how quickly we can ensure IoT security. Protecting IoT devices is now essential, not optional.
Why IoT Security Matters Now?
Attackers have realized something simple. Many IoT devices are poorly secured, always on, and everywhere. Recent reports estimate hundreds of thousands of daily IoT attacks, with global IoT hacking attempts in 2025 highlighting the fragile foundation of our connected world. We are not just talking about someone turning your smart bulb on and off.
1. Healthcare: Over 1 million IoT medical devices were recently found exposed online, leaking sensitive patient data, including MRI scans and test results.
2. Industrial Systems: By the end of 2025, more than 200,000 critical devices—including water treatment and fuel monitoring systems are projected to remain exposed to the public internet.
3. Cloud Infrastructure: Microsoft Azure blocked a record-breaking 15.72 Tbps DDoS attack launched by an IoT botnet of around 500,000 compromised devices in November 2025.
Why are IoT Devices so Vulnerable?
Manufacturers often prioritize function and cost over security when building IoT devices. A few recurring problems show up across many brands.
1. Default or Weak Passwords
Many devices ship with simple, factory-set usernames and passwords, and users either do not know or do not bother to change them. Attackers often rely on automated tools to scan the internet and access devices using common default credentials.
2. Lack of Updates
Unlike phones or laptops, many smart devices rarely receive security patches, or users never install them. That means known vulnerabilities remain open for years.
3. Always Connected, Always On
IoT devices often run continuously and stay connected to the internet. For attackers, that is a dream: a huge pool of machines available for exploitation and botnets.
4. Flat Networks
In many homes and businesses, IoT devices sit on the same network as critical servers or personal laptops. One compromised camera or printer can become an entry point to everything else. A Palo Alto Networks analysis recently found that nearly half of network connections between IoT and IT devices involve high-risk IoT equipment, often with poor segmentation.
5. Poor Design and Insecure Defaults
Some devices expose unnecessary services, use outdated encryption (or none at all), and have hard-coded credentials built into firmware. A famous example is the Mirai botnet, which took over hundreds of thousands of IoT devices, mostly by guessing default passwords, and used them to launch massive DDoS attacks.
What is at Risk in Everyday Life?
The impact of poor IoT security is not just technical it is personal and sometimes physical:
1. Cameras and Baby Monitors: Hackers can hijack poorly secured devices, allowing strangers to watch or speak through them.
2. Medical Devices: Connected pumps, monitors, and scanners transmit sensitive data. Exposure or tampering can affect privacy and safety.
3. Industrial Systems: Attackers can weaponize factory sensors, energy systems, and water treatment devices for sabotage, ransomware, or service disruption.
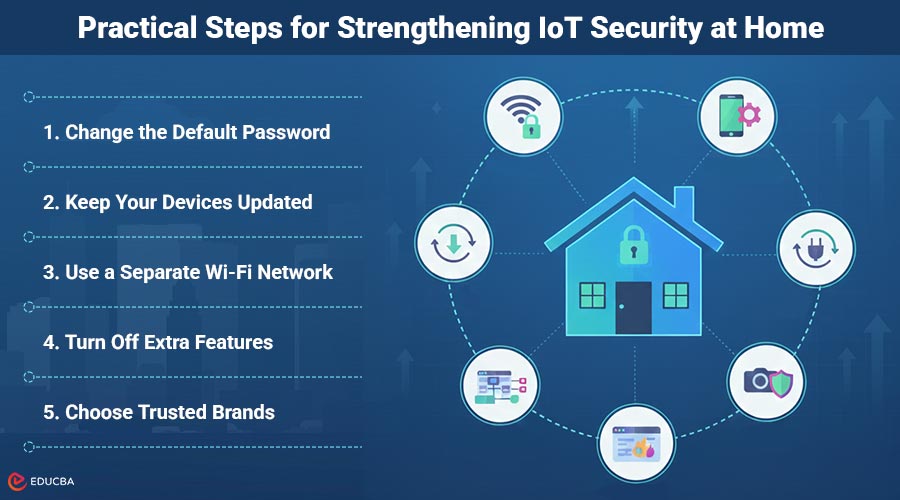
Practical Steps for Strengthening IoT Security at Home
In larger homes or small offices with many connected devices, lightweight ITSM software helps track all connections and alerts users to unusual behavior. Simple steps can reduce the risk of cyberattacks:
1. Change the Default Password
The first thing you should do after setting up any smart device is change the default password. Those factory passwords are easy for hackers to guess and are often the same across devices. Using a strong, unique password stored in a password manager significantly enhances your device’s security.
2. Keep your Devices Updated
Updates are not just about new features; they often fix security problems. Turn on automatic updates if possible, so you do not have to remember. Keeping apps and devices updated helps protect them from known threats.
3. Use a Separate Wi-Fi Network
It is safer to keep your smart devices on a different Wi-Fi network from your personal devices. Most routers let you easily create a guest network. If one smart device gets hacked, this setup prevents access to your laptop or phone.
4. Turn off Extra Features
Many smart devices include features you might never use, each of which can provide an entry point for attackers. Turning off unnecessary features, such as remote access, reduces risk. If you do not need it, disable it.
5. Choose Trusted Brands
Since not all devices prioritize security, selecting brands with strong cybersecurity measures is essential. Even outside IoT, modern platforms now rely on tools like address autocomplete APIs to validate locations, reduce user errors, and ensure accurate device setup, demonstrating that automation and reliability go hand in hand with security.
Look for companies that clearly mention regular updates and strong security features. Spending a little more on a secure device now can prevent bigger issues later.
How IoT Security Will Evolve in the Coming Years?
Finally, governments and business groups are calling for stronger, built-in IoT security, not added on later. In the US, the Cyber Trust Mark label for consumer goods and the IoT Cybersecurity Improvement Act for federal devices are raising the bar for clear and safe design. In Europe, laws like the Cyber Resilience Act aim to hold companies legally responsible for ensuring that connected goods meet security standards and receive updates.
International groups like ETSI, ISO/IEC, and NIST are working to ensure that IoT devices have the same basic security controls and testing methods. These steps would not instantly fix everything, but they send a strong message- IoT that is not safe should no longer be the norm.
Final Thoughts
Smart devices simplify daily tasks such as turning on lights, monitoring security cameras, and operating factory machines. Every connected device becomes a target for hackers when you fail to secure it. Staying secure does not need tech expertise. Simple IoT security measures such as changing default passwords, updating devices, and buying from known brands can help.
As technology advances, security needs to keep pace. Protecting smart devices is just as important as protecting your phone or laptop. Today, staying safe online means protecting all your devices, not just the ones you consider important. A little work now can keep problems from getting worse later.
Recommended Articles
We hope this guide to IoT security helps you protect your smart devices. Check out these recommended articles for more tips and strategies to enhance your device safety.
